Cyber attacks targeting national critical infrastructure can cause significant damage to national economies, public health, safety, and national security. These risks and threats continue to escalate in frequency and sophistication and organizations must be prepared.
Governments, national law enforcement organizations, and CERTS need a view of their cyber risk to improve security and protect critical infrastructure.
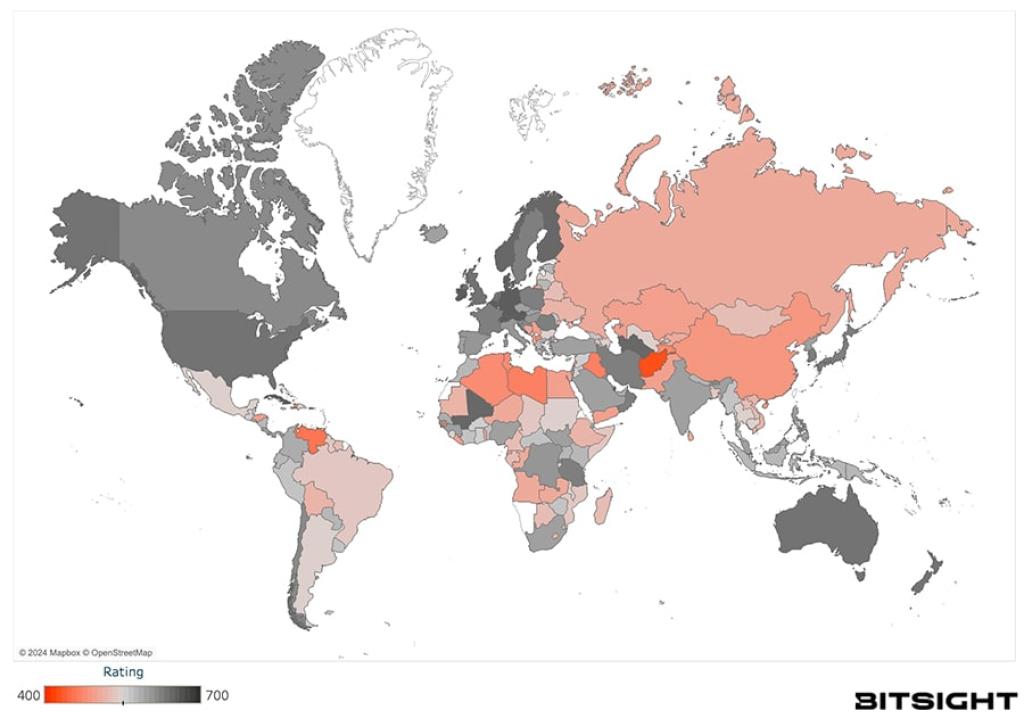
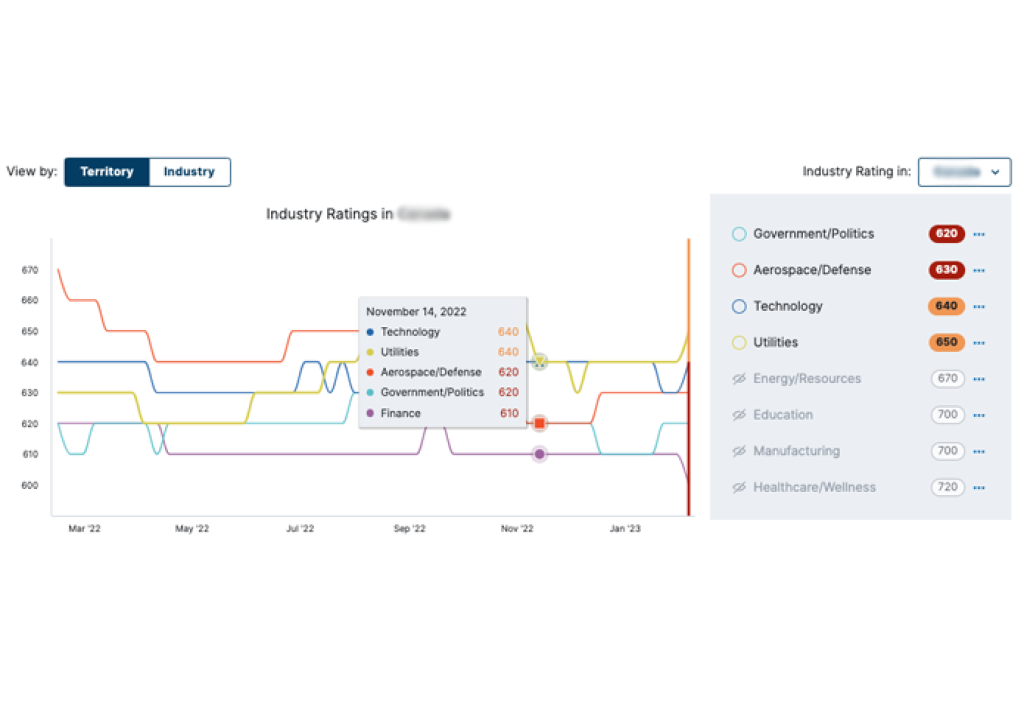
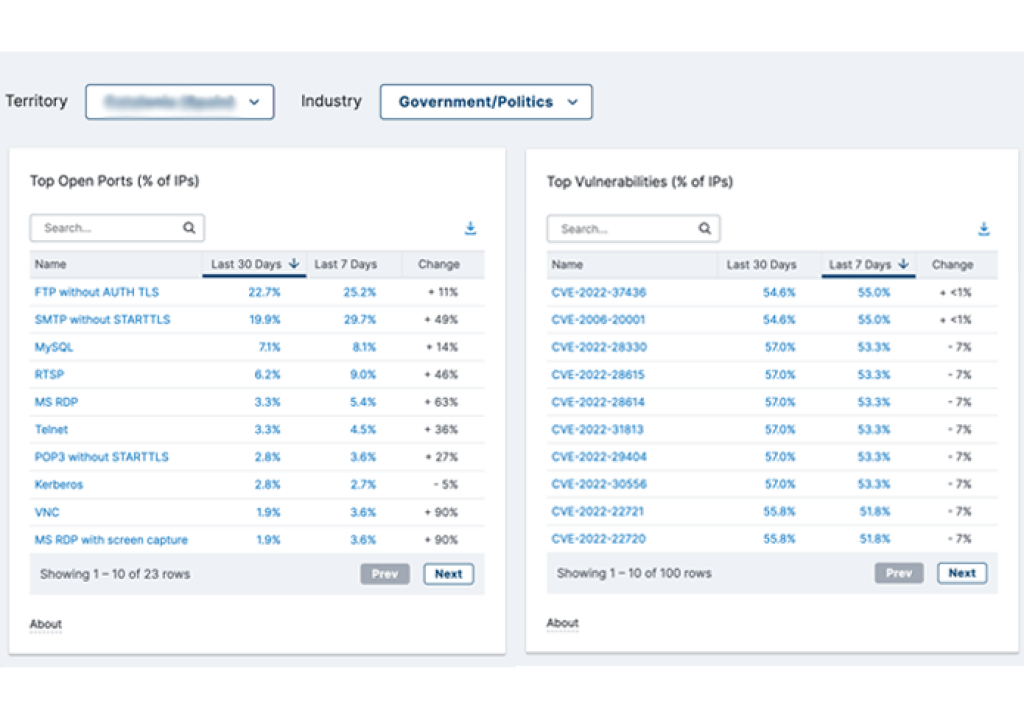
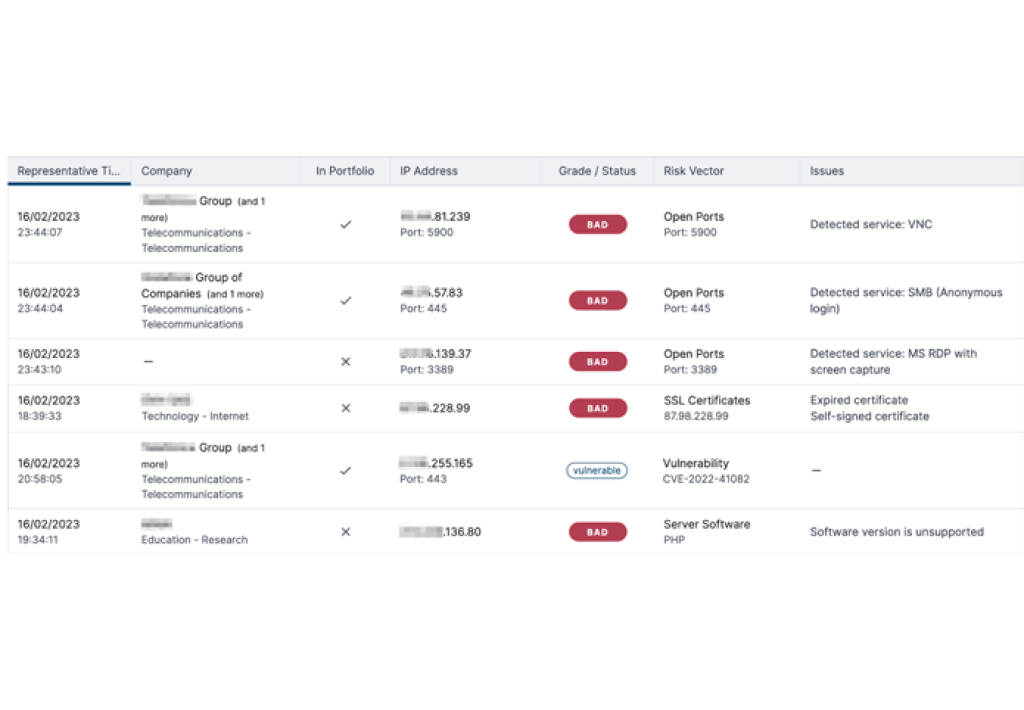
Bitsight empowers governmental agencies to continuously measure, monitor, and mitigate risks in your territory, key industries, and critical infrastructure companies. Bitsight provides the view and analytics to monitor and benchmark the security performance of your nation against others, compare different regions and industries, and pinpoint threats and risks occurring within a geographic area or strategic organization.