Request your free custom report and see how you can start reducing your cyber risk exposure across your digital ecosystem: cloud assets across all geos & subsidiaries; discover shadow IT; security risk findings; and more!
Attack Vector vs. Attack Surface: What is the Difference?
The terms attack vector and attack surface are often used interchangeably. But there are very clear differences between both terms. Understanding those differences can help your organization maintain a strong security posture. In this blog, we explore attack vectors vs. the attack surface and recommend strategies to account for both in your cybersecurity program.
The Difference Between Attack Vectors & Attack Surface
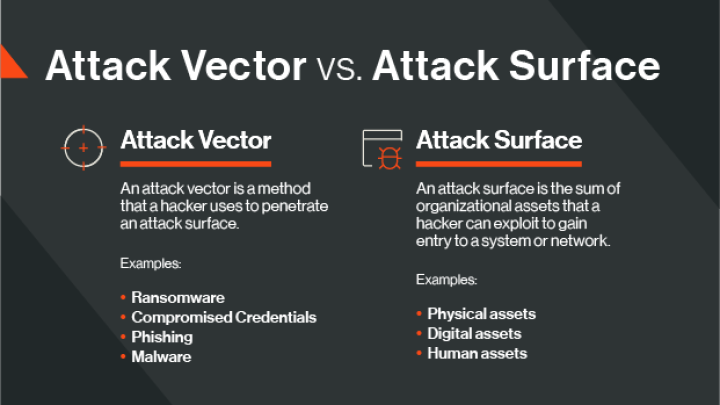
An attack vector is a method that a hacker uses to penetrate an attack surface. An attack vector takes many forms, including ransomware, compromised credentials, phishing, and malware.
An attack surface is the sum of organizational assets that a hacker can exploit to gain entry to a system or network. For many companies, the attack surface can be vast and includes physical, digital, and human assets.
Different Types of Attack Vectors
Now, let’s look at common attack vectors that can be used to breach your attack surface and how to defend against them.
Malware
Malware is a term for any form of software, including ransomware or a Trojan horse, that looks like a legitimate file but executes malicious code when the user opens or downloads it.
Ransomware
Ransomware is a form of malware that encrypts data on a victim’s computer and blocks the owner from accessing it in exchange for a ransom. Once payment is received, access to the data is restored.
Bitsight research suggests that poor security hygiene and the presence of vulnerabilities increase the likelihood of ransomware attacks. Learn more about the report’s findings and how you can lower the odds of being the next ransomware victim in our blog.
Misconfigured Systems
The misconfiguration of systems, particularly in the cloud, is a leading cause of data breaches and data loss. The massive Capital One data breach, for example, was the result of a misconfigured web application firewall.
There is also a direct correlation between misconfigured systems and ransomware attacks. For instance, Bitsight analysis found that organizations with a C grade or lower in TLS/SSL configurations are nearly four times more likely to be ransomware victims.
Unpatched Systems
New vulnerabilities arise every day and if you don’t monitor for unpatched systems or apply a patch expeditiously, hackers will easily exploit them. Indeed, Bitsight’s researchers found that organizations with a patching cadence of D or F were more than seven times more likely to experience a ransomware event compared to those with an A grade.
Compromised Credentials
Compromised usernames and passwords are widely available on the dark web and can give hackers unprecedented access to your network. Consider investing in tools that monitor for exposed credentials resulting from publicly disclosed breaches so that you can act quickly.
Phishing
Phishing is a form of social engineering that occurs when a bad actor impersonates a legitimate person or organization—typically via email—and asks the recipient to take an action that would give the phisher access to critical data or systems.

Different Types of Attack Surfaces
Let’s look at each element of the broader attack surface and the ways you can reduce risk exposure across each.
1. Physical Attack Surface
The physical attack surface of your organization is its four walls—offices, data centers, or a server room. Once an attacker gains entry to a building or space, they can carry out malicious cyber activity on a device. This method is typically exploited by disgruntled employees, intruders, or perpetrators of social engineering attacks.
Attack methods can include installing malicious software on a device, checking for and exposing sensitive data, accessing source code on a machine, and more.
To guard the physical attack surface, implement robust physical security measures, especially where sensitive data is housed, and ensure you have policies to dispose of unused hardware or sensitive paper files.
2. Digital Attack Surface
The digital attack surface encompasses any digital assets accessible via the internet, such as servers, databases, cloud instances, remote machines, shadow IT, and more. It also includes any third-party vendors that handle sensitive data.
Protecting this surface is a challenge. As businesses expand to the cloud and across remote locations, business units, and subsidiaries, hundreds of thousands of digital assets may be vulnerable to attack.
To reduce the risk of a hacker penetrating your digital attack surface, you first need to understand its scope. Use tools like attack surface analytics to gain visibility into digital assets, broken down by cloud provider, geography, and business unit—and the corresponding cyber risk associated with each.
Because threats and vulnerabilities are constantly emerging, make a plan to continuously monitor your digital attack surface for any changes to your security posture. Then apply the same monitoring capability to your vendors so that you can be alerted to cyber risk without the need for costly or time-consuming assessments or audits.
3. Human Attack Surface
Your organization’s employees are its weakest link and the most vulnerable attack surface. Typically, threat actors exploit this weakness through social engineering attacks such as phishing, smishing, and vishing.
Training, exercises, and creating a cyber aware culture in the workplace can help reduce the risk of these attacks. Still, security leaders must better understand their employees’ psychological vulnerabilities and mitigate the risk associated with these behaviors. Check out this blog for more insight.
Protect Your Attack Surface and Address Attack Vectors With Bitsight
To address these attack vectors, regularly review your security program performance. Bitsight can help. Use Bitsight Security Ratings to evaluate how your security posture is changing over time (ratings are updated daily) and make better cybersecurity decisions, faster.
An attack surface is the sum of all the physical and digital points within an IT network that malicious actors may attack as they try to gain access to a company’s system.
Attack surface analytics are a security solution that provides visibility into the size and nature of an organization’s attack surface, as well as the risks and vulnerabilities within the attack surface.
Attack surface monitoring is the practice of continually gauging the size and composition of a company’s attack surface and evaluating the risks within it.


