New! The Security Ratings report is now the Executive Report. Request your report to see enhanced analysis such as your rating, likelihood of ransomware incidents, and likelihood of data breach incidents.
Bitsight’s View into the NSA’s Top Vulnerabilities
Tags:

In a highly unusual move, the National Security Agency released research on October 20, 2020, highlighting 25 common vulnerabilities that are being actively exploited by Chinese state-sponsored actors. The NSA issued the alert in order to help companies prioritize vulnerability management. Most of the NSA vulnerabilities can be exploited to gain initial access to networks that are directly accessible from the Internet.
Security and risk leaders should act immediately to determine whether their organizations -- and the organizations that comprise their supply chain -- are vulnerable. It is critical to examine the supply chain -- half of Bitsight’s “40 Most Subscribed Entities” have been vulnerable to a NSA-identified Remote Access vulnerability this year.
Summary of Findings
Leveraging our global telemetry, Bitsight is helping organizations gain visibility into some of the most risky vulnerabilities identified by the NSA. We analyzed the security performance records of more than 200,000 global entities across 22 sectors to identify trends across a number of high risk vulnerabilities highlighted in the NSA alert:
- Remote Access vulnerabilities are prevalent across many sectors. Many sectors have a high presence of Remote Access vulnerabilities -- including BlueKeep (CVE-2019-0708), Citrix (CVE-2019-19781), PulseSecure (CVE-2019-11510), and F5 BigIP (CVE-2020-5902).
- Specific sectors are potentially at risk to Active Directory vulnerability. Organizations in the Education, Utilities, Government, and Technology sectors are potentially vulnerable to the Active Directory vulnerability -- Zerologon (CVE-2020-1472). A recent Bitsight assessment found at least 17,000 systems potentially vulnerable.
- Company size matters. The analysis reveals some interesting findings when it comes to the performance of companies measured by employee size. Organizations with greater than 100,000 employees generally demonstrate weaker performance managing Remote Access vulnerabilities compared to all other organizations. This finding highlights the challenges that organizations with large attack surfaces face in managing risks.
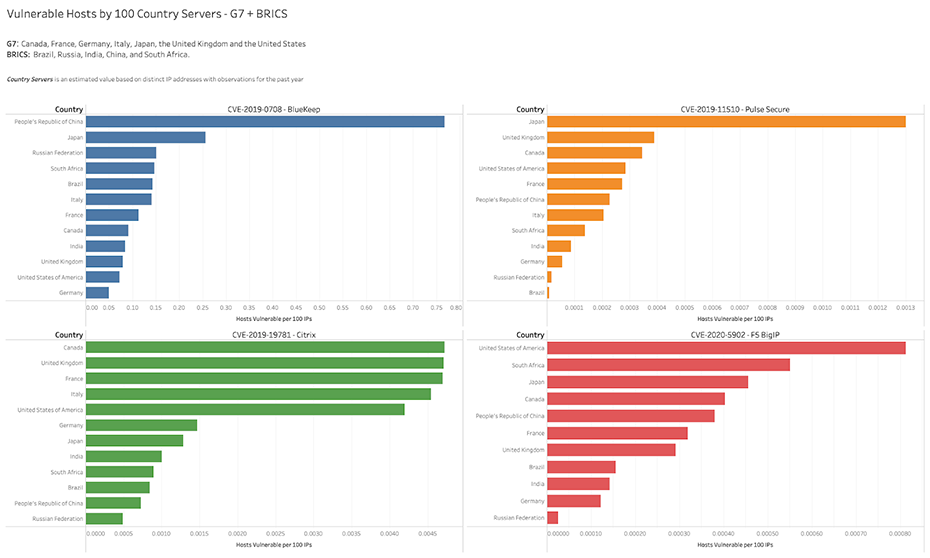
- Performance varies by country. Country rates of vulnerability vary across the four major Remote Access vulnerabilities -- while China has a higher rate of BlueKeep (CVE-2019-0708), the United States has a higher rate of F5 BigIP (CVE-2020-5902) and Citrix (CVE-2019-19781). Japan outpaces all when it comes to PulseSecure (CVE-2019-11510). Vulnerability presence within countries is more likely the cause of technology adoption rather than policy initiatives.
Bitsight’s Visibility into NSA Vulnerabilities by Sector
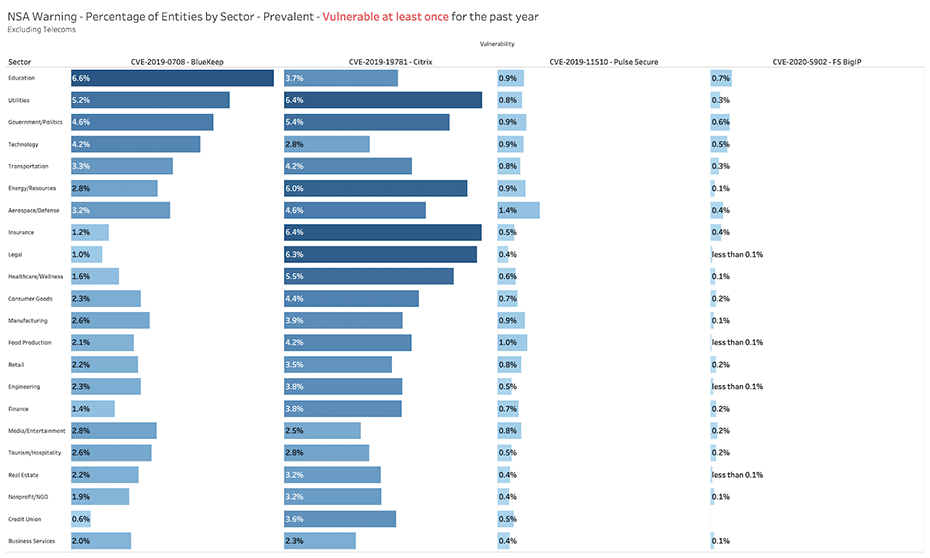
When it comes to managing Remote Access vulnerabilities -- including BlueKeep (CVE-2019-0708), Citrix (CVE-2019-19781), Pulse Secure (CVE-2020-11530), and F5 BigIP (CVE-2020-5902) -- no sector is a particularly strong performer. These vulnerabilities are common across a broad range of sectors.
Table 1: Bitsight View into Four Major Remote Access Vulnerabilities, By Sector
Bitsight is able to identify systems that are potentially vulnerable to the Active Directory vulnerability known as Zerologon (CVE-2020-1472). In October 2020, we were able to identify at least 17,000 systems around the world that are potentially vulnerable to an attack leveraging this vulnerability. In general systems like this should not be exposed outside of the firewall.
Table 2: Bitsight View into Zerologon Vulnerability, By Sector
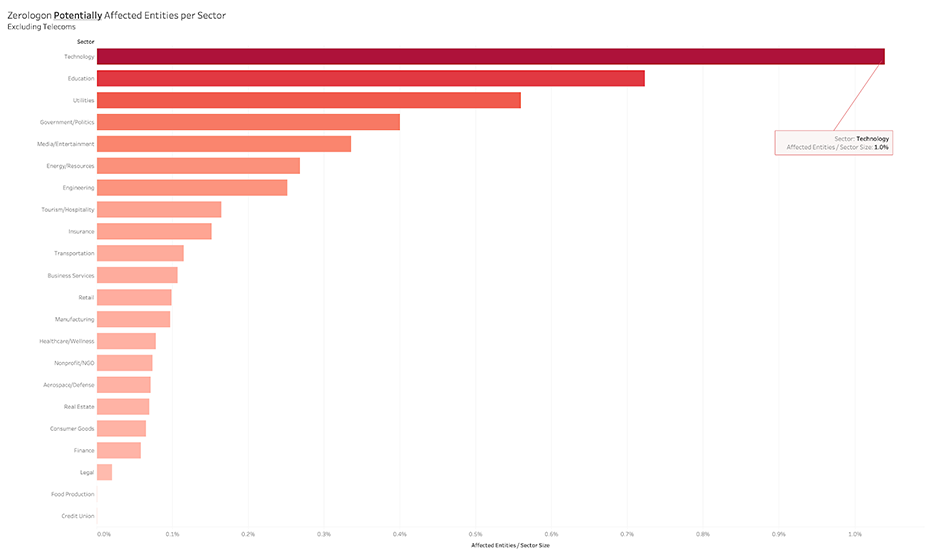
We did not try to directly connect to the Netlogon port on all of these systems, but manual testing on a small subset shows that the Netlogon port is unfiltered in the vast majority of cases.

Check back Monday for our in depth analysis of the Zerologon vulnerability
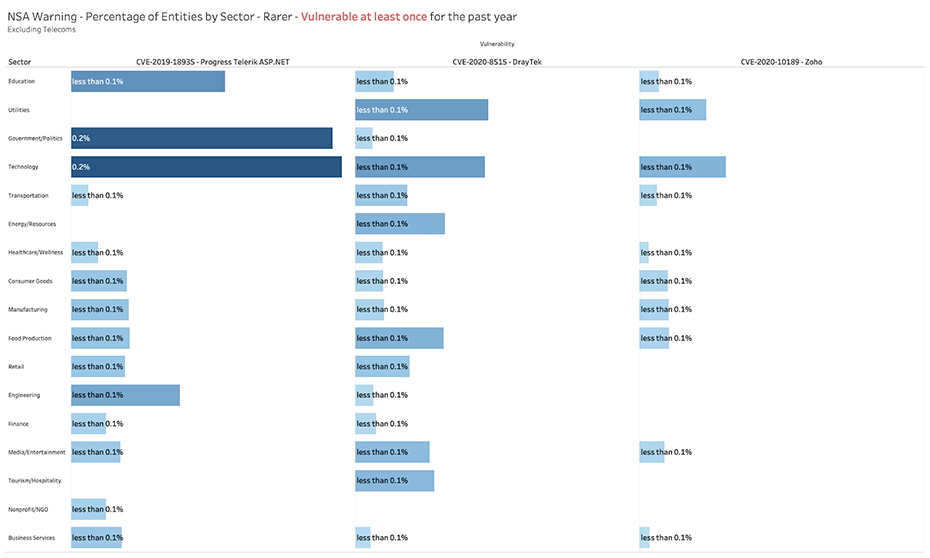
Some of the vulnerabilities identified by the NSA that exploit internal servers or network devices -- including DrayTek (CVE-2020-8515), Zoho (CVE-2020-10189), and Telerik (CVE-2019-18935) -- appear less prevalent around the world:
Table 3: Bitsight View into Additional NSA Vulnerabilities, By Sector
Bitsight’s Visibility into NSA Vulnerabilities by Size of Company
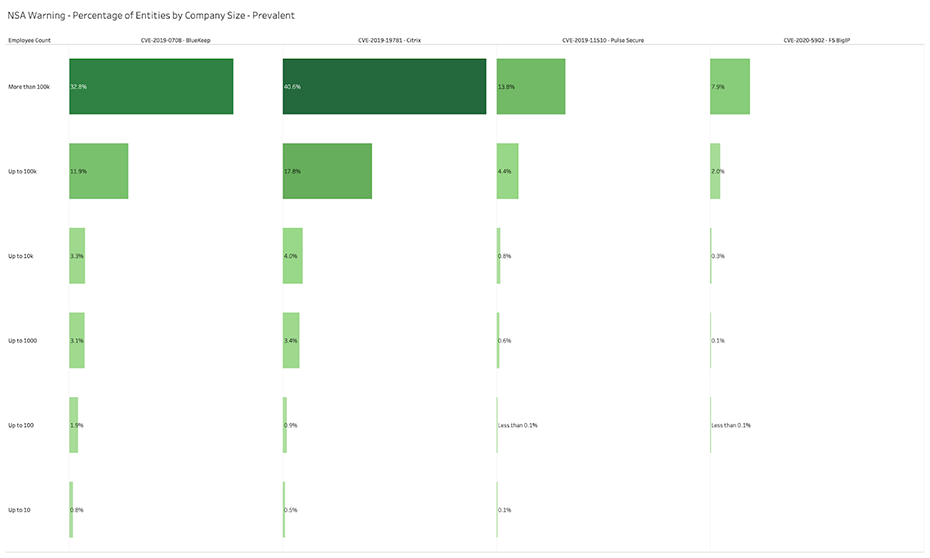
Bitsight observes weaker performance in managing vulnerabilities identified by NSA by organizations with massive numbers of employees (>100,000). These massive companies have larger networks and a larger attack footprint, making vulnerabilities more likely to be exposed.
Table 4: Bitsight View into Four Major Remote Access Vulnerabilities, By Size
Bitsight’s Visibility into NSA Vulnerabilities by Country
An examination of country rates of vulnerability finds different levels of performance across the four major Remote Access vulnerabilities. While China has a higher rate of BlueKeep (CVE-2019-0708), the United States has a higher rate of F5 BigIP (CVE-2020-5902) and Citrix (CVE-2019-19781). Japan outpaces all when it comes to PulseSecure (CVE-2019-11510).
The number of vulnerable systems within these countries is likely dependent on the adoption of certain technologies rather than policy initiatives. For example, the United States is more vulnerable to F5 and Citrix because these technologies are used more frequently in the U.S. than in other countries.
Table 5: Bitsight View into Four Major Remote Access Vulnerabilities, By Country
Next Steps for Security and Risk Professionals
The NSA alert should raise alarms inside organizations around the world and help them prioritize remediation for these critical vulnerabilities. Organizations must act now to gain visibility into these vulnerabilities within their own organization, as well as their supply chain partners. By identifying and mitigating these critical risks across their ecosystem, they can reduce the risk of becoming the next victim of a state-sponsored cyber attack.
To learn how Bitsight can help you manage these and other risks to your organization and your third party ecosystem, contact us for a demo and receive your complimentary vendor portfolio risk report to see where your vendor cyber risks are and how it could affect your cyber risk rating.


