Bolek – An evolving botnet targets Poland and Ukraine

Bolek is a recent malware from the Kbot/Carberp family. We first heard about this malware from the cert.pl blog post in May 2016, and since then, a few others have published additional information about it (links below).
This is a very interesting piece of malware because it is being subject to frequent updates and has malicious capabilities which include self-spreading through USB and network shares, TOR network access, screen captures and web injects, and uses asymmetric cryptography to secure network communications.
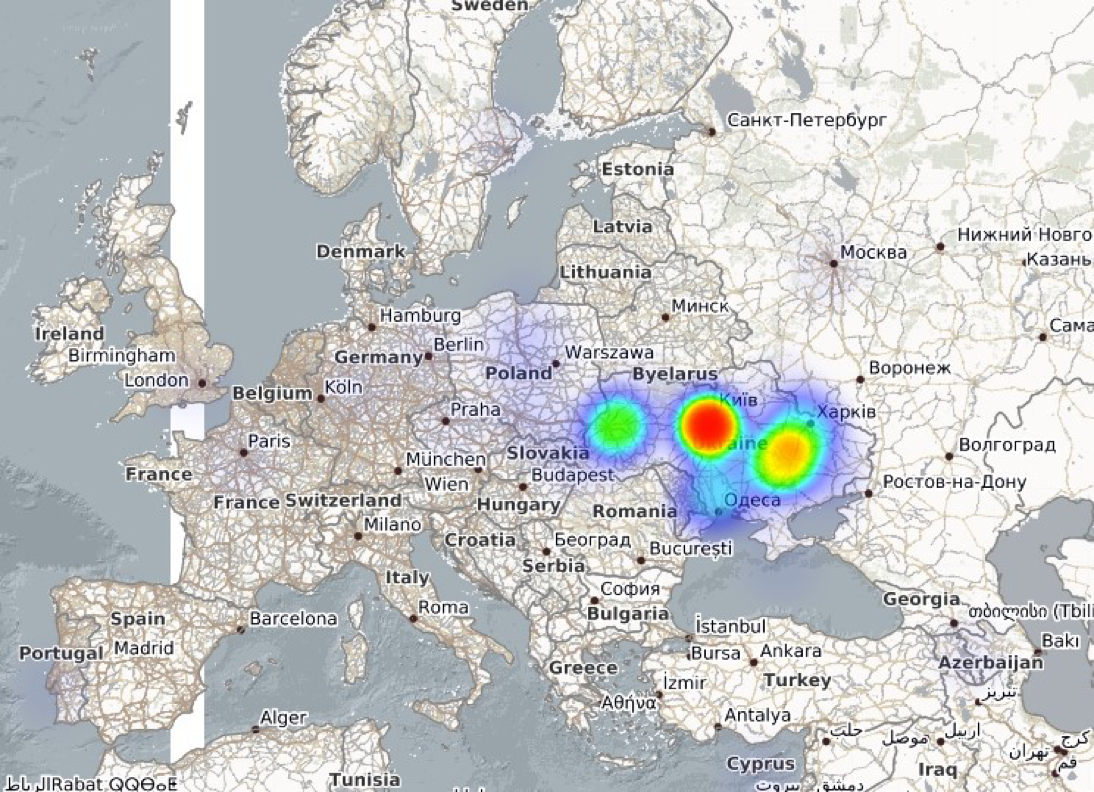
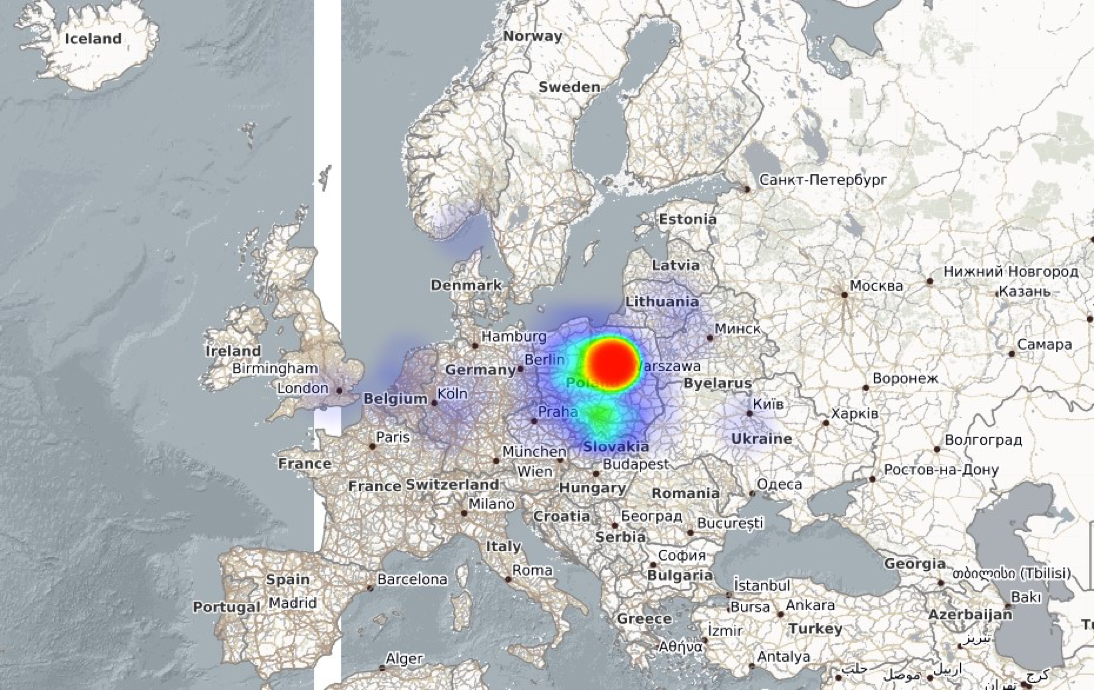
Anubisnetworks has recently sinkholed two botnets of this family, one that is targeting Ukraine and another one that is targeting Poland. The following images show the clearly targeted geographic dispersion of the infections.
Bolek botnet targeting Ukraine:
Bolek botnet targeting Poland:
Looking at malware samples for each of the botnets, we found two different versions in use (1.0.2.0 and 1.0.3.1), both have more recent version numbers than the ones analysed by cert.pl back in May (1.0.1.0), showing that this malware is being actively updated. On a quick look, a relevant difference we noticed is that the config is no longer stored in clear text on the binary and is now obfuscated.
Through the use of a Debugger it is still possible to obtain the configurations without having to look at the actual obfuscation mechanism. The following are the configs for each of these botnets:
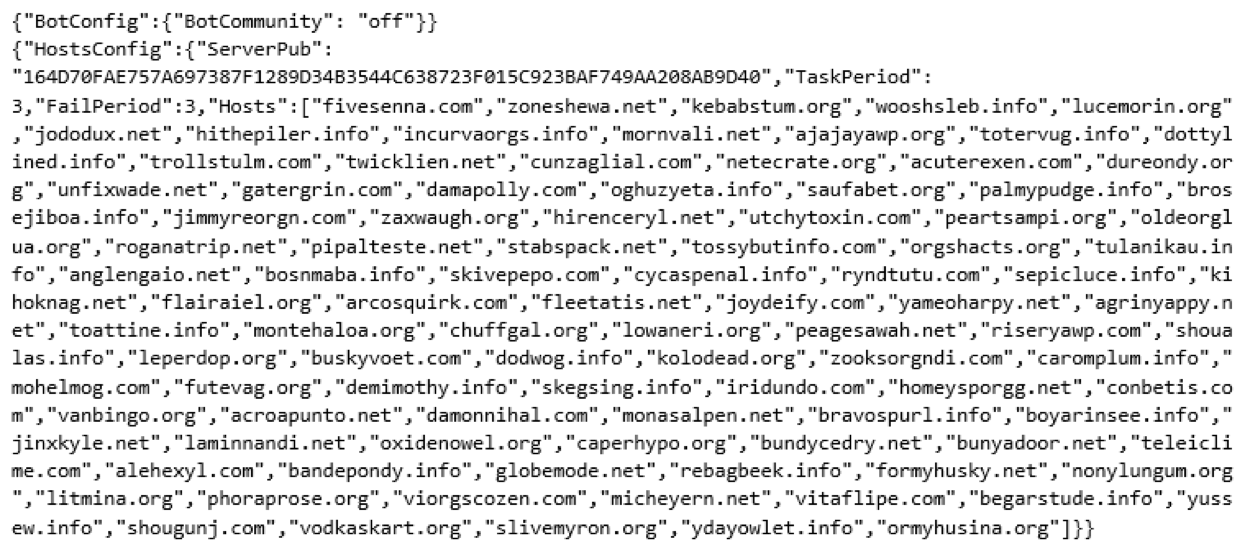
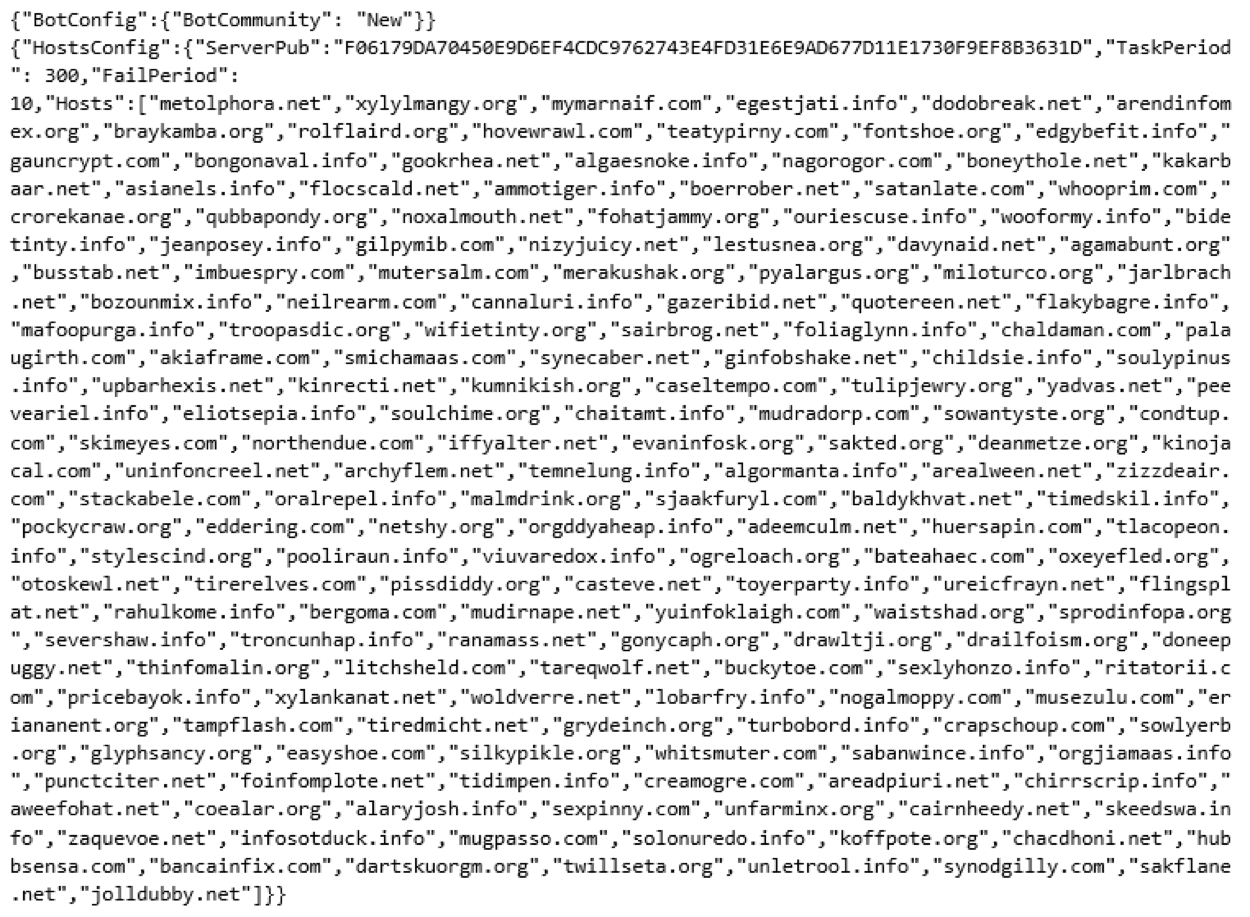
As these configs, show, the botnets come preconfigured with a large number of domains that can be used for C2, on the event that some of them get taken down.
For further reading on Bolek and its features, please see the following links:
- https://www.cert.pl/en/news/single/newest-addition-a-happy-family-kbot/
- http://vms.drweb.com/virus/?_is=1&i=8202516&lng=en
- https://www.arbornetworks.com/blog/asert/communications-bolek-trojan/
- https://phishme.com/bolek-leaked-carberp-kbot-source-code-complicit-new-phishing-campaigns/
We will keep monitoring this threat as it evolves, keep posted for new updates.
Samples analysed:
ed1a6200d871122600bd0f2f73c79d072c1a2c0eb9fd122ea2f40f45cf21b191
0f37e74d790cceafe09a53b33bb28ac262594d469dcd23e8bbe60bede71c67c3


