Learn how Bitsight Third-Party Vulnerability Detection empowers third-party risk professionals to find and remediate threats - including major security events - more quickly within their vendor portfolio. Identify exposure and mitigate risk more easily with critical insights into the impact on your organization’s third parties.
Video Transcript
Hi, I'm Jacob Mulberry and I work on the TPR M product team here at Bitsight. I'm really excited to share with you our latest enhancement to the product third party vulnerability detection. So you may be asking, what is third party vulnerability detection? With the continuous rise in zero day attacks, flooding organizations across the world.
It's become increasingly difficult to mitigate vendor exposure to critical vulnerabilities quickly and effectively. With third party vulnerability detection, we've simplified the process of not only finding the most pressing vulnerabilities in your vendor portfolio, but providing you detailed information to help manage and remediate more efficiently.
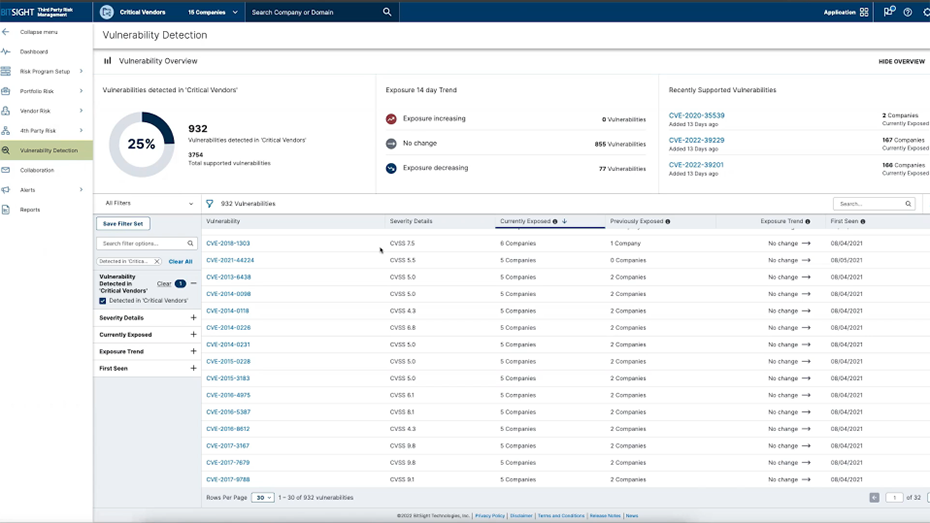
I'm thrilled to be introducing this new functionality with you today. So without further adieu, let me show you what we've built. You can easily access vulnerability detection from the left navigation panel in your TPRM app. Clicking into vulnerability detection will show you the vulnerability detection dashboard.
You can see a broad overview of how many vulnerabilities affect your tier, folder, or portfolio. You can also view trends for the past 14 days, as well as recently added vulnerabilities by Bitsight. Scrolling down to the vulnerability section, we've provided you easily access the most pressing vulnerabilities impacting your vendors.
You can now filter by severity details, currently exposed vendors or when the vulnerability was first seen. You can save any of these filter sets and come back to them and reference them whenever you need to. You can also search vulnerabilities by the CVE name or CVE number. Clicking into any vulnerability will open up the vulnerability details page. This will give a description about the vulnerability, the severity, as well as a remediation tip if there is one. You can also click on this link to go to the National Vulnerability Database and find any information that NIST has on the vulnerability. Clicking into any one of these companies will show you the evidence and the certainty of that evidence that Bitsight has found.
From here, you can quickly send an EVA or download this page to use for internal stakeholders or for external vendors. We're hoping to bring this new experience to vendor risk teams to help you stay ahead of zero day attacks, remediate risk more quickly, confidently adhere to growing regulatory pressure, and to build stronger vendor relationships.
We can't wait to hear what you think. Please visit us at bitsight.com to learn more and to give us your feedback.