Risk 101: SSL Key Indicator in Security Effectiveness

Our use of the Internet can be characterized as a state of constant data exchange. While the exchanges of data between users and machines are often passive, when we are consuming information or clicking around from page to page, increasingly we need to exchange private or sensitive data. SSL (Secure Socket Layer ), and its successor TLS (Transport Layer Security), have become the de facto standard for encrypted and authenticated communications across the Internet.
SSL / TLS are cryptographic methods that are commonly found within web browsers and e-mail to prevent eavesdropping and tampering when we send PIN numbers, credit card numbers, personal data, and other confidential information across the Internet.
You’re probably aware of SSL / TLS when sending and receiving data across the Internet when you see “HTTPS:” or a lock in the URL bar as a visual cue.

However, you likely never considered how SSL / TLS was implemented, which while deceptively simple, has many common pitfalls that pose serious risk to the secure transfer of data across the world wide web and serve as a key risk indicator of security effectiveness. Risks in SSL / TLS implementation include:
- Strength of Encryption
- Purchase of Certificates from Unreliable Vendors and Not Developing a Strong Certificate Chain
- Using SSL 3.0 or Earlier Instead of TLS 1.0 or Later
- Incomplete Deployment across the Breadth of a Website or Application
Ivan Ristić, the founder of SSL Labs, details best practices for SSL / TLS deployment.
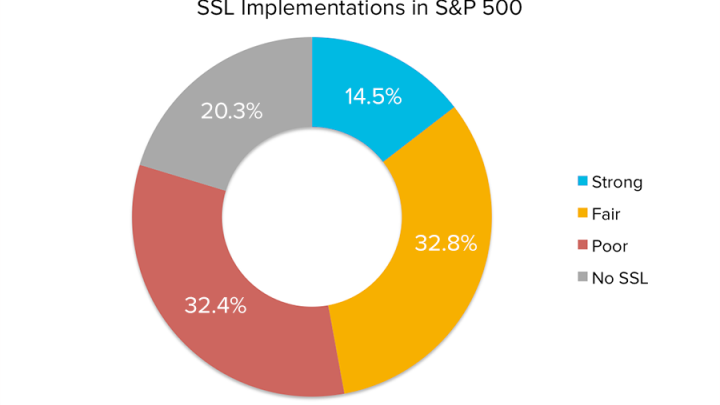
Analysis of SSL Across S&P 500
Earlier this month a pulse of the top 1 million websites performed by the Trustworthy Internet Movement showed that 29.1 % of the sites surveyed had improperly implemented SSL / TLS. Additionally, Bitsight’s analysis of the S&P 500 found that nearly one third of companies had improperly implemented SSL / TLS, and 20% had failed to implement broadly across their websites or applications.

SSL is well known and should be a part of all companies’ security programs. The fact that so many organizations are failing in this area, especially in light of recent breaches in the retail industry (where PCI compliance requires that organizations have properly implemented SSL / TLS), is representative of the bigger issues we all face with cybersecurity. If something as commonly accepted as SSL is not properly configured, what else could be exposing us to risk of breach?
** If you want to test the strength of your SSL / TLS implementation you can use the following open source resource provided by Qualys SSL Labs


