From Framework to Application: Identify With Bitsight
Tags:

This is the second post in a series exploring how Security Ratings can address key components of the NIST cybersecurity guidelines. You can read the first post here.
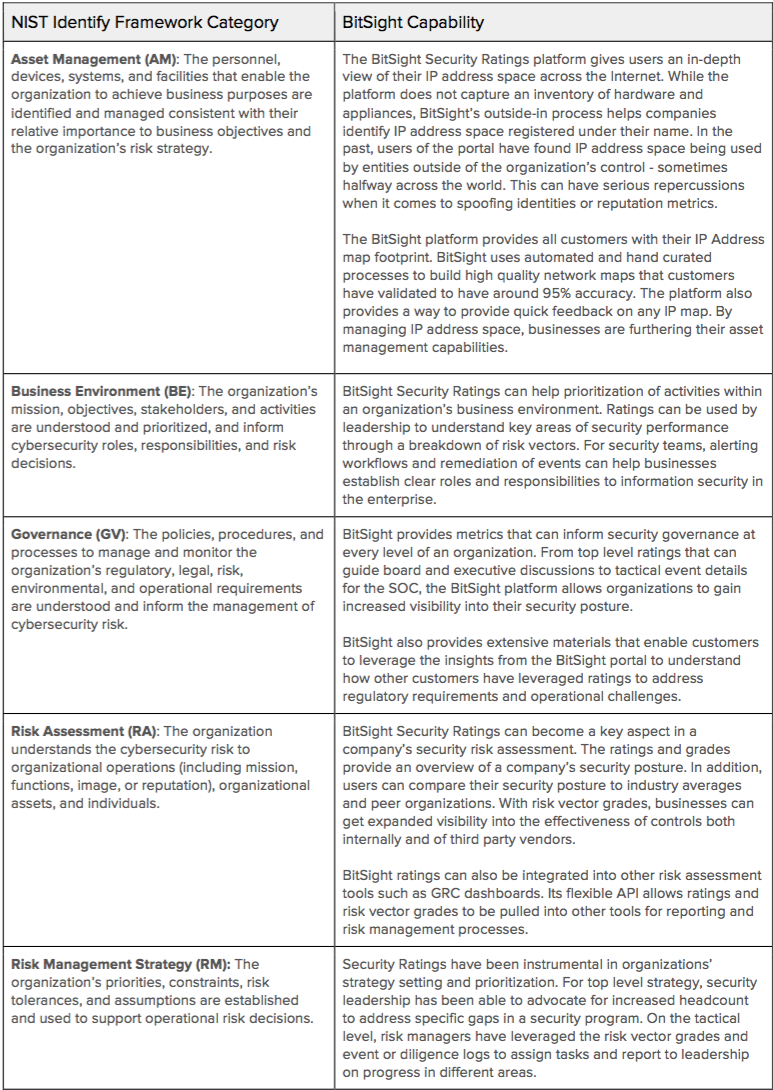
The NIST Cybersecurity Framework outlines five Framework Functions that organizations can use to better protect themselves against cyber threats. The first of these Framework Functions is Identify, which NIST describes as, “Develop the institutional understanding to manage cybersecurity risk to organizational systems, assets, data, and capabilities.” The Identify Framework Function is focused on the business context of security threats and defining a risk management strategy that maintains business continuity. Within this Framework Function, NIST further defines categories, subcategories and references from other widely adopted standards, such as COBIT (Control Objectives for Information and Related Technology) and ISO/IEC guidelines.
The NIST standards clearly place importance on the need for formalized risk management processes and communication of security posture throughout the enterprise. To address these challenges, many businesses have adopted Bitsight Security Ratings for Benchmarking in order to effectively communicate performance to stakeholders and identify area of improvement. Below Bitsight has provided a breakdown of how its product complements the NIST Identify Framework.