Data Insights on the BlueKeep Vulnerability


On May 14th, Microsoft issued a warning about the BlueKeep vulnerability (CVE-2019-0708) affecting Remote Desktop Services Protocol (RDP), a component common in most versions of Microsoft Windows that allows remote access to its graphical interface. This vulnerability, if exploited by an external attacker, will lead to full system compromise, without requiring any form of authentication or user interaction.
Microsoft has since issued two strongly worded blog posts here and here, warning system owners to patch their systems. In an unusual step, they even provided fixes for operating systems that have long been in “End of Life” unsupported status, namely Windows XP and Windows Server 2003.
Microsoft has made several links between BlueKeep and the EternalBlue vulnerability used by the WannaCry worm several years ago. The comparison between these two vulnerabilities is pertinent, as both can be exploited without user authentication and require no additional interaction. In other words, both are “wormable” vulnerabilities.
Our Insight
Our mission at Bitsight involves collecting externally observable signals that help measure a company’s IT security posture and providing information that organizations need to manage and improve their own security performance and address security issues throughout their extended business ecosystem. In some cases there are vulnerabilities that pose significant risks to an organization which can also be observed externally. We believe that the way companies will handle this issue in the next few weeks can provide valuable insight into their cybersecurity posture. Therefore, since May 31st we have been collecting information about the exposure and vulnerability status of systems vulnerable to BlueKeep.
The Numbers
There are reports of reliable exploits for this vulnerability privately circulating, including unconfirmed reports of an exploit being available for purchase on the darknet as early as September of 2018. One information security professional, Robert Graham, created a tool to check the presence of the vulnerability on any given system, and subsequently performed a full Internet scan to check for exposed vulnerable systems; he identified over 900,000 systems vulnerable to this issue.
We incorporated Robert’s tool into our own Internet scanning platform to continuously monitor for vulnerable systems. The following chart provides the global numbers we obtained for affected systems. We confirm the recently published numbers from Robert, which indicate close to one million vulnerable systems exposed to the Internet. 
Systems with RDP exposed externally with Network Level Authentication (NLA) enabled were not vulnerable to the issue prior to the patch being released and remain protected.
We can also provide the exposure by country. The following chart shows the top 15 countries with the most exposure to this issue, ignoring NLA enabled events. 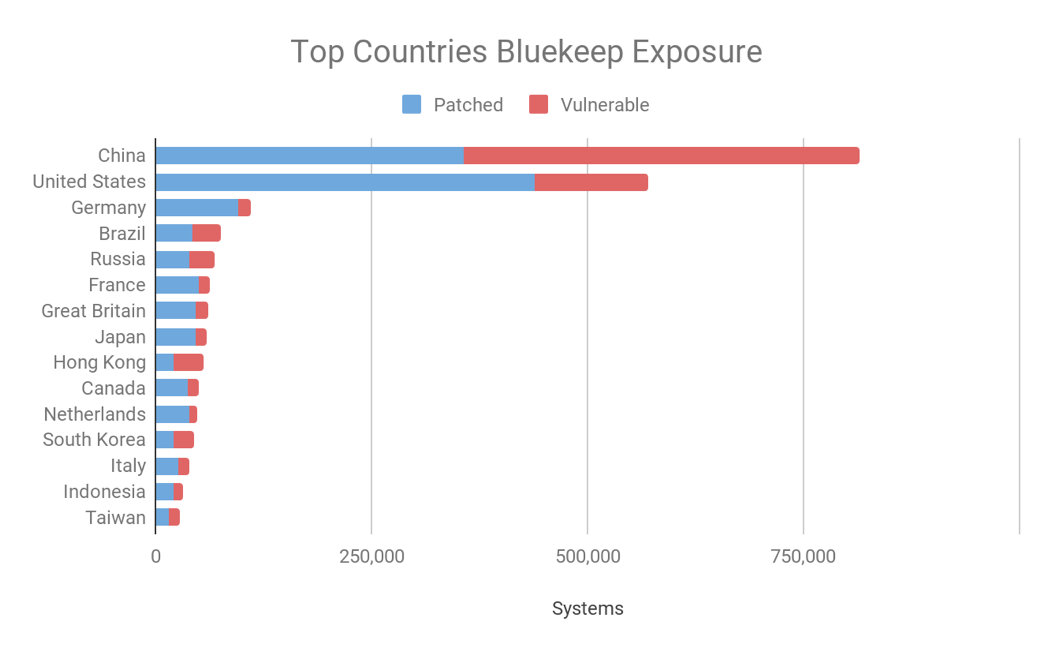
Countries have responded differently to patching their systems, as can be seen in the following graph, where we correlate between number of RDP systems exposed without NLA and ratio of patched systems.
Since countries with very low exposure can have skewed results, we filtered out countries with less than 20,000 exposed RDP hosts.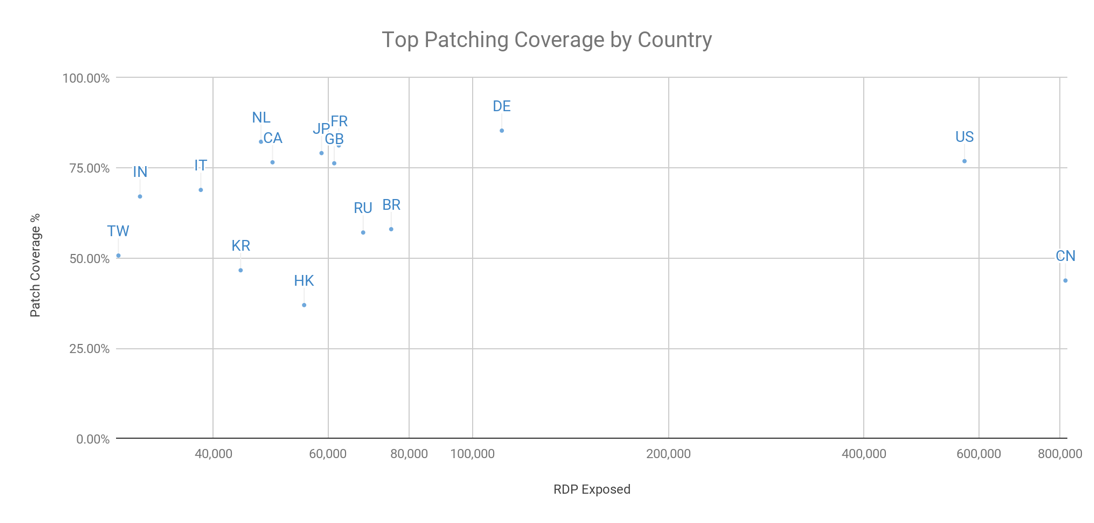 Similarly we can show the exposure to this issue by Industry sector, for all companies in our inventory. The chart below shows the ratio of companies that contain at least one vulnerable system, companies that have patched or are protected by an additional layer of authentication (NLA) as well as companies that do not have RDP exposed. We can see that Telecommunications, Education and Technology companies are the most affected. Telecommunications companies usually host end-customer systems that they cannot upgrade themselves, which may explain the higher ratio for this industry sector.
Similarly we can show the exposure to this issue by Industry sector, for all companies in our inventory. The chart below shows the ratio of companies that contain at least one vulnerable system, companies that have patched or are protected by an additional layer of authentication (NLA) as well as companies that do not have RDP exposed. We can see that Telecommunications, Education and Technology companies are the most affected. Telecommunications companies usually host end-customer systems that they cannot upgrade themselves, which may explain the higher ratio for this industry sector.
EternalBlue versus BlueKeep
Based on the data we collected beginning May 31 and the historical data available from 2017, we can compare the number of exposed systems immediately before each bug was acknowledged and patched by Microsoft.
Note that EternalBlue was the bug used in the WannaCry worm, let loose on the Internet approximately two months after the Microsoft EternalBlue advisory and patch.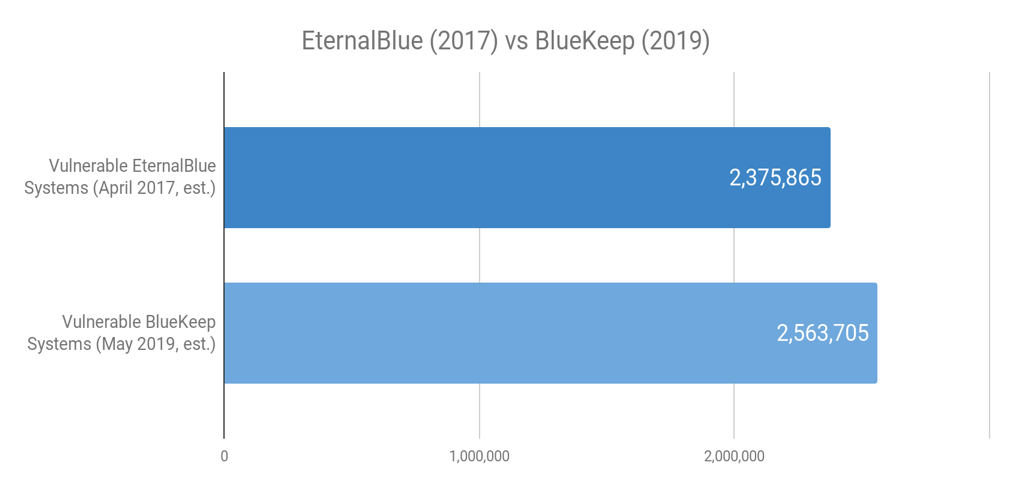
In this graph we are comparing potential exposure around the date both bugs were announced, disregarding patching.
We are estimating potential exposure for EternalBlue by counting the number of SMBv1 hosts exposed on the Internet during April 2017, and for BlueKeep we are counting the number of RDP exposed hosts with NLA disabled during May 2019.
We can see that the situation is very comparable in terms of exposed systems, with BlueKeep having a larger number of exposed systems at the time of bug announcement and patch release.
Regarding exploit availability, the situation is slightly different. In the case of the EternalBlue vulnerability, a reliable exploit was leaked almost simultaneously to the patch being released. With BlueKeep there is no widely available exploit circulating at the time of this writing, but there have been several reports of proof of concept exploits being easily created by reverse engineering the patch.
It will be interesting to understand if the wide availability of a reliable exploit is a differentiating factor regarding the possibility of mass exploitation or a worm being released.
In any case, the destructive potential is clearly similar or worse than WannaCry, especially if patching is not taken seriously.
Individual Companies Affected
Bitsight follows responsible disclosure, and we are committed to never publicly naming specific companies affected by these or other vulnerabilities. The information for affected systems is available in our portal for all rated companies. We provide free access for a limited period of time to all rated companies and will always work with any rated entity to improve the accuracy of its rating and the information we base our ratings on, regardless of whether it is a paying customer.
What Comes Next
Having vulnerabilities is an inevitability of running a modern business. How companies manage and respond to these vulnerabilities is the distinguishing factor for security resilient businesses. We measure this particular data as part of our Patching Cadence risk vector, in which we negatively impact ratings for companies with vulnerabilities that remain unresolved for a long period of time, and conversely positively impact the rating of companies which quickly respond to these high severity issues.
We will be monitoring how companies will respond to this issue by continuing to observe the patching response and measuring the time each company takes to mitigate this issue. We will update this post with additional relevant data as the situation unfolds.
Customers can access our portal to identify companies in their portfolio that are affected by this vulnerability by choosing “CVE-2019-0708” under the “Vulnerability” portfolio filter. Customers can also access individual events by accessing the “Patching Cadence” risk vector under the “Diligence” risk category.
Companies should also follow these recommendations, originally provided by the National Security Agency:
In order to increase resilience against this threat while large networks patch and upgrade, there are additional measures that can be taken:
- Block TCP Port 3389 at your firewalls, especially any perimeter firewalls exposed to the internet. This port is used in RDP protocol and will block attempts to establish a connection.
- Enable Network Level Authentication. This security improvement requires attackers to have valid credentials to perform remote code authentication.
- Disable remote Desktop Services if they are not required. Disabling unused and unneeded services helps reduce exposure to security vulnerabilities overall and is a best practice even without the BlueKeep threat.
Authors: Luis Grangeia, Tiago Martins, Dan Dahlberg
Visit our BlueKeep Resource Center to stay up to date on the latest news & Bitsight research on the BlueKeep vulnerability and learn how you can protect yourself and your supply chain from this and other emerging risks.


