Bitsight TRACE is Bitsight’s security research and intelligence team. Comprised of researchers and threat analysts with deep cybersecurity experience, the team investigates and publishes information on emerging malware, vulnerabilities, and threats.
Security Research
Bitsight TRACE Research
Bitsight TRACE researchers leverage Bitsight’s extensive cyber data collection, mapping, and attribution technology to not only investigate security incidents, but often times identify a range of vulnerabilities and threats. The research is used throughout the security community to improve cyber readiness.
Recent Bitsight TRACE research

Bitsight Research

Bitsight Research
security research report
State of Cyber Risk and Exposure 2025
90% of security leaders say managing cyber risk is more difficult now than it was five years ago. This year’s report reveals what’s driving the complexity—and what forward-thinking organizations are doing to gain visibility, improve prioritization, and align security with business goals.
Explore exclusive findings from our global survey of 1,000 cybersecurity and risk leaders to learn how leading enterprises are transforming cyber risk intelligence into better business outcomes.

Security research report
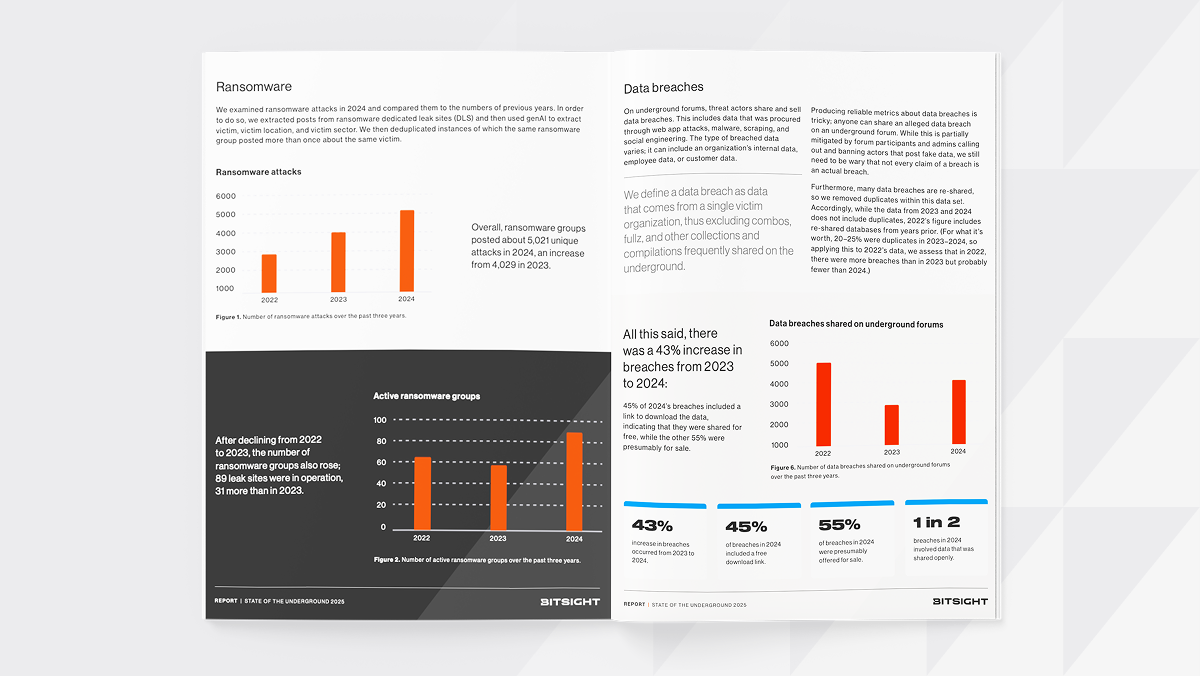
State of the Underground 2025
Ransomware is up. Credential leaks are rising quickly. Malware is diversifying. This year’s report drills into how cybercriminals are evolving—and what defenders must do to keep up. We analyzed millions of endpoints, credentials, and forums to expose the realities of the cyber underground in 2024. This isn’t theory—it’s what’s actually happening right now.
security research report
Researching Exposed Cameras in the Wild
In our latest research at Bitsight TRACE, we found over 40,000 open, publicly accessible network cameras, streaming live footage from offices, factories, medical facilities, and even private homes. We first raised the alarm in 2023, and based on this latest study, the situation hasn’t improved. These cameras — intended for security or convenience — have inadvertently become public windows into sensitive spaces, often without their owners’ knowledge.


security research report
Under the Surface: Uncovering Cyber Risk in the Global Supply Chain
Your supply chain isn’t just a series of links—it’s a vast, tangled web of dependencies, many of which have weak security. This report uncovers the critical but often-overlooked providers that could be the next cybersecurity weak spot, along with data-driven insights to help you mitigate risks before they disrupt your business.

Security Research Report
A Global View of the CISA KEV Catalog: Prevalence and Remediation
Bitsight TRACE research analyzing trends and insights of the Cybersecurity and Infrastructure Security Agency’s Known Exploited Vulnerabilities (KEV) Catalog. In this comprehensive report, Ben explores:
- Prevalence of KEVs across organizations, geographies, and verticals
- Average KEV remediation times and compliance with CISA deadlines
- Differences in KEVs known to be part of ransomware vs other CVEs
