Global State of Exposure: BIG-IP (CVE-2022-1388)

In May 2022, the U.S. Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA) alerted the public to a critical vulnerability affecting thousands of BIG-IP devices. The vulnerability, tracked as CVE-2022-1388, potentially allows a remote unauthenticated attacker to take complete control of the victim’s system, and to deploy ransomware and other malicious software.
Now, four months later, Bitsight evaluated the current global state of exposure to CVE-2022-1388. Our findings indicate that many organizations remain vulnerable to this critical vulnerability, presenting risk not only to these organizations but also to their customer bases.
This article will describe how your organization can stay up to date with patches for CVE-2022-1388, and promptly identify and remediate weaknesses in your supply chain.
Background: Big-IP and CVE-2022-1388
BIG-IP software products are licensed modules spanning a variety of use cases, including virtual environments, firewall management, application security management, load balancing, local traffic management, and more. The software’s broad access to internal systems makes it a target for attackers seeking to breach internal systems, and to deploy crypto miners and ransomware.
This vulnerability impacts several versions of F5’s BIG-IP software, including:
- 16.1.0 - 16.1.2
- 15.1.0 - 15.1.5
- 14.1.0 - 14.1.4
- 13.1.0 - 13.1.4
- 12.1.0 - 12.1.6
- 11.6.1 - 11.6.5
If your organization uses any of these versions, be sure to install the latest fixed version as outlined by the developer here.
Organizations currently exposed
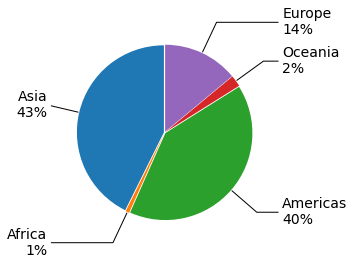
Bitsight identified many organizations currently exposed to CVE-2022-1388. Most of these organizations are from the technology sector, followed by telecommunications, education, and government/politics from the Americas and Asia.
Active exploitation and malware
It is important to understand exposure to CVE-2022-1388 because cyber threat actors are taking advantage of this vulnerability to attack organizations.
CISA recently added CVE-2022-1388 to its list of “Top CVEs Actively Exploited By People’s Republic of China State-Sponsored Cyber Actors.”
Reports also note that malware designed to exploit CVE-2022-1388 has doubled since May. The malware – called Chaos – is designed to target Linux and Windows systems running vulnerable versions of BIG-IP.
Organizations running vulnerable versions of the software should take prompt action to remediate their vulnerability to these cyber threats.
Third-party implications
Organizations should be alerted to potential risks posed by their third-party ecosystem. Bitsight recommends you contact your supply chain partners to better understand your third-party partners’ use of vulnerable BIG-IP versions. Bitsight customers can also follow this link to see which portfolio vendors are exposed to CVE-2022-1388.
Using the Enable Vendor Access (EVA) feature in the Bitsight portal enables customers to have data-driven, evidence-based conversations, making vendor risk management a more collaborative process. The EVA feature gives your business partners and vendors free access to the Bitsight portal, plus a Customer Success Manager to help your vendors understand and remediate risks.


