Bitsight Groma: Next-generation Internet Scanning
Tags:


Earlier this year, we announced Bitsight’s next-generation internet scanning, Bitsight Groma, and AI-powered discovery and attribution technology, Bitsight Graph of Internet Assets (Bitsight GIA). While these technologies work as partners in the Bitsight Cyber Risk Data Engine to create a dynamic map of internet infrastructure, it is helpful to separate them out to understand their unique contributions. This post will focus on developments in Bitsight Groma, and a later article will dive deeper into the Bitsight GIA.
Bitsight Groma continuously scans the entire internet to discover assets and identify an ever-growing set of security observations, such as vulnerabilities and misconfigurations. We developed Bitsight Groma to reduce dependence on unverified third-party data sources, minimize the mean-time-to-detect asset changes, and respond fast to changes in our customer environment.
Key Takeaways
- Available to all customers, Bitsight Groma improves scanning coverage, depth, and flexibility, enabling enhanced visibility into exposure and attack surface.
- Groma now plays a pivotal role in the data collection for highly visible diligence risk vectors, such as Web Application Security, Web Application Headers, SSL Configurations, SSL Certificates, and Open Ports.
- Groma has helped us increase our findings in these areas by up to 60 percent.
- Our enhanced scanning capabilities now extend to specialized industrial control systems (ICS) and operational technology (OT).
Why We Built a Proprietary Scanning Engine
Asset discovery and observation are core to what we do at Bitsight. While there are many sources of third-party information about internet-connected assets, as well as off-the-shelf vulnerability scanning technologies, investing in our own proprietary scanning architecture has unlocked numerous advantages that directly benefit our customers:
- We can aggressively pursue greater breadth and depth of scanning coverage.
- We have complete control over scanning frequency, allowing us to minimize mean time to detection of new vulnerabilities and changes to customer environments.
- We can adapt and evolve our scanning capabilities rapidly based on new customer requirements and innovations and insights from our team of 30+ security researchers.
Groma’s Capabilities and Scale
Bitsight Groma is continuously scanning the internet. This gives us a much more accurate and up-to-date view of our customers’ IT assets, along with those of any third and fourth parties that they interact with. It also allows us to observe any positive or negative changes to the risk posture of these entities much more rapidly.
Groma’s scanning activities presently encompass:
- 40 million-plus monitored organizations
- 250 million-plus host names
- 4 billion-plus routable IPv4 and IPv6 addresses
The importance of the continuous scanning, and breadth of Bitsight Groma scanning, is the ability to find assets changes or new assets fast. A recent study from Greynoise.io found that Bitsight can find new assets within 2 hours of them becoming visible on the internet.
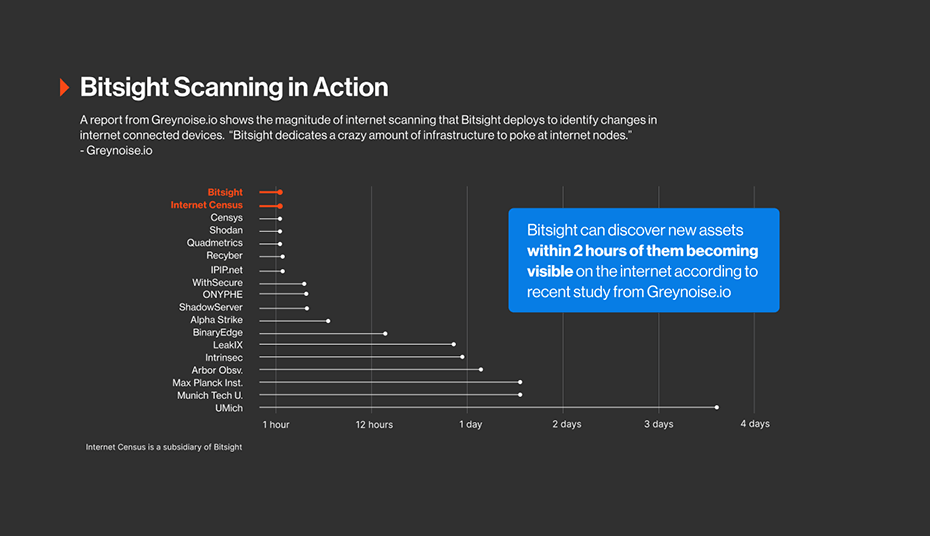
This increased scale has enabled significant leaps in the coverage we are able to achieve. For example, Groma has enabled us to triple our vulnerability coverage compared to just one year ago. Also, we have increased our hostname coverage drastically (5x) due to the recent enhancements in our scanner infrastructure.
We’ve also been able to tailor our scanning activities to the specific data categories that are essential for delivering Bitsight’s product offerings. One notable example is the significant advances we’ve made with scanning ICS and OT protocols used for the automation of processes (industrial or other), such as for building automation, power-system automation, automatic meter reading, and vehicular automation. Groma now supports the 8 most widely used OT protocols, including Modbus, BACnet, Ethernet/IP, DNP3, and growing this list continues to be a major area of focus for our team.
Groma’s Early Impact on Security Observation
In addition to enhancing our overall entity and asset coverage, Groma has also yielded significant improvements in the breadth and depth of our security observations across the various diligence risk vectors we measure, such as web application security, SSL practices, software vulnerabilities, and patching cadence.
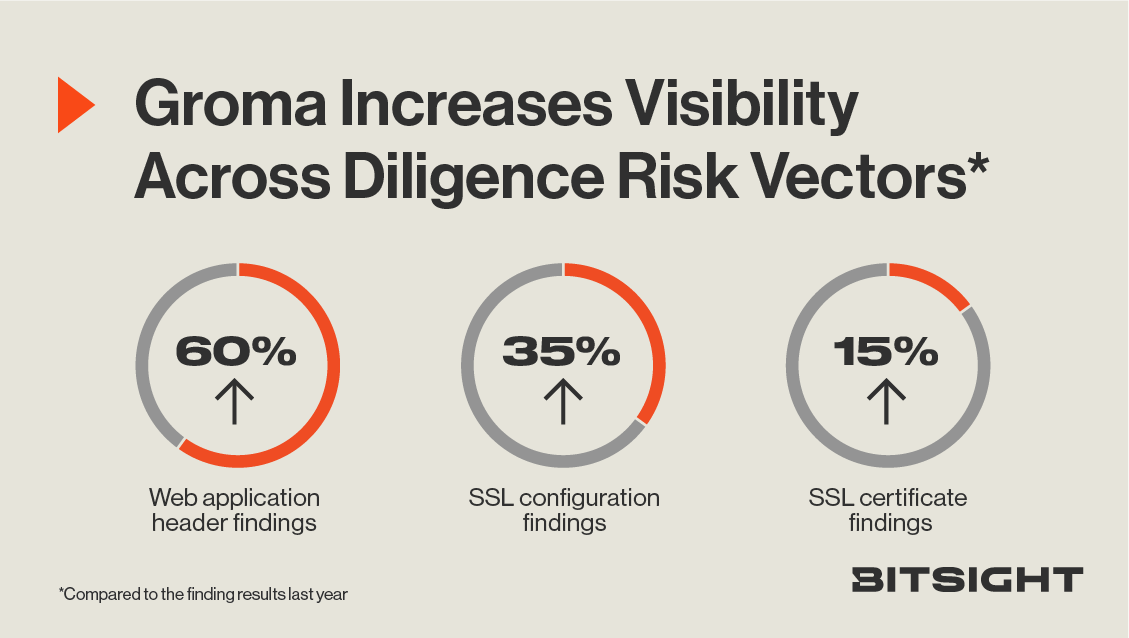
When compared to last year, we’ve been able to observe:
- 60 percent more web application header findings
- 35 percent more SSL configuration findings
- 15 percent more SSL certificate findings
We’ve also tripled the number of Common Vulnerabilities and Exposures (CVEs) covered by our scanning efforts and have achieved 21 percent coverage of CISA’s Known Exploited Vulnerability (KEV) catalog.
How Higher Data Fidelity is Enriching Bitsight’s Products
By increasing the coverage and frequency of our scanning data, Bitsight Groma has already unlocked significant value for our customers. Perhaps the best example of this is our 2024 Rating Algorithm Update (RAU), which reduced the lifetime of Patching Cadence findings from 300 days to 90 days. This is a significant benefit to customers who focus on this area, since improvements they make to their patching efforts will be reflected in their Bitsight Rating much faster.
Thanks in large part to the enhanced capabilities of Groma, we were able to make this improvement while maintaining a high level of correlation between our Patching Cadence measurement and real-world security outcomes. Our data science team shared a deeper dive into the analysis and data behind this change in a recent blog post.
The enhanced insights into assets and risks that Groma provides are also enriching the data behind our External Attack Surface Management, Cyber Governance and Reporting, Third Party Risk Management, and Cyber Data Solutions in numerous other ways that our customers now benefit from directly every day.
What to Expect Moving Forward
While we are proud of the impact that Groma has already made on customer value, our team continues to pursue new innovations aggressively. In the coming months, stay tuned for:
- Even greater increases in the breadth of Groma’s scanning capabilities.
- Accelerated response to major security threats through more sophisticated automation.
- Further increases in our CISA KEV CVE coverage.
- Continuing expansion of our already differentiated coverage of ICS and OT protocols.
Learn More About Bitsight’s Data Discovery, Attribution, and Observation Capabilities
For a more comprehensive overview of Bitsight’s internet scanning and AI-based graphing capabilities, download our white paper, “A Data-Driven Approach to Asset Discovery and Risk Measurement.”
You’ll learn how Bitsight Groma and Bitsight Graph of Internet Assets (GIA), our AI-powered graphing engine, work in concert to build a living map of the world’s digital ecosystem and capture deep insights about organizational risk posture.
Download your copy today.


