Less Is More: Consolidating Your Third Party Risk Management Tools



Proudly serving over 3,000 enterprises globally, Bitsight works closely with risk leaders across industries to help them protect their businesses. CISOs and third-party risk professionals face pressing challenges, from regulations to efficiency to maintaining supply chain resilience—all calling for smarter, easier, and more integrated solutions.
On September 1, 2022, Bitsight announced the acquisition of ThirdPartyTrust, an innovator in the third-party risk management space disrupting how an enterprise manages, or even thinks about, third and fourth-party risk. Led by a dynamic and brilliant entrepreneur, Anders Norremo, the company applied a unique approach to managing the growing threat emerging from the digital supply chain.
Over the past year, we’ve been riding the journey of integration and seeing an amazing result: over 90% customer growth in the last 12 months. Today, we announce the full integration of Bitsight Vendor Risk Management into the Bitsight portal, combining the automation, workflows, and vendor network with Bitsight’s breadth of cyber risk data, Continuous Monitoring, and vulnerability response capabilities.
We sat down with Anders, now VP of Product at Bitsight, to discuss what we learned from hundreds of conversations with supply chain risk leaders. These are the insights that influenced the integration and our view of managing third-party risk end-to-end.
Q: You’ve spoken with hundreds of risk leaders. Is there a common theme that runs throughout?
Anders: The number one thing we heard is: this is really hard. As the cyber risk landscape gets increasingly complex, our customers find themselves acquiring an overwhelming number of security solutions. With the rising demand to manage an ever-growing vendor population, teams are at the breaking point where a main focus is accelerating their assessment process. This has proven difficult when having an array of siloed tools. We see a push to consolidate the number of platforms to drive efficiency and better use of consistent data. To achieve that, teams seek cyber risk management solutions seamlessly integrated across their many TPRM workflows, including assessing and onboarding vendors, continuously monitoring vendor risk, and managing vulnerabilities in the digital supply chain.
Q: Consolidation and integration: how does it apply to onboarding vendors?
Anders: Many customers have told us they wish to expedite vendor risk assessments and onboarding. Tools like Bitsight Vendor Risk Management are meant to automate and centralize the assessment process so it’s more efficient. A huge benefit is that it’s tightly integrated with other tools for performing third-party risk processes. Switching between comprehensive point-in-time assessments and continuous vendor risk monitoring takes just a click of a button—that’s the productivity hack risk leaders are asking for.
This comes even more handy for highly regulated businesses or those under regional regulations, like DORA, NIS2, and SEC, to name a few. Bitsight VRM has over 40,000 companies in its vendor network. That means security teams can leverage these profiles both when assessing vendors and when working with clients’ onboarding process, which in turn is going to speed up the process and free them from manual work.
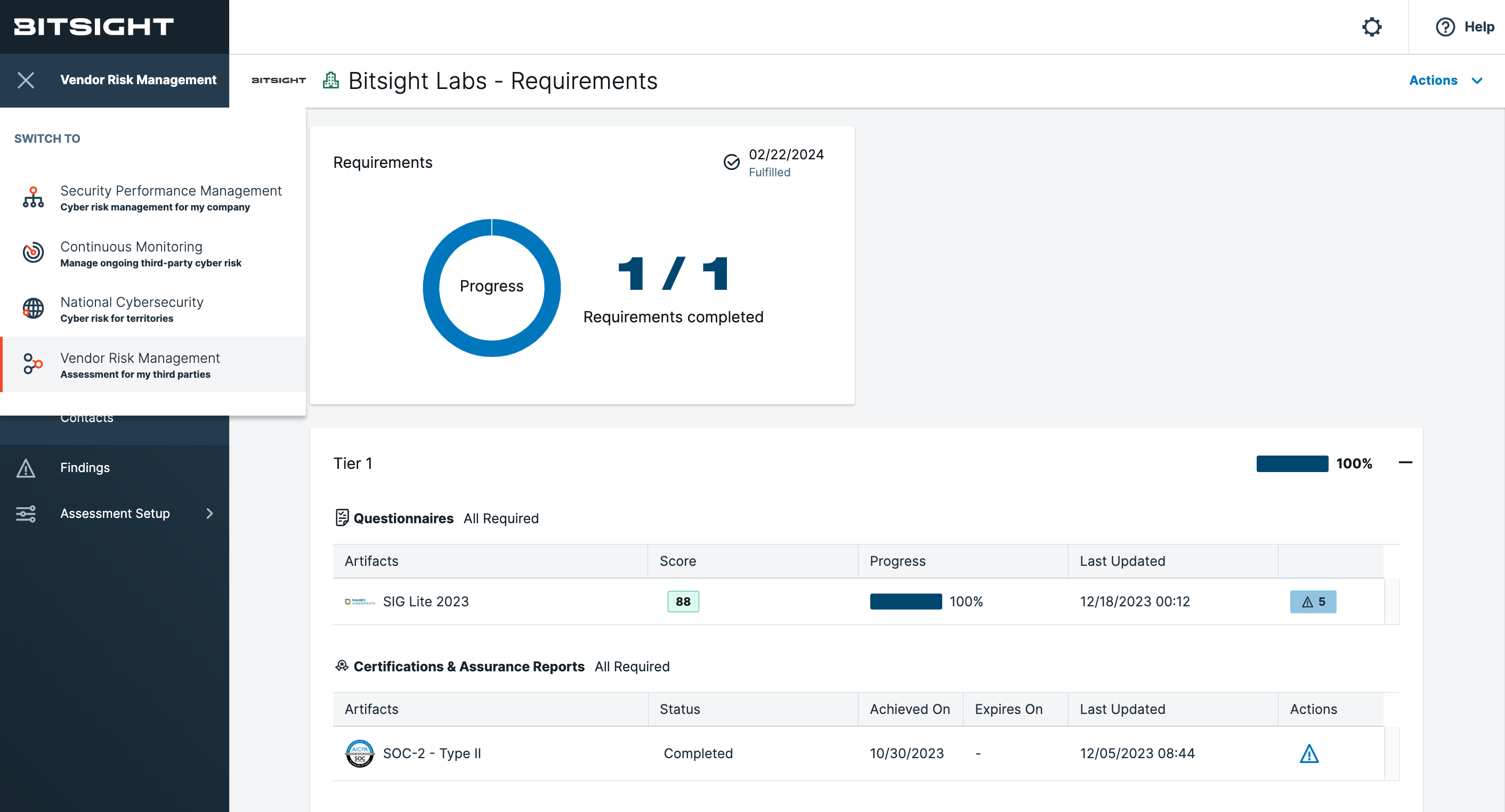
Bitsight Vendor Risk Management provides enhanced requirements and automated assessments within one view
Easy to switch among TPRM workflows within the fully integrated Bitsight Third Party Risk Management
Q: What are the benefits of having a TPRM solution with natively embedded data vs. integrations from other data sources?
Anders: In the day and age of “solution overload,” the more you combine platforms, the more efficient your team will be. You no longer need to manage access across multiple platforms or train your users on how to navigate and operate disparate tools. Data no longer sits on various islands where teams are constantly reconciling data or pulling the data out of systems into spreadsheets.
Customers also find that natively integrated tools are richer in their capabilities and ease of use than a set of platforms strung together in a daisy chain approach. For example, the data and analytics from Bitsight Continuous Monitoring are proven to have the strongest correlation to risk. Leveraging them to validate vendors’ responses and drilling into the details whenever customers need to is key to efficiency and program confidence.
Q: Where do you see the future of Digital Supply Chain Management heading? Where does AI play a part?
Anders: TPRM programs will be driven to continue to increase their effectiveness and execution. Relying on people doing the right thing and following a process will remain important. Still, an inevitable shift is happening to insert more data and intelligence into the TPRM process: every step of the way from onboarding to assessment, risk remediation, continuous monitoring, and beyond.
The next generation of solutions will also need to leverage the power of AI to make informed and faster decisions. AI has the potential to speed up the comprehension of a vendor's security posture, automatically pointing out the control gaps that exist, and automating many of the other manual tasks that security analysts perform today. This will result in businesses’ employees being freed up from checking ‘yes/no’ boxes to focus on high-value activities that often involve working hand in hand with their vendors to drive risk remediation and ultimately reduce the risk of a negative event.
To learn more about the Bitsight TPRM solutions, go to the new unified Vendor Risk Management and Continuous Monitoring for a deep dive.


