A Guide to Adaptive Security

What is Adaptive Security?
Adaptive security is an approach to cybersecurity that helps your Security Operations Center (SOC) quickly adapt to the latest threats. By implementing adaptive security, your organization can evaluate and analyze behaviors and events in real-time to take preventative action before a breach.
Unlike traditional security programs that focus primarily on remediation and issue response, an adaptive security approach automatically and continuously monitors the entire attack surface to uncover anomalies, malicious traffic, and vulnerabilities swiftly
With this observability, your SOC can stop potential risks from becoming actual risks through root-cause analysis and predictive analytics. Importantly, adaptive security allows you to gain an understanding of your organization’s security performance and continuously adapt and improve based on data-driven insights.
How to Implement Adaptive Security
To fortify cybersecurity measures effectively, organizations should incorporate the Four Stages of an Adaptive Security Architecture into their strategy. This approach, as delineated by Gartner, ensures a comprehensive and proactive defense mechanism that evolves with the threat landscape.
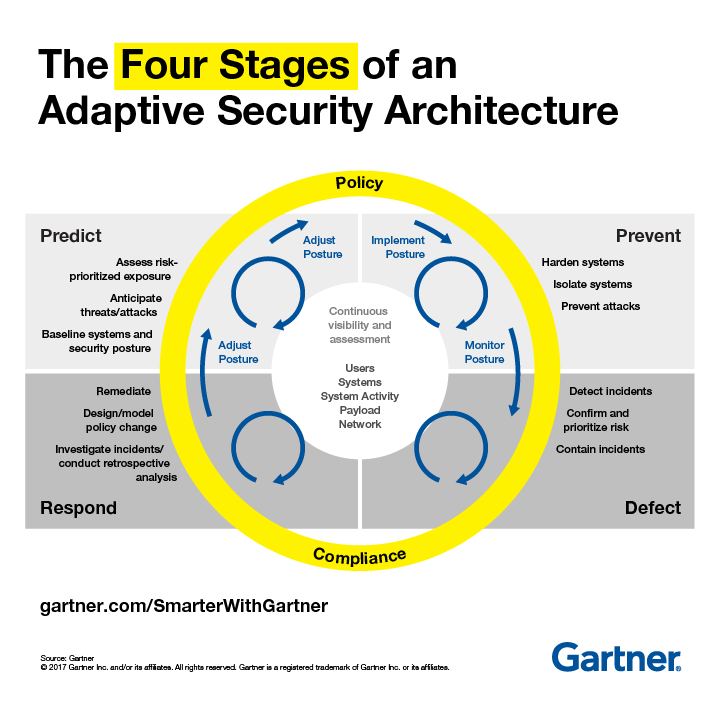
The 4 Stages of Adaptive Security: Real Examples
Gartner's infographic above illustrates a cyclical, dynamic approach to cybersecurity encompassing four key stages. Below are several real-world examples of each:
1. Predict
Proactively identify potential threats by analyzing risk and anticipating attack vectors. For example:
- Analyzing dark web traffic to predict the sale and distribution of stolen credentials
- Implementing AI-driven threat hunting to identify abnormal behavior indicative of APTs (Advanced Persistent Threats)
- Utilizing Bitsight's continuous monitoring to identify and analyze trends in your organization's security performance and help predict potential security events
2. Prevent
Implement measures to reduce vulnerability and avert incidents before they occur. For example:
- Enforcing multi-factor authentication to reduce the risk of unauthorized access
- Applying zero-trust network access controls to prevent data breaches.
3. Respond
Effectively address and mitigate the impact of security incidents after they happen. For example:
- Deploying automated incident response to quickly isolate infected systems and prevent the spread of malware
- Utilizing forensic analysis tools post-incident to understand the breach's cause and impact
4. Defect
Ensure ongoing compliance with security policies and regulations, and manage any defects in security controls. For example:
- Implementing a bug bounty program to discover and fix vulnerabilities before they can be exploited
- Regularly conducting security audits and penetration testing to ensure compliance with security standards
How Security Ratings Can Help
To protect against and adapt to threats before they happen, you must first gain visibility into hidden risks in your digital infrastructure.
Instead of waiting for your next scheduled security audit, a more effective way to assess cyber risk is to continuously monitor your IT infrastructure using a tool like Bitsight Security Ratings:
Measure and Continuously Rate Security Performance
Security ratings are a data-driven measurement of enterprise-wide security performance. Ratings allow you to assess risk and the likelihood of a breach based on risk factors such as unpatched systems, open ports, misconfigured software, malware infections, and weak security controls.
Findings are presented as a numerical score (like a credit score), making it easy to convey risks and your organization’s cyber readiness in terms that all stakeholders can understand.
With the context and visibility that security ratings provide, it becomes much easier to prioritize mitigation decisions and allocate resources where they’re needed most.
Continuously Assess the Effectiveness of Security Controls
Security management is a constant game of whack-a-mole—the minute you fix an issue, another one pops up. But the real focus should not be on fixing an individual problem. Instead, the focus should be on identifying and fixing the underlying cause that allowed the issue to occur in the first place.
For example, if you use Bitsight Security Ratings to continuously monitor your digital environment for cyber risks and it identifies gaps in your network, you can then patch them. But ideally, you should implement a control system that helps you prevent gaps from forming in the first place. This is getting to the root cause, and Control Insights which is built into Bitsight for Security Performance Management, can help you get there.
Unlike point solutions that only measure the effectiveness of a single control and must be configured to monitor specific infrastructure, Control Insights continuously assesses the effectiveness of every security control across your extended enterprise, without initial configuration. If it finds any issues it automatically suggests how to remediate those gaps.
Reveal, Remediate, and Monitor Supply Chain Risk
Third-party cyber risk is now a leading cause of data breach. That’s because hackers look for the weakest link you’re an organization’s security posture. Often, this resides in your business’ interconnected supply chain.
Assessing this risk typically involves questionnaires, vendor risk assessments, and penetration testing. But these tools don’t provide a complete view of cyber risk hidden in your supply chain. Neither do they adapt to reveal emerging risk—they only capture a snapshot of a vendor’s security posture at a point-in-time.
Alternatively you can use a continuous monitoring solution like Bitsight for Third-Party Risk Management to adapt your security program to tackle growing third-party threats. Based on the Bitsight Security Ratings data and analytics platform, the solution provides an immediate, near real-time snapshot of your third parties’ security postures. A higher rating denotes better security, while a lower rating means improvement is needed.
Using these data-driven insights, you can speed up the vendor onboarding process and, once the contract is signed, Bitsight continuously assesses your vendor’s security postures for the remainder of your partnerships. If a new vulnerability is detected, you’ll receive automatic, near real-time alerts and can share these findings with your vendors so that, together, you can quickly and collaboratively respond to new threats.
Quantify Cyber Risk and Adapt Appropriately
To continually adapt your security program, you need to know which network vulnerabilities are the riskiest or could result in the most financial damage if breached.
Rather than best guess, use Bitsight’s powerful monitoring and cyber risk modeling technology to financially quantify the impact of a breach. With Bitsight’s data-driven insights, you can simulate your organization’s financial exposure across thousands of cyber events, including ransomware, denial of service, compliance issues, supply chain attacks, and more.
With this understanding and cyber risk quantification, you can make better, faster decisions on how to adapt your security program and focus resources and investments to avoid future incidents.
Unite Your SOC Around an Adaptive Security Strategy
With the capabilities that Bitsight’s tools provide, your organization can derive the insight it needs to develop a robust adaptive security program, create improvement plans, prioritize risk-reduction strategies, and unite teams around the actions that have the most impact.


