Stay ahead of the compliance curve. Dive into our playbook curated by Tim Grieveson, Senior Vice President and Global Cyber Risk Advisor. Unearth insights to not just comply but lead in the era of NIS 2, DORA, PS21/3, and emerging cyber regulations.
Supply Chain Visibility: The Key to NIS2 Coordinated Risk Assessments


The path to NIS2 compliance is less about ticking boxes and more about fostering a resilient, proactive cybersecurity culture across the organisation and its extended network. While the challenges pertaining to third-party and supply chain risk management are significant, they are not insurmountable—especially if we break them down.
Today we will focus on understanding a very specific NIS2 requirement: Coordinated Risk Assessments. Let’s explore what that means and what you can do to enable compliance.
Breaking Down NIS2 Article 22: Union level coordinated security risk assessments of critical supply chains
The NIS2 Directive provides three mechanisms to guarantee supply chain security:
- Article 21(2)(d) mentions an obligation that can be described as an “entity’s suppliers risk assessment.”
- Article 22 mentions the coordinated risk assessment—a procedure, carried out at the EU level, to assess the level of risk of a specific supply chain.
- Throughout the text, there’s a notion that can be described as a “national risk assessment”, which includes all the powers of Member States to extend the scope of the Directive to entities originally outside its scope.
| A Coordinated Risk Assessment is a procedure initiated by the Cooperation Group (composed of representatives of Member States, the Commission, and ENISA) that is carried out at EU level to assess and mitigate the level of risk of a specific supply chain. |
In recital (90), the Directive states that coordinated security risk assessments of critical supply chains are aimed at identifying, per sector, the critical ICT services, ICT systems, or ICT products, as well as their threats and vulnerabilities. It looks at measures, mitigation plans, and best practices to counter critical dependencies, potential single points of failure, threats, vulnerabilities and other risks associated with the supply chain.
So what’s the criteria to conduct a coordinated risk assessment?
Recital (91) informs that this procedure should take into account both technical and non-technical factors. The latter include concealed vulnerabilities or backdoors and potential systemic supply disruptions, in particular in the case of technological lock-in or provider dependency.
This all follows the guidelines defined in Recommendation (EU) 2019/534, in the EU coordinated risk assessment of the cybersecurity of 5G networks, and in the EU Toolbox on 5G cybersecurity agreed by the Cooperation Group.
Now that we know what the requirements are, let’s look at how to pave the way for compliance. Here’s a hint: visibility across your entire supply chain.
Why Visibility is the Key to NIS2 Coordinated Risk Assessments
Visibility plays a pivotal role because it allows you to see all the connections and dependencies within your supply chain. Under NIS2, coordinated risk assessments require organisations to not only assess their own risk posture but also to understand how their suppliers and partners contribute to or mitigate those risks.
This interconnectedness means that a vulnerability in one part of the supply chain can ripple through and affect the entire ecosystem. Without visibility, you’re flying blind, potentially leaving critical gaps in your risk assessments.
What are the implications for your business?
If your organisation falls under NIS2 regulations, it could be deemed non-compliant if a supplier within your supply chain is identified as particularly high-risk through a coordinated risk assessment. Therefore, it's essential for businesses to closely monitor ongoing activities related to these coordinated risk assessments.
The value of visibility becomes apparent across many fronts:
- Comprehensive Risk Identification
- Effective Risk Mitigation
- Enhanced Coordination
- Proactive Risk Management
- Regulatory Compliance
Seeing the Whole Picture Matters: Lessons from the Kaspersky Ban on Supply Chain Visibility
Take, for instance, the recent Kaspersky ban in the United States. This was a political decision to ban a specific vendor from the supply chain of a country, and it serves as an example of a non-technical factor-based decision. The Bureau of Industry & Security (BIS) determined that Kaspersky poses an undue or unacceptable risk to national security for various reasons, including:
- Jurisdiction, control, or direction of the Russian Government
- Access to sensitive U.S. customer information through administrative privileges
- Capability or opportunity to install malicious software and withhold critical updates
- Third-party integration of products
To put this in perspective, Bitsight TRACE researchers analysed our proprietary data and detected a strong user base in Europe, with Germany and Italy leading. We observed over 14 million unique IP addresses communicating with Kaspersky update servers, making a total of over 100 million connections globally.
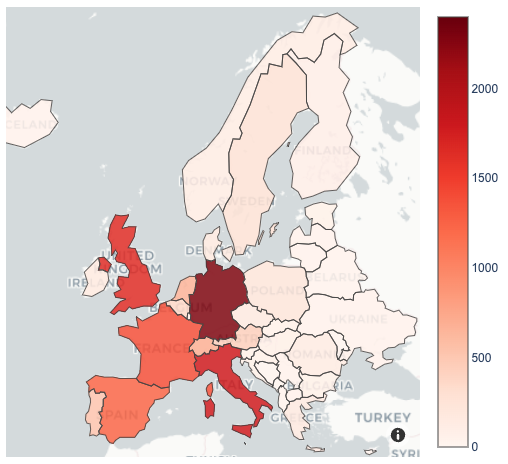
(Figure 1 - Percentage of unique IP addresses in Europe contacting Kaspersky servers, per country)
The Kaspersky ban underscores just how critical it is for organisations to have a clear view of their connections to potentially high-risk or banned products throughout their supply chains. You need to know, not just in theory but in almost real-time, whether your business, directly or indirectly, is using a banned product to avoid compliance issues, security vulnerabilities, or even legal ramifications.
Looking forward, the principles of supply chain visibility and coordinated risk assessments will only become more critical as threats continue to evolve. The NIS2 Directive offers a framework for navigating these challenges, but the onus is on each organization to ensure they are not just compliant, but ahead of the curve. By embracing visibility, businesses can transform compliance from a burden into an opportunity—one that enhances security, fosters trust, and drives long-term resilience.
The NIS2 Directive calls for a deep understanding of every link in your supply chain. By ensuring that your organization has the tools and processes in place to achieve this visibility, you are not only protecting your business but also contributing to a safer, more secure digital landscape across Europe and beyond.



