View our guide, 'Cybersecurity 101: Security Ratings Explained' to learn all about security ratings.
A Security Score vs. A Security Rating: What’s The Difference?

This post was originally published July 18, 2016 and has been updated for accuracy and comprehensiveness.
A security rating and a security score are often used interchangeably, but there are key distinctions between the two phrases.
In broad terms, a security score connotes a baseline, static result and is used by cybersecurity insurance underwriters to evaluate an organization’s potential risk. A security rating, on the other hand, offers more context into performance by providing a data-driven, objective and dynamic measurement of an organization’s security performance over time. This is important because cyber threats are continuously evolving and the cyber risk landscape is always changing.
The Oxford Dictionary definitions help to further distinguish these two:
- Score: The number of points, goals, runs, etc., achieved in a game by a team or an individual.
- Rating: A classification or ranking of someone or something based on a comparative assessment of their quality, standard, or performance.
Assessing the cybersecurity posture of trusted vendors, suppliers, and other business parties is a very complex task. With so many different elements involved to secure a network, it’s rare that a company’s security score is simply just “good,” “average,” or “bad.” A complete picture of an organization’s security is more nuanced.
The founders of Bitsight chose a security ratings scale as a performance metric for this very reason. Third- party cybersecurity risk management can require in-depth conversations with companies, and having a more precise view of a company’s security posture makes for a more valuable and transparent conversation.
Security Ratings vs. Security Scores: A Deeper Dive
Comparative assessment is a key differentiator between a security score and security rating. Organizations that are trusting third parties with sensitive data cannot afford to simply know that some of their business partners have a score of “A” versus a score of “C.” Context into their security performance over time, how they compare to similar companies in the same industry, and how they compare to other vendors is far more helpful. Without this context, organizations may be selecting, onboarding, and continuously monitoring vendors with a limited view of their overall cyber risk.
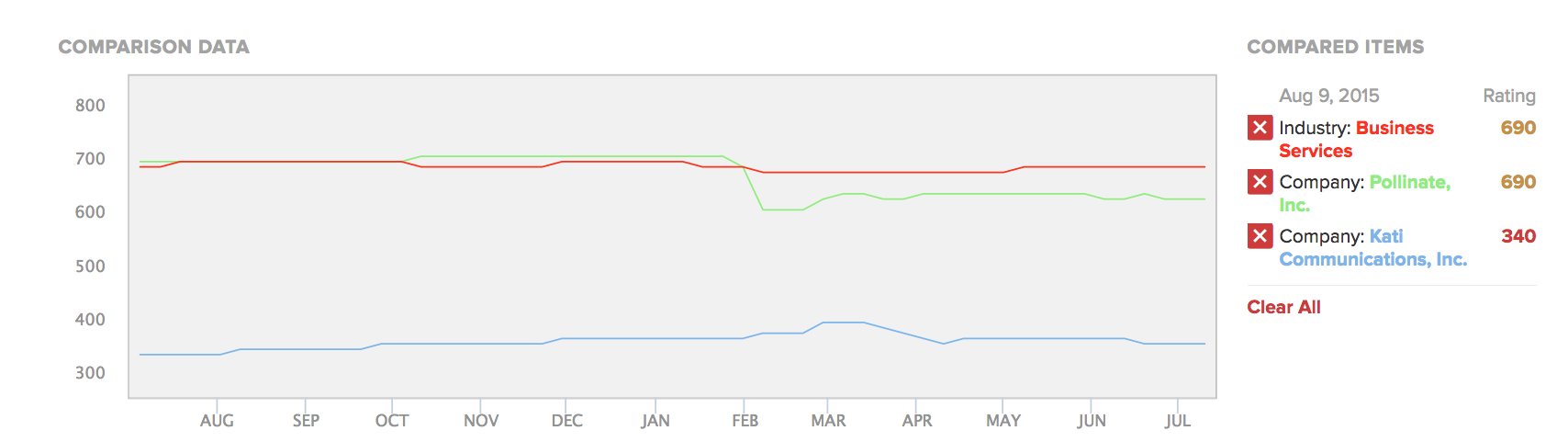
A comparison of two companies in the Business Services industry (all companies shown are fictitious).
Take the example of a general manager for a baseball team. When spending millions of dollars on signing a pitcher, is it sufficient to only know that the player won nine games and lost three in the last year? A savvy manager would want to know more. What is their career earned run average? How do they perform against left-handed batters versus right-handed batters? The list could go on and on, but more data points translate to greater confidence when making business decisions.
Going Beyond a Security Score
Bitsight Security Ratings are built with a detailed set of parameters that go beyond a static security score, giving a real-time view into an organization’s security posture. Armed with more data points, organizations can now monitor and mitigate third-party cyber risk during the selection, onboarding, and life cycle of the business relationship.



