See the news before it hits the headlines, from data breaches and ransomware events to industry and geo-specific chatter across the deep and dark web.

How does Bitsight Pulse work?
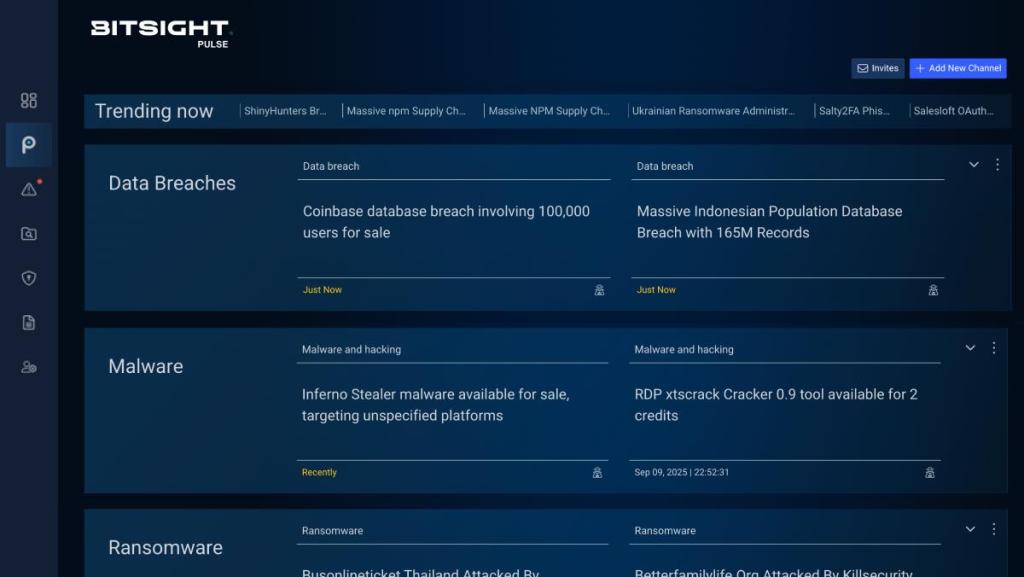
Bitsight Pulse consolidates the latest cybersecurity news, ransomware events and data breaches from hundreds of deep web, dark web, social and OSINT sources. Using Bitsight AI, Bitsight Pulse filters and personalizes these news events into three selected channels (location, sector, region) and displays the latest hot topics and trends.
Each new article is instantly structured with key details including a summary, topic category, threat actor, countries affected, victim organizations, industry sectors, and products, allowing you to quickly identify relevance, spot trends, share insights, and act decisively.
- DieNet Network targets my.gov.il in a cyberattack
- DieNet Network targets my.gov.il in a cyberattack
- Parker Lipman LLP attacked by INC Ransom ransomware group
- Access to hotel websites' admin panels and vulnerabilities for sale
- PENTAGON LAUNCHER dropper available for $2000/month
Bitsight Pulse Plans
Find the Bitsight Pulse plan that best fits your needs.
Need more than free threat news and events?
Bitsight Pulse can help you stay informed of global events and threats to your organization. To dive deeper and investigate events, Free users can upgrade to Bitsight Pulse Premium, where they can instantly share articles via email and other delivery mechanisms or download reports for easy distribution.
Go hands on with Bitsight Pulse Premium.
Experience Bitsight Pulse Premium’s dynamic intelligence feed and learn how your team can investigate, prioritize, and respond to global events impacting your business.
Looking for a complete threat intelligence solution?
Gain complete CTI visibility with the Bitsight Threat Intelligence platform:
- Empower teams with actionable threat intelligence from the clear, deep, and dark web
- Identify and prioritize vulnerabilities that pose the greatest risk
- Detect real-time mentions of your brand across the cybercriminal underground
- Discover all external assets and eliminate threat exposure blind spots
- Detect and manage compromised credentials in real time
- Consolidate all threat entity data for incident response, threat hunting, and IOC analysis
- Transform raw threat data into actionable insights and dynamic reports using Generative AI