Monitoring SSL Vulnerabilities in Your Network
Microsoft has announced that it is removing SSLv3 support in both Internet Explorer (according to VentureBeat) and Azure Storage (according to Redmond Mag) on Tuesday, February 10. The company is not the first to stop supporting the technology, but this announcement should be one of the final straws for companies still supporting it.
Mozilla stopped supporting SSLv3 in November 2014. Oracle updated 19 Java vulnerabilities, while also disabling SSLv3 entirely on Tuesday, January 20. On the same date, Google Chrome removed SSLv3 support.
The Reason: SSL Vulnerabilities
One of the biggest reasons for the move away from SSLv2 and v3 are their vulnerabilities. SSLv2 is a deprecated protocol and has a wide range of known vulnerabilities. SSLv3 is vulnerable to the POODLE attack, discovered in October of 2014.
Are You Following These Recommendations Within Your Network?
In the fall, we wrote about how you can monitor your third parties' vulnerability to POODLE. This will eventually factor into a company's Bitsight Security Rating as well. (We will announce when that feature is live.)
Bitsight is adding two new SSL annotations:
-
Allows insecure protocol: SSLv2
-
Allows insecure protocol: SSLv3.
Why are these Annotations Being Incorporated into the Bitsight Algorithm?
Currently, in order to check if a company is vulnerable to the POODLE attack, a customer has to run the POODLE test separately. This test is limited in that it only checks the company’s primary domain. Incorporating this test into the TLS/SSL diligence risk vector means that customers don't have to run the POODLE test separately for entities, that all domains controlled by a company are tested for the vulnerability, and that being vulnerable to POODLE is actually reflected in the company’s rating.
How Will this Affect Security Ratings?
The ratings for companies that still support SSLv2 or SSLv3 may get lower because of the update.
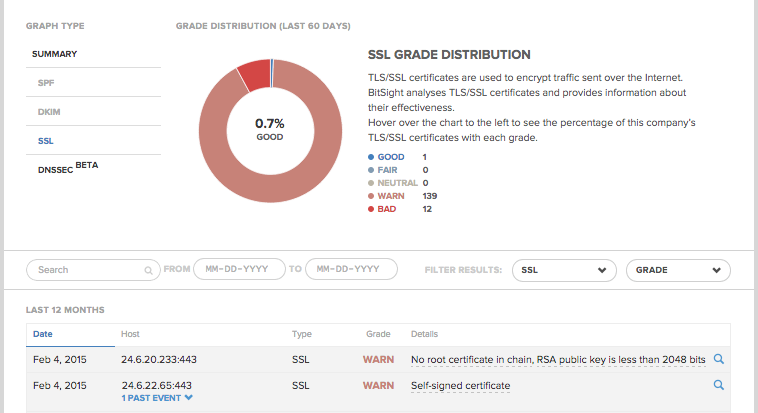
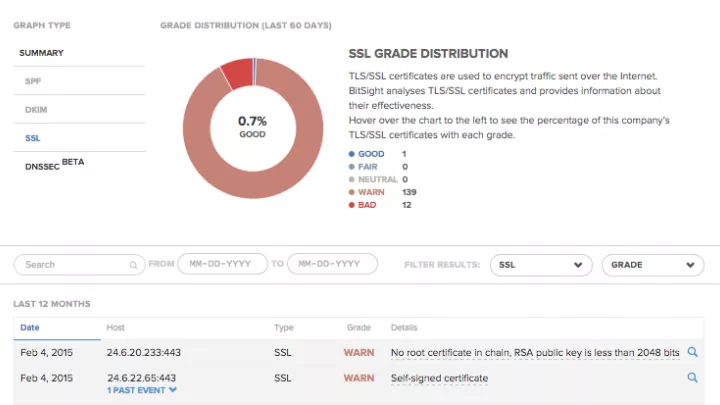
How to Monitor the TLS/SSL Certificates in Your Network
Within the Bitsight platform, customers can hover over the TLS/SSL graph on the Diligence page to see the percentage of a company’s TLS/SSL certificates with each grade (Good, Fair, Neutral, Warn, and Bad). In the chart beneath it, the reason for each certificate's grade is given, so it is easier for IT teams to fix problems with their certificates and improve their network security. (It also could cause a bump in the company's Security Rating.)


