Analyzing 3 Major Data Breaches Of 2015
Tags:

Some of the largest data breaches in history happened in 2015. Notable breaches on that list include PNI Digital Media, Anthem Insurance, and The Office Of Personnel Management. These three weren’t necessarily the top data breaches of last year in terms of size or impact, but they were important because these organizations were so highly trusted and recognized in their respective industries.
Below, you’ll find details about each of these breaches, followed by our analysis of what you can learn from them.
1. PNI Digital Media
PNI is a third-party photo processing service. In June and July of 2015, attackers breached a number of PNI photo kiosks and installed malware which collected and exfiltrated customer data, resulting in a loss of over 300,000 records. CVS Caremark, Costco, Walmart, and Rite-Aid were among the large corporations affected in this breach.
2. Anthem
In January 2015, medical insurance provider Anthem began notifying 80 million individuals that their records had been compromised in a cyberattack. The hackers may have accessed “names, dates of birth, social security numbers, healthcare ID numbers, home addresses, email addresses, and employment information, including income data.” A number of large organizations submitted data breach documentation due to affected parties in their company, including Bank of the West, American Apparel Inc., McDermott Will & Emery, and Verizon.
3. OPM
In July of 2015, the Office of Personnel Management (OPM) revealed that the records of more than 21.5 million government employees (current and former) were affected in their cyberbreach. This breach was reported to be espionage-related.
Analysis: What Can You Learn From These Breaches (& Beyond)?
It’s easy to gravitate toward learning from these headline-grabbing, worst-case breaches. But using only these breaches to learn how to defend your organization would be like basing your worry about how you’re going to die by reading only stories about grisly murders. You would have a skewed perception and a biased opinion of what may go wrong and what you should be thinking about.
That being said, there are a number of things you can learn not only from these three major breaches but also the thousands of smaller breaches that happen on a daily basis.
1. It’s all about preparation and detection.
The following log scale looks at the number of records compromised in 2015 data breaches. As you can see, it peaks around 1,000 records:
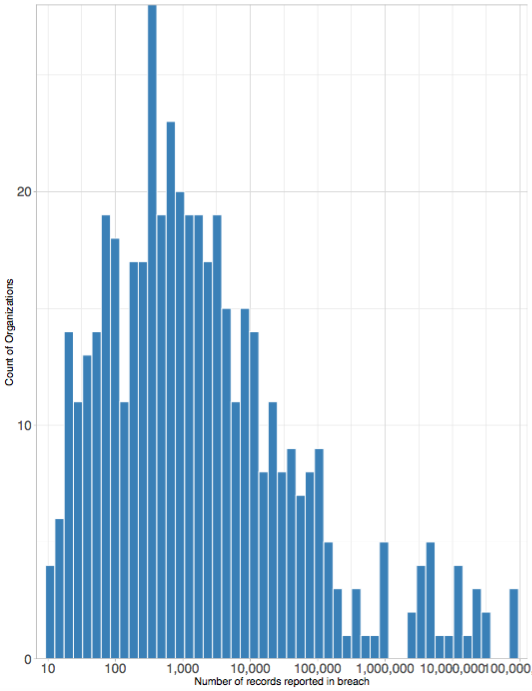
This goes to show how rare breaches that compromise millions of records truly are. If you are breached, you’re far more likely to lose 5,000 records than 500,000. In any case, it all boils down to preparation. If you experience a breach, you’ll have a certain number of fixed costs, regardless of the size. There will be legal or PR issues to handle, because you’ll want to approach disclosure, customer churn, and reputational loss correctly.
Examining the full corpus of breaches can help you learn what companies did or did not do that lead to a cybersecurity breach. (Just remember not to get too hung up on the major headline breaches and forget about the many others.)
2. If you want to learn from a breach, look at those within your industry.
Attackers have a different set of tools or skills to acquire what they’re after. Some are focused on credit card information, others on intellectual property, and so on. So if you’re an insurance company (and don’t deal with credit card information), you’re not going to look across the aisle to understand how an accommodation industry was hit with a point-of-sale attack. Rather, you’d want to look at what your industry peers are experiencing.
Similarly, if you’re a financial institution that isn’t regularly targeted for international espionage, you shouldn’t try to learn from the OPM breach. You’d be better served looking at breaches specifically in the financial sector (which are often targeted because of financial motivation).
3. Cyberattacks are not preventable.
The majority of breaches can be categorized as opportunistic. Attackers are largely scanning for anyone weak in a particular area so they can exploit them. But some attacks are more specifically targeted, like many financial institutions are targeted for their money. There are very different games you have to play to protect yourself. But regardless of the type of breach, it’s important that you understand that losses in data cannot be strictly avoided. You can certainly lower your risk following a number of best practices, but it’s nearly impossible to prevent any data loss from ever happening.
The best thing to do is to keep your cybersecurity posture in check and have a vendor risk management plan on hand if your network (or your vendor’s network) is ever exploited.


