Bitsight Releases ROBOT Vulnerability Identification Feature
Tags:

Within the Bitsight Security Ratings platform, we prioritize features specifically chosen to help organizations identify and manage risks across their own networks and the networks of their third parties. Bitsight now enables users to identify organizations who are potentially vulnerable to ROBOT — short for "Return Of Bleichenbacher's Oracle Threat"— attacks. The vulnerability behind the ROBOT attack was originally discovered in 1998 and has resurfaced through a number of proprietary TLS/SSL implementations, affecting some of the most popular websites — including Facebook and PayPal. The vulnerability ultimately provides a method by which an attacker can decrypt TLS/SSL traffic and obtain sensitive information.
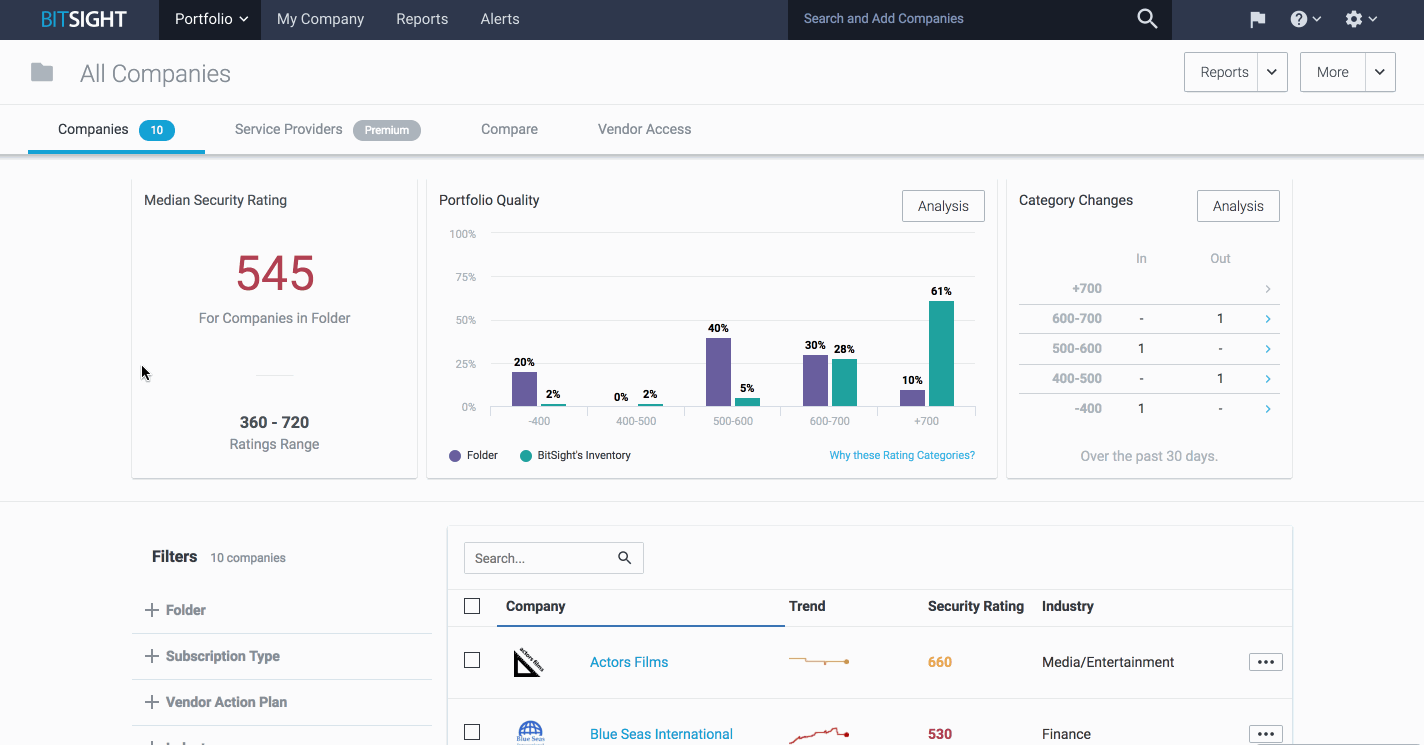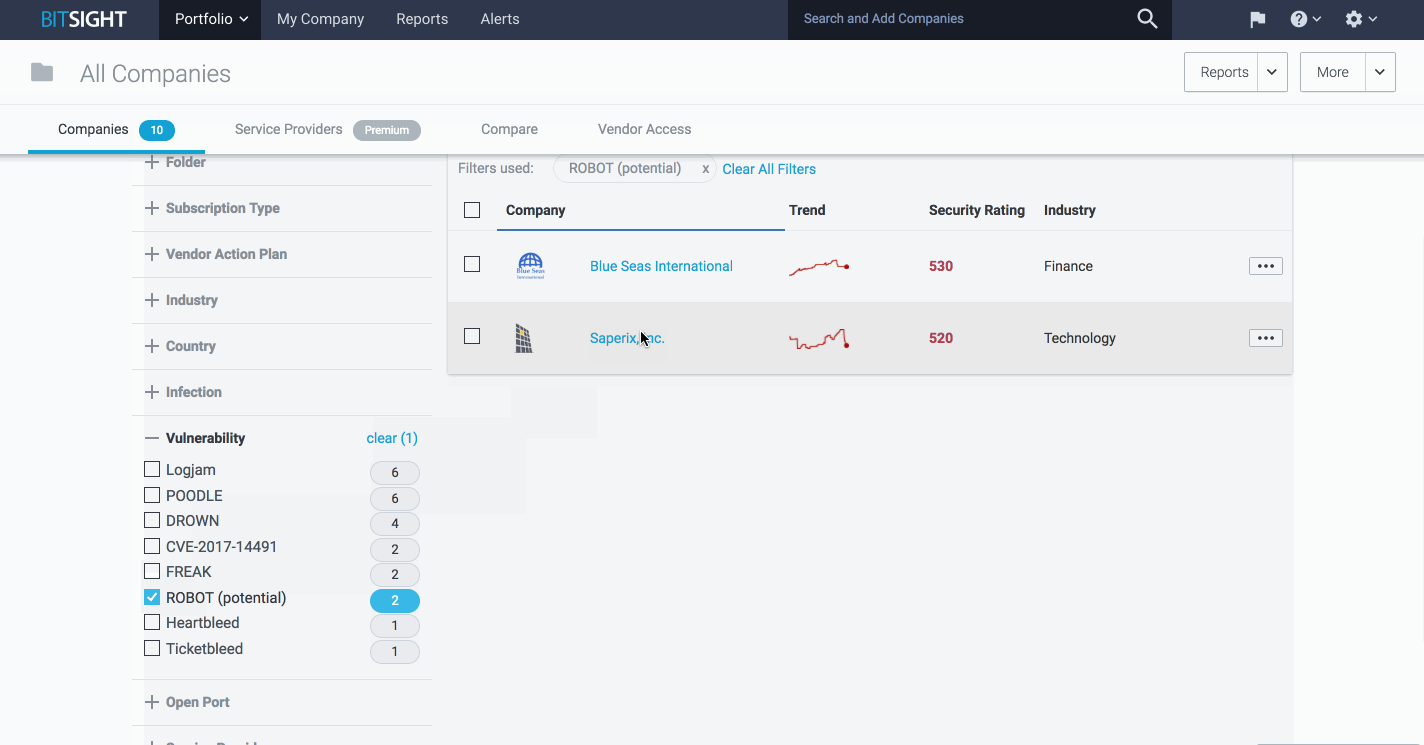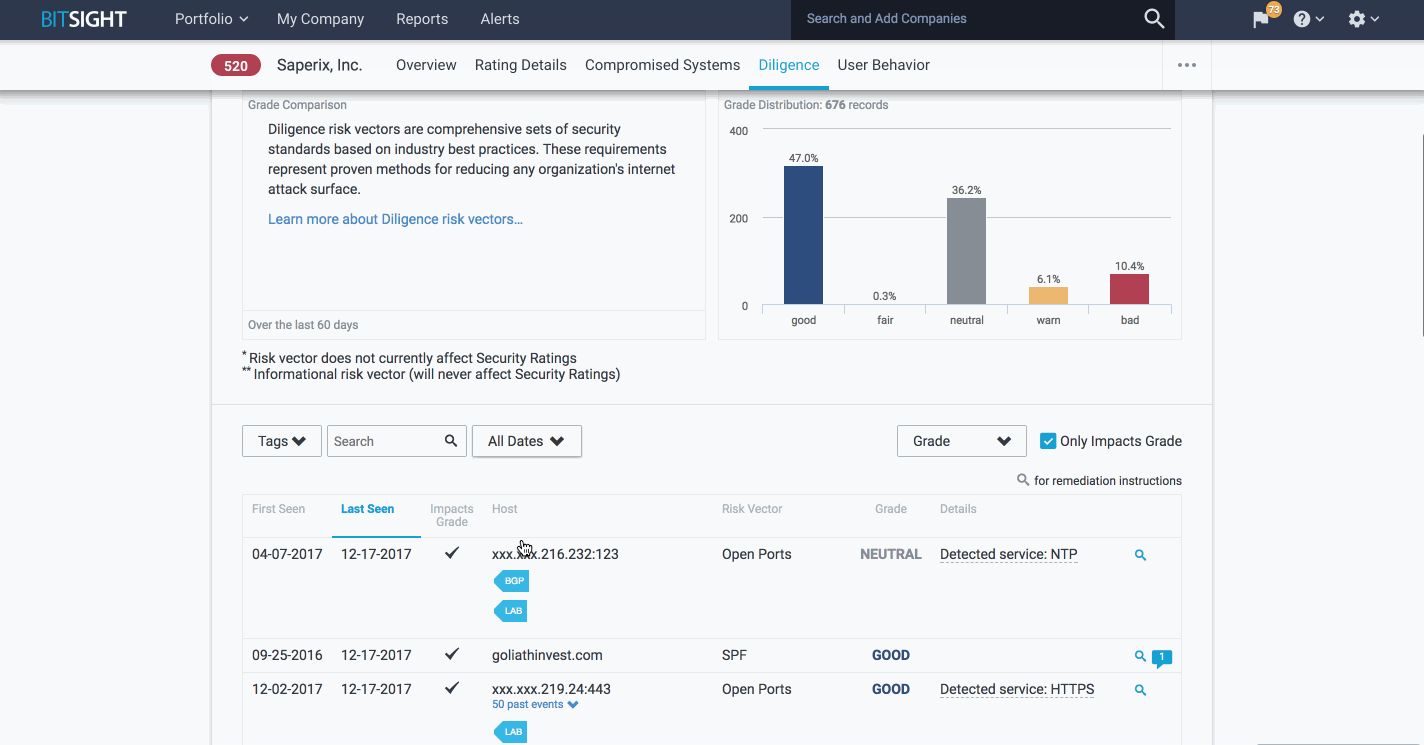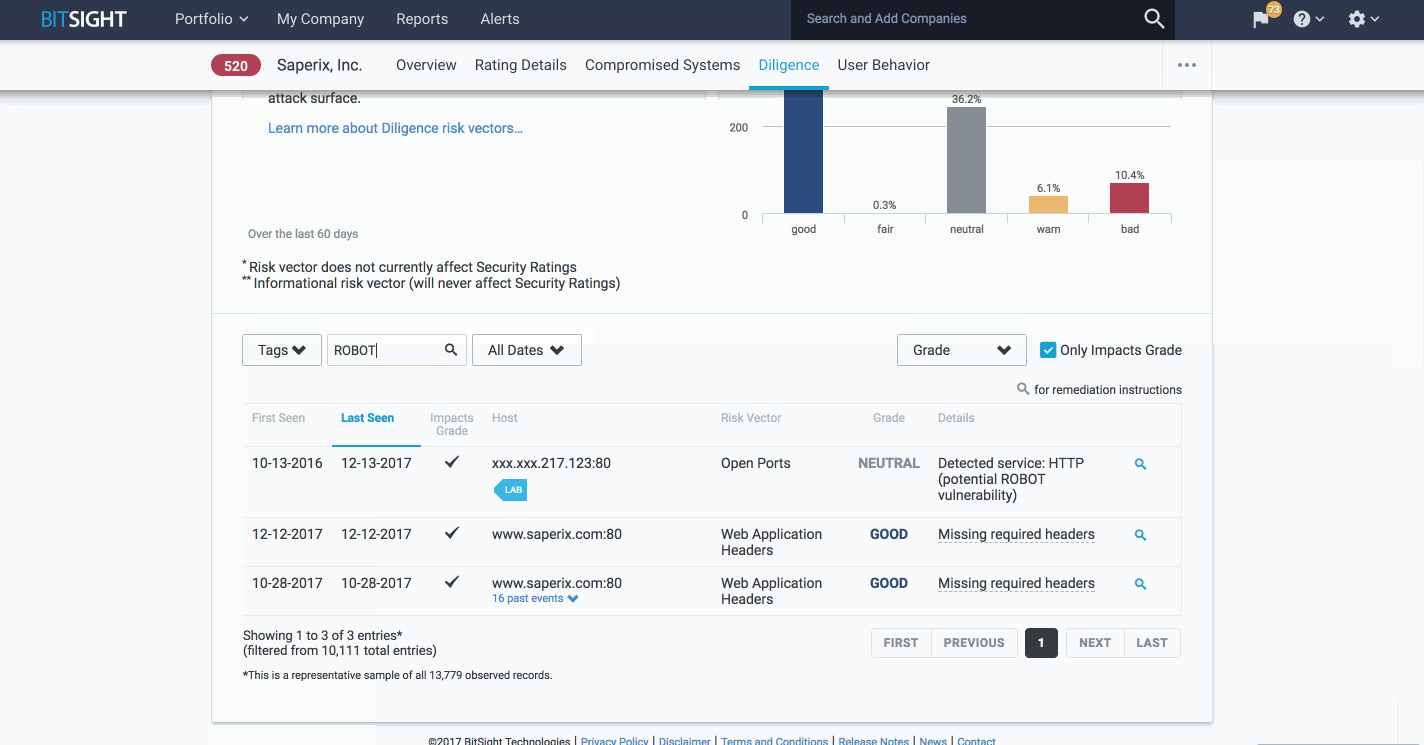
This new functionality to identify where ROBOT exists across your supply chain is very similar to the feature within the platform that allows organizations are potentially vulnerable to Struts attacks. Bitsight users can navigate to the Portfolio page and use the Vulnerabilities filter to find organizations potentially vulnerable to ROBOT attacks. They can then go to a company’s Diligence page and search for “ROBOT” to find the potentially vulnerable hosts.
This new feature provides valuable insight into the security posture of an organization (and its vendors). With global cyber attacks that exploit internal vulnerabilities, companies must keep track of the endpoints on their network and ensure that patching is enabled and up-to-date. Bitsight is leading the way in the Security Rating Services industry to provide insights like this to better equip security and risk professionals to reduce the cyber risk associated with their third parties and within their organizations.


