New! The Security Ratings report is now the Executive Report. Request your report to see enhanced analysis such as your rating, likelihood of ransomware incidents, and likelihood of data breach incidents.
Bitsight’s Newest Risk Vectors Highlight Innovation in Security Ratings

Within the Bitsight Security Ratings platform, we analyze risk vectors specifically chosen to help organizations identify and manage risks across their own networks and the networks of their third parties. Over the past few months, Bitsight has added new risk vectors to enhance the insights across the “spectrum of risk” and provide a more comprehensive picture of an organization’s security posture. These risk vectors will not be factored into our rating calculation until we update and expand the rating algorithm once every year. However, they still provide extremely valuable information to Bitsight users. As new threats emerge, Bitsight understands the important role that these threats play in the security ratings industry. This is why we continuously add to our list of risk vectors — it is critical that security ratings services are dynamic in nature and able to incorporate the identification of these risks into their service.
In this post, we’ll take a look at the newest risk vectors that Bitsight Security Ratings addresses.
Endpoint Security
Bitsight now provides data on the security of endpoints connected to your corporate network. These include desktop or mobile devices that may be running outdated operating systems and browsers. Bitsight identifies the software and operating systems on these endpoints to enable organizations to understand which might lead to a data breach. This level of analysis is extremely important if you have trusted vendors accessing your company’s sensitive data through outdated systems. Bitsight has found that organizations running a majority of their machines on outdated browsers or operating systems are more likely to experience a publicly disclosed breach, which could ultimately impact your business. Bitsight not only gives you visibility into your organization’s endpoints, but also your vendors’ endpoints.
The graphic below shows the percentage of companies that experienced a data breach and their use of outdated operating systems and out-of-date Internet browsers.
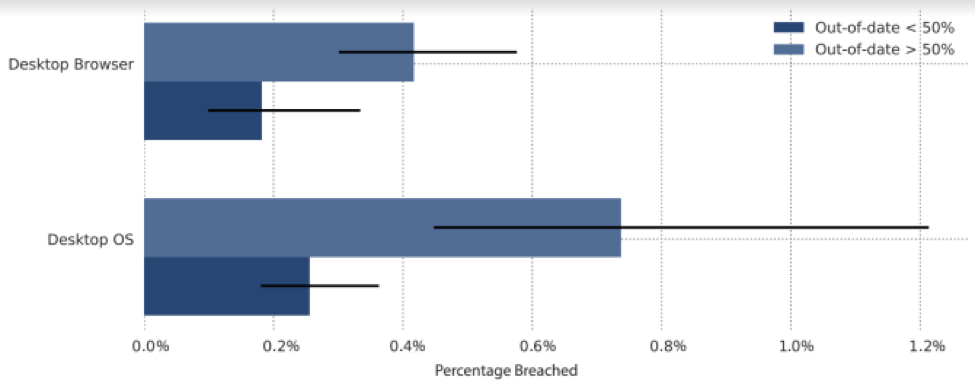
Desktop Software
Bitsight compares the desktop devices' version of OS and browser with currently released versions and software updates available for those systems, and determines whether those systems are supported or out of date. Unsupported desktop devices in an organization's network present a greater risk of system failure (if vendor devices are not being maintained), disruption of business continuity, and may allow attackers to exploit unpatched vulnerabilities and gain system access.
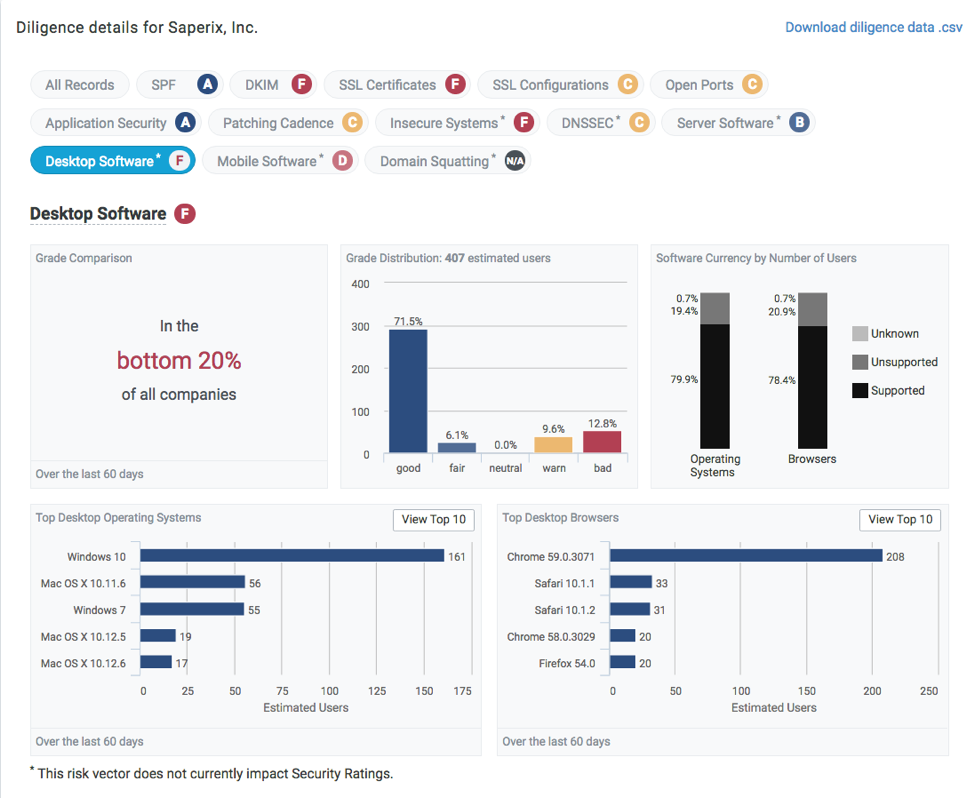
Mobile Software
Unsupported mobile devices in an organization's network present the same risks of system failure, business disruption, and exploitable vulnerabilities. Outgoing communications from mobile devices include metadata about the device's operating system, device description, browser version, and description of applications. Bitsight compares version information with currently released versions and software updates available for those systems, and determines whether those mobile devices are supported or out of date.
Insecure Systems
Bitsight identifies any insecure systems connected to your corporate network. Using Bitsight Security Ratings, organizations identify whether there are systems connected to the network that are insecure by nature. Insecure Systems shows which endpoints inside an organization are communicating with an unintended destination. The software in these endpoints may have been tampered with or misconfigured to communicate with a remote server that, if captured, may allow attackers to inject code, or extract sensitive data. For instance, Bitsight researchers recently discovered that millions of Android devices were vulnerable to a Man-in-the-Middle attack. They were able to identify a vulnerability that was tied to many companies’ networks. With Bitsight Security Ratings, organizations can quickly identify and continuously monitor insecure systems on their own network or on the network of their third parties.
Domain Squatting
The Bitsight Platform reveals any instances of domain squatting — this occurs when similar domains mimic that of your company, but are used to carry out malicious attacks. Hackers will create fake websites that closely imitate both the URL of another site, which can then cause visitors to enter sensitive information in the wrong place. For example, you might receive an email asking you to visit your bank's website, but the URL you navigate to doesn't seem quite right; you know something suspicious may be happening. There may be numbers instead of letters, or missing characters — consider "yahoo.com" versus "yah00.com.”
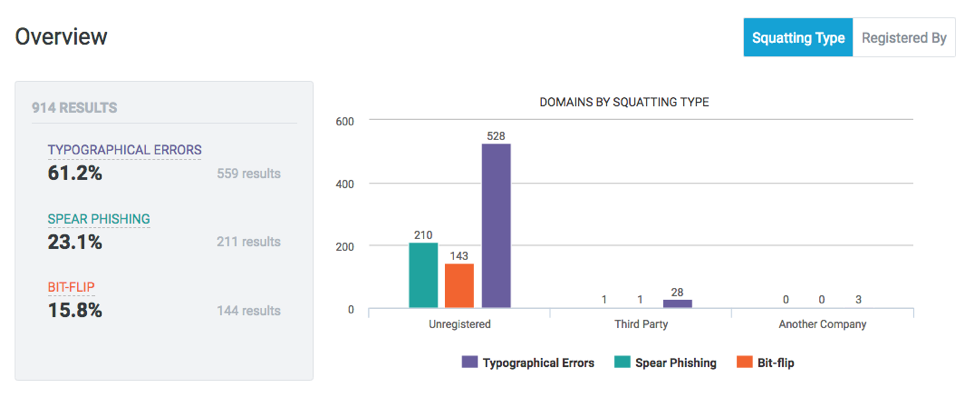
This can be potentially harmful to your customers if they mistake it to be your own site and enter their credentials or other sensitive information through these domains; criminals may steal those credentials. This is a particularly large threat for larger companies with high-traffic websites, although even smaller organizations can be targeted for these attacks, which cause a breach of sensitive data. Organizations monitor whether they have a domain that should have been registered to them but was overlooked; Bitsight includes information about whether that domain was registered to a known organization, another third party, or is unregistered.
When it comes down to it, this is an issue of reputational risk. That “lost” domain can prove to be harmful for both an organization and its customers. It’s important for companies to also understand that evaluating third party vendors’ domains can be a critical part of a cyber security and risk management program. For instance, your organization may use a web portal to share sensitive information with trusted vendors. Monitoring the risk of domain squatting becomes a critical part of adequate vendor risk management.
Server Software
Bitsight monitors server software to inform companies about servers with software packages that are no longer supported and may pose vulnerabilities to their corporate network. Organizations can use this information to understand the applications that are in use by their third parties and identify potential vulnerabilities. Consider the Target breach of 2013, where post-breach investigations found that the company was using outdated servers — one of many factors in this attack.
Conclusion
These important new risk vectors provide a more comprehensive picture about the security controls and policies of an organization. With global cyber attacks often exploiting outdated software, companies must keep track of the endpoints on their network and ensure that software is up-to-date and properly configured. Bitsight is leading the way in the Security Rating Services (SRS) industry to provide this granular detail to better equip security and risk professionals to reduce risk.



