Bitsight Insights: Peer-To-Peer Peril & File Sharing Risks
Tags:
This is a two-part blog post. First, you'll discover the key findings in our latest Bitsight Insights report titled “Peer-To-Peer Peril: How Peer-To-Peer File Sharing Impacts Vendor Risk and Security Benchmarking.” In the second part, you'll read on to uncover our recommendations for mitigating the risks of peer-to-peer file sharing.
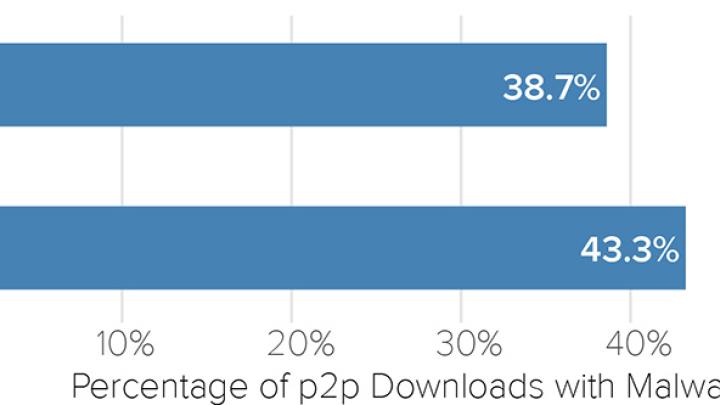
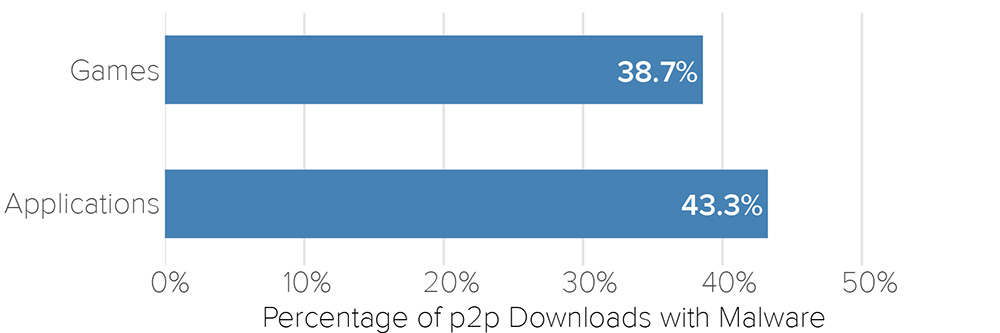
Today we published our latest Bitsight Insights report titled “Peer-To-Peer Peril: How Peer-To-Peer File Sharing Impacts Vendor Risk and Security Benchmarking.” For this report, Bitsight researchers analyzed peer-to-peer file sharing activity on over 30,000 companies to understand the risks of this behavior. Shockingly, when looking at specific files, Bitsight found that a whopping 43% of applications and 39% of games contained some form of malicious software. This underlines the key finding of this report: file sharing on corporate networks is a major malware threat for organizations.
In addition to this finding, Bitsight also learned some interesting facts about peer-to-peer file sharing:
-
23 percent of organizations analyzed have evidence of some P2P file sharing activity on their networks.
-
Adobe Photoshop and Grand Theft Auto V are the top torrented applications and games respectively.
-
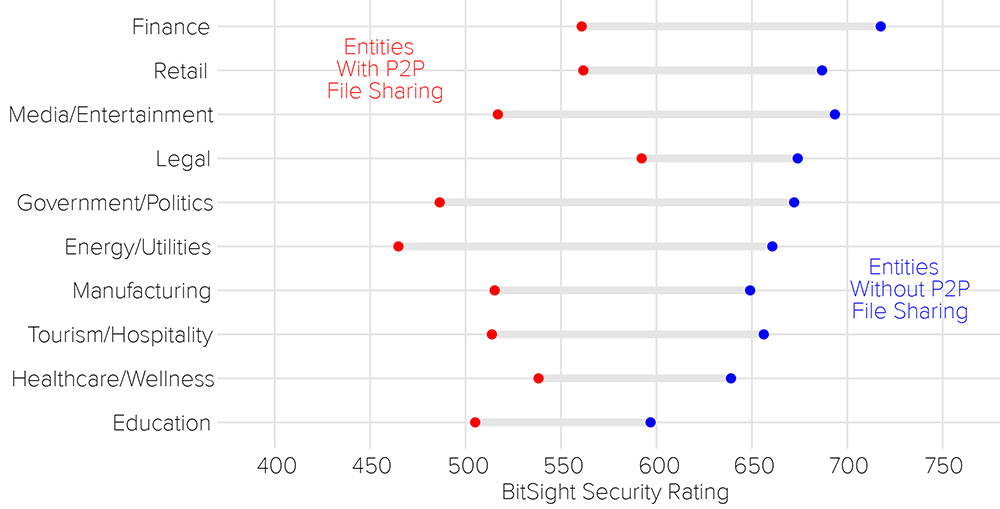
More than a quarter of companies in the Government, Education and Energy/Utility industries have observed peer-to-peer file sharing activity in the last six months.
-
Companies with more file sharing activity were likely to have more compromised machines due to botnet infections.
-
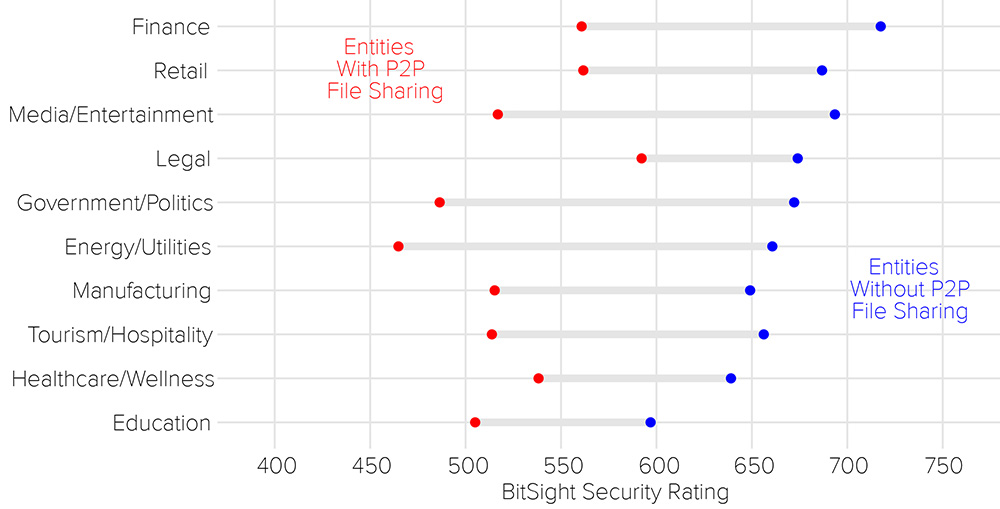
Companies with higher rates of file sharing were likely to have a lower Bitsight Security Rating across all industries. Currently, Bitsight does not factor file sharing information into our ratings as they are a beta risk vector. This finding underlines that companies with file sharing activity may have other issues (such as botnets, spam or diligence issues) on their network.
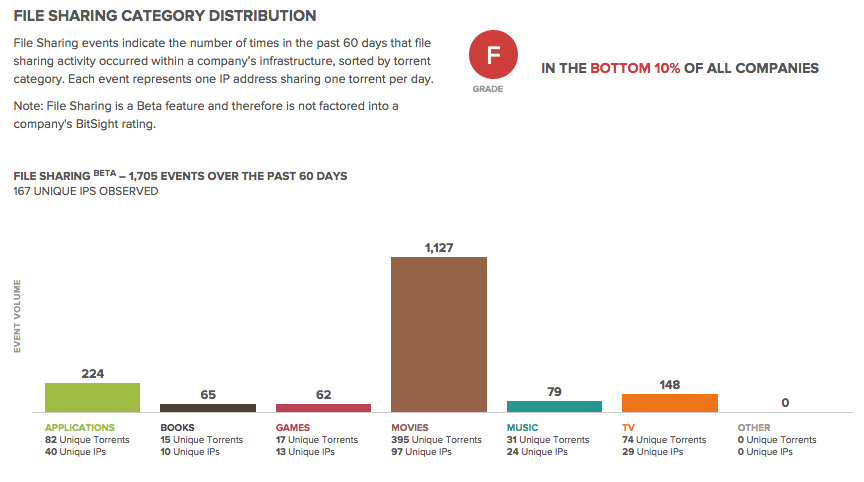
In addition to this report, Bitsight is also announcing our new File Sharing risk vector available to all customers in the Security Ratings portal. With this new feature, customers will be able to view file sharing of applications, books, games, movies, music, tv and other files on their network and their vendors’ networks. Along with this high-level view of file sharing, customers can subscribe to the File Sharing Forensics package that provides more granular information such as torrent name, event date, peer IP information and more - giving them the ability to identify this activity on their network and take action to remediate. As with all features in the Bitsight platform, customers can invite their vendors to gain temporary access to address file sharing in their vendor ecosystem. This expansion of data breadth further Bitsight’s capability as the global leading provider of objective, verifiable and actionable security ratings.
Part 2: Peer-To-Peer File Sharing Risks
It’s possible that your business is one in nearly four that has peer-to-peer file sharing activity occurring on its networks. In our latest report, Bitsight researchers found that out of 30,700 companies, 23% had file sharing activity occurring on their IP addresses. In addition to firewall protection and strict policies that prohibit peer-to-peer file sharing, it is beneficial to verify that there isn’t any file sharing activity occurring on your network. Since torrented files such as games and applications contain executable files that are susceptible to being infected with malware, the consequences are grave. Companies with more P2P file sharing are more likely to have an increased number of botnet infections, and thus, could have a higher likelihood of experiencing a data breach.
With boards becoming increasingly involved with cybersecurity, identifying and measuring peer-to-peer file sharing risk will be essential. Companies using the Bitsight platform can now benchmark their file sharing risk with their competitors, peers, and third parties in their portfolios.

Why Is This Valuable?
- Reporting: Telling your board that you are in the top 10% of all companies proves that you have effective controls and policies in place to mitigate the risks of peer-to-peer file sharing.
- Benchmarking Against Your Industry: File sharing occurs for a higher percentage of companies in some industries than others. Learning how you compare to industry peers can tell you a lot about the current security controls and policies you have in place given the nature of your industry.
- Best Practices: If a business partner or peer excels at preventing peer-to-peer file sharing, you may want to learn how about the controls and policies they have place. Reaching out to peers for advice is an easy way to learn what is effective for them.


