New vulnerability could lead to one of world’s most powerful cyber attacks

The other week, Bitsight released a piece of high-profile research alerting the public to a high-severity vulnerability potentially allowing attackers to launch one of the most powerful Denial-of-Service (DoS) attacks in history. Here’s a summary of what happened and why it matters:
- On April 25th 2023, researchers from Bitsight and Curesec jointly discovered a high-severity vulnerability — tracked as CVE-2023-29552 (CVSS 7.5) — in the Service Location Protocol (SLP), a legacy Internet protocol.
- Bitsight identified over 2,000 global organizations and over 54,000 SLP instances as of February 2023 — including VMware ESXi Hypervisor, Konica Minolta printers, Planex Routers, IBM Integrated Management Module (IMM), SMC IPMI, and others — that attackers could potentially leverage to launch DoS attacks on unsuspecting organizations around the world.
- Successful exploitation of this vulnerability could potentially allow an attacker to launch one of the most powerful DoS amplification attacks in history with a factor as high as 2200 times.
- Assuming a leadership role in the cybersecurity community, Bitsight:
- Collaborated with the U.S. Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA) to responsibly disclose CVE-2023-29552. Read the CISA Activity Alert here.
- Collaborated with security operations center (SOC) teams at Fortune 500 technology firms to inform experts and answer pressing questions.
- Alerted leading DDoS mitigation firm, Cloudflare, to our discovery so they could take steps to protect their broad customer base. Read Cloudflare's announcement here.
- Reported the vulnerability to VMware. Read the VMware Security Response Center’s announcement here.
- Publicly released our joint research with Curesec, announcing CVE-2023-29552.
- Merged CVE-2023-29552 into the Bitsight product, allowing customers to detect and respond to exposure in their first- and third-party digital ecosystems.
- Collaborated with the U.S. Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA) to responsibly disclose CVE-2023-29552. Read the CISA Activity Alert here.
Security leaders are asking “now what?” and Bitsight has answers. Let’s review how serious DoS attacks are, why they matter, and how you can protect your organization from CVE-2023-29552 and similar vulnerabilities in the future.
DoS attacks: A brief history of their impact
DoS attacks can bring down entire companies, inflict significant financial losses, and permanently damage a company’s reputation and ability to do business. These attacks are serious business risks that must be considered at all levels of the organization, from the board to executives to security leaders.
What is a DoS attack?
In a DoS attack, a threat actor sends mass amounts of traffic to machines or network resources with the intention of shutting down the targeted system, rendering it unavailable to its users. If an attacker uses one (more than one) system to launch the attack, then it’s a DoS (Distributed Denial-of-Service (DDoS)) attack. Typically, attackers leverage others’ systems to send the traffic for them; this is called a reflection amplification attack because the attacker is requesting information from systems on the Internet and “reflecting” the systems’ replies to a target IP address. This request/reply interaction is what’s responsible for sending the traffic.
Pretend you’re an attacker for a second. If you want to flood a target’s systems to bring them down, you want to generate much more reply traffic than you request from the system, right? That’s where the amplification factor comes in. The amplification factor is the ratio between reply to request magnitudes. If a 10 byte request generates a 1000 byte response, then the factor is 100. The below chronology of DDoS attacks shows that amplification factors tend to hover between four and 500, while CVE-2023-29552 allows attacks with a factor of 2200X.
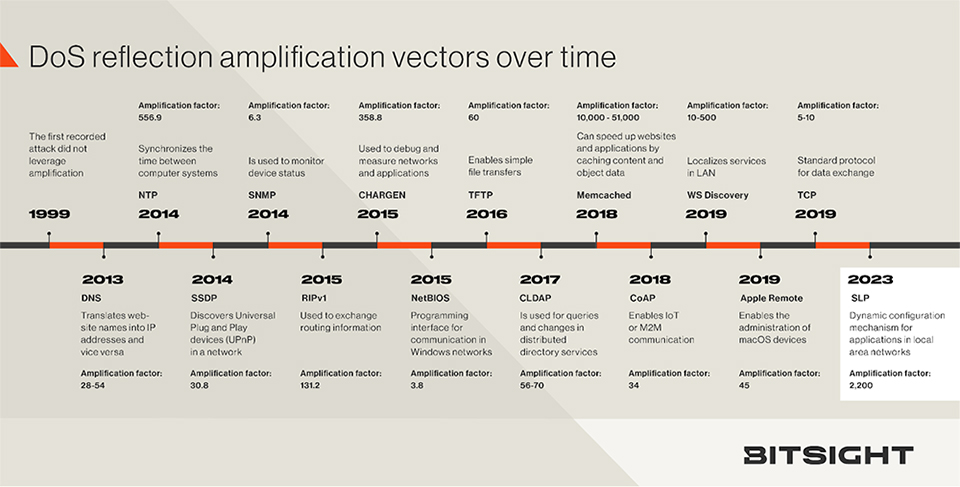
DoS attacks can inflict significant harm to your organization
Falling victim to a DoS attack can lead to significant business downtime and subsequent reputational harm and financial loss. The average DDoS attack costs organizations $40,000 per hour, according to a report. As hours turn into days, and days into weeks and months, financial losses can accumulate to significant sums if your organization becomes the victim of a DDoS attack.
But the harder-to-quantify impacts can sometimes be more acute and critical. Business disruption could mean your organization is rendered incapable of providing contractually-agreed-upon services to partners and customers; this could result in permanent reputational damage and interfere with your ability to do business in the future. In practice, this could be initiated by your organization’s IT systems — websites and other systems you use to conduct business — being disrupted. This is a particularly serious risk for organizations relying on web-based purchases.
The main point? DoS attacks are a serious risk to your organization but there are concrete steps you can take to manage this risk.
How you can protect your organization
Make no mistake, you should take the necessary steps to protect your organization from CVE-2023-29552 but zooming out to see the bigger picture is critical to organizational security that goes beyond this CVE.
Detecting vulnerabilities in your own systems
If you can’t detect it, then you can’t protect against it. That’s where external attack surface management comes in – detecting and responding to cyber risk at scale. Bitsight Security Performance Management (SPM) offers key External Attack Surface Management (EASM) capabilities, helping your organization continuously discover its attack surface, identify where exposure exists, and prioritize remediating vulnerable areas of infrastructure. Take SLP systems for instance – Bitsight allows you to quickly and efficiently identify deployed SLP systems in your organization and then take steps to remediate vulnerabilities in those systems, like CVE-2023-29552.
Here’s what Bitsight customers see when they search for CVE-2023-29552:
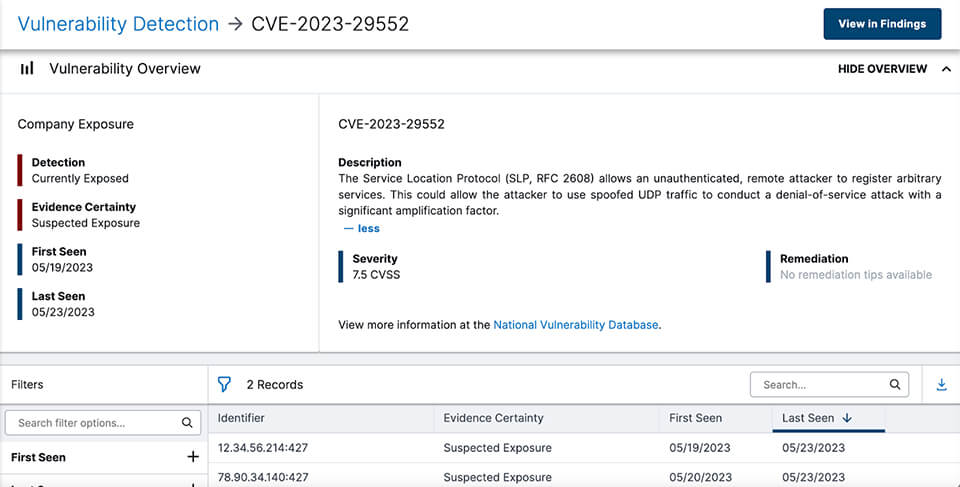
Source: Bitsight Security Performance Management. All IPs are fictitious for demonstration purposes.
Bitsight customers can quickly identify exposure to CVE-2023-29552 in their digital ecosystem, allowing them to detect vulnerable systems and prioritize remediation based on evidence.
But the risks don’t end with your organization. You need a way to ensure your third parties are not using vulnerable systems that could be leveraged by threat actors.
Detecting vulnerabilities in your third-party ecosystem
Managing vendor exposure to critical vulnerabilities quickly, effectively, and at scale is crucial to protect your network. When a major security event hits the news, how do you know which of your vendors is affected? How are they potentially exposing your organization? In the heat of the moment, you need to be able to answer these questions quickly and accurately.
With Bitsight’s Vulnerability Detection & Response capabilities, included in our Continuous Monitoring solution, you can gain insights into vendor exposure to vulnerabilities and take action on high-priority incidents impacting your vendors at a moment’s notice, while communicating critical information to board- and executive-level stakeholders during high-stress situations.
With Bitsight you can:
- Detect, manage, and mitigate emerging zero day vulnerabilities in your vendor ecosystem with speed
- Remediate risk more quickly and effectively with better prioritization of critical vendor response
- Initiate and track vendor outreach at scale through built-in questionnaire capabilities
- Confidently adhere to growing regulatory pressure with easy access to critical vulnerability data
Searching for CVE-2023-29552 using Bitsight’s Vulnerability Detection feature, Bitsight customers see this:

Source: Bitsight Third-Party Risk Management. All company names are fictitious for demonstration purposes.
Bitsight customers can quickly detect exposure to CVE-2023-29552 in their third-party ecosystem, seeing which third-parties are exposed with supporting evidence, and when the exposure was first and last seen. From here, Bitsight customers are armed with what they need to take the necessary steps to remediate third-party exposure.
Take action now
CVE-2023-29552 will not be the final vulnerability allowing for DoS attacks. It’s therefore critical for you to zoom out and consider the bigger issue at hand, namely that external attack surface management and third-party risk management are critical to ensuring your organization is protected against CVE-2023-29552 and similar threats that are bound to present themselves in the future.
Bitsight is your trusted partner in your journey to a stronger security posture. Contact us today to learn more!






