
Welcome folks! It’s 2024 and we here at Bitsight are kicking off a series of short informative posts on events that caught our attention as cognition authorities1 each month. We’re excited to report on the interesting things Bitsight found.
So, what was a thing that happened in the last 31 days that fits the above? For me, it was the publication (to both various CVE repositories and the CISA Known Exploited Vulnerabilities Catalog) of two new Ivanti [Connect|Policy] Secure vulnerabilities: CVE-2024-21887 and CVE-2023-46805. For those unfamiliar, Ivanti Connect Secure (previously known as “Pulse Secure Connect”), is a SSL VPN product, while Ivanti Policy Secure is a Network Access Control (NAC) solution. Together these make up the locked gate (VPN) and gatekeepers(NAC) to an organization's network castle, only allowing those authorized to enter, and once inside controls where they are allowed to be. That means any vulnerability for which:
Kind of a big deal.
Beyond the basic facts of the vulnerability, there were (are ongoing) a bunch of circumstances that made this “very bad”: these vulnerabilities affect “all supported versions”, promised patches got delayed more than two weeks, installing the patches potentially caused a race condition in the device, and the download portal was unavailable for a bit. All this was such a big deal that a few days later CISA went so far as to issue an emergency directive saying “patch like NOW, check your systems, and reset any auth keys you might be using”. On top of that, there was widespread reporting of exploitation in the wild, with Chinese affiliated APTs even getting in the game. CISA even went so far as to update their emergency directive indicating “these things shouldn’t even be plugged in until you can fix them”.
If some of the words above are ringing a bell to you, it’s because this isn’t their first rodeo. There are 57 CVEs for those two pieces of software published in NVD (including those two), and there was that little incident where a Chinese APT breached multiple government agencies using a vulnerability in Pulse Secure. We shouldn't be too hard on Ivanti though. As we mentioned, their software is the gate and gatekeeper for an organization's network, meaning it’s Internet-facing and a tempting target to bad actors out there. In fact, it shows up in other threat reports (Figure 4, page 7) as something actors are frequently targeting.
Widespread Prevalence: An Analysis of Firmographic and Geographic Impact
So what info might Bitsight have on these CVEs? Well, first of all, we published some news about it, and jumped to battle stations to investigate what percentage of the internet might be affected. First, it’s important to know the history, so we took a look at what we found with the new CVE in context with the other Ivanti CVEs that Bitsight tracks (Figure 1). The prevalence data is all from January 31, 2024.
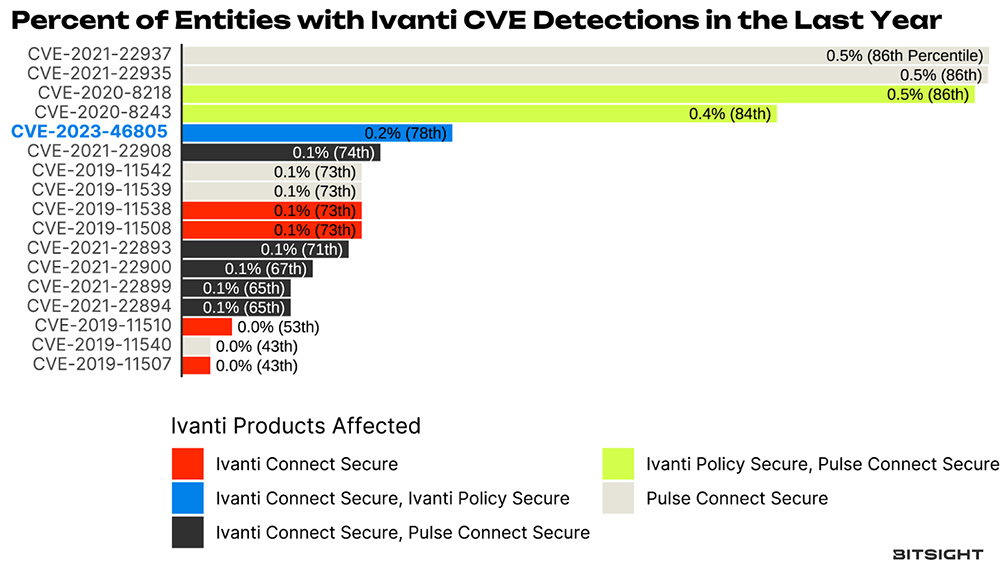
Figure 1 Pulse secure CVE detection rates, our new CVE highlighted with blue text.
While the overall percentages might not be overwhelming at first blush (less than 1%), these are substantial in terms of the overall percentile, with many in the top quartile and nearly all in the top half of prevalence for vulnerabilities we detect2. After all, there is a huge zoo of software out there, and while some things are a monoculture (looking at you Chrome), there is quite a bit more variety for stuff like VPNs.
How is this prevalence distributed across various industries? That’s easy enough…
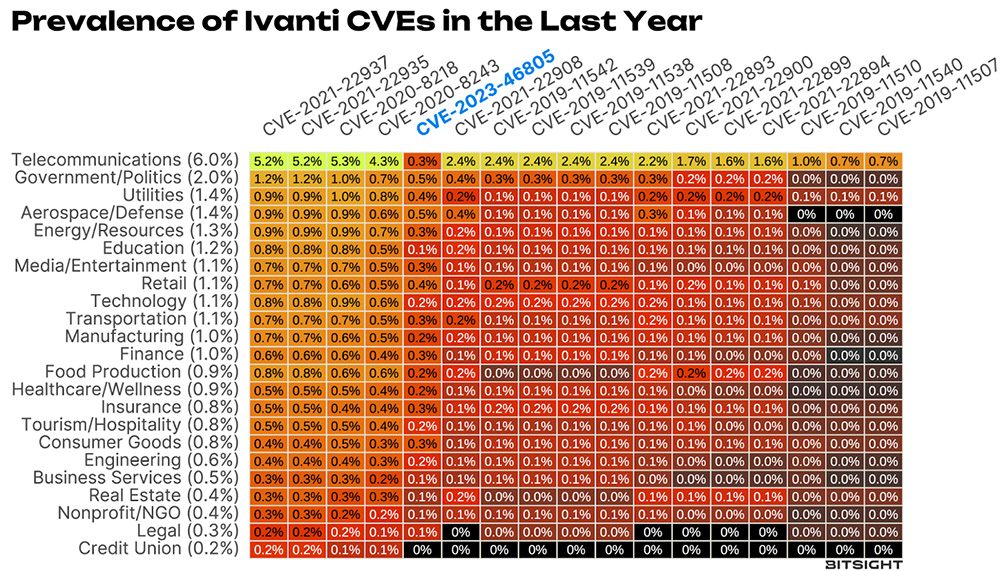
Figure 2 Prevalence of Pulse/Policy Secure CVEs in 2023 across industries. Numbers in parenthesis are the overall rate for that industry. This excludes service providers; if it didn’t, that top row would be white hot.
The fact that the six out of the top seven rows which have the highest prevalence of these CVEs are what could be called “critical infrastructure” is concerning and should raise some eyebrows. Our new vulnerability is pretty middle of the road, as it was in Figure 1, though it’s interesting to note that it is lower than we might expect in telecoms. Maybe they’ve learned some lessons.
This of course raises the question, is there anywhere this new vuln has higher than expected occurrence? We didn’t find anything that made our eyes bug out at the industry level, but at geographic level, things are a bit more interesting (Figure 3).
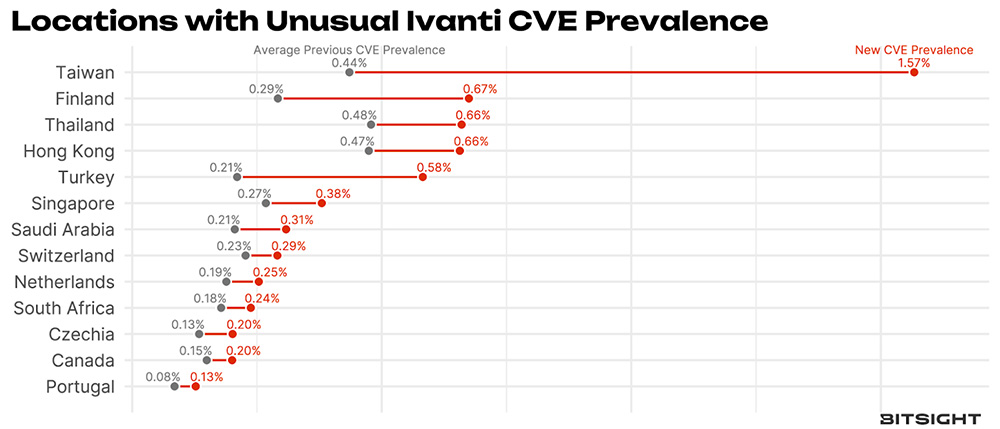
Figure 3 Average prevalence of older Ivanti Connect Secure vulnerabilities compared to the new vulnerability (CVE-2023-46805).3
We won’t go so far as to make wild inferences, but it does seem that Southeast Asia (Taiwan, Thailand, Hong Kong and Singapore) have unusual concentrations, with Finland and Turkey also in the mix.
But do we think CISA was right in their concern and directive to “unplug” everything? In a word, “Yes”.
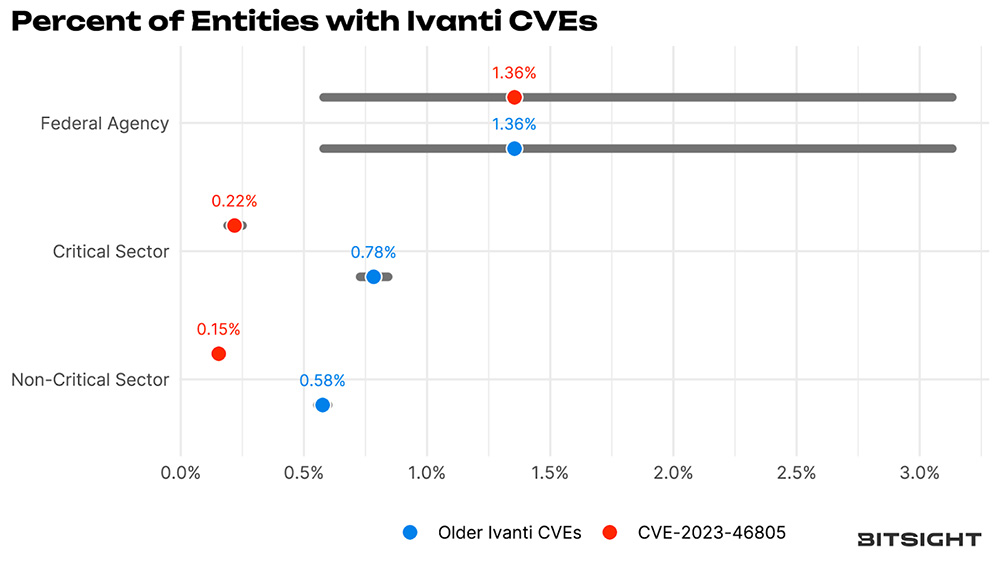
Figure 4 Ivanti prevalence among Federal Agencies, Critical Infrastructure and Non-CISA Critical Infrastructure
Federal agencies were nearly 9X more likely to be affected by CVE-2023-46805 than their non-critical counterparts.
The error bars are pretty wide in the above, as there are a limited number of federal agencies that actually are required to comply with emergency directives. Given those wide bars, those federal agencies aren’t more exposed with the older vulns, but they are for the new Ivanti CVE. So, yes, “unplug this NOW”, likely was prudent advice. The data in Figure 4 was from a scan we ran on January 31st, but by February 4th, we no longer detected the Ivanti CVEs on any federal agencies.
Exposure is one thing, but actual exploitation is another. There was quite a bit of hubbub given the series of events, and we wanted to investigate whether that made people hop to it. Early rough detections by others using Shodan indicated at least 15k vulnerable instances out there. We ran our own scans over the weekend (finishing up on February 4th, a lag time of three weeks) and found ~5k vulnerable IPs, and that seems both promising and concerning. On one hand, folks seem to be taking things offline, on the other that’s still a lot of vulnerable instances.
But vulnerability is only half the battle, there have been a number of indications of exploitation, so Bitsight researchers did some further tiptoeing in vulnerable IP space to see if attackers had gotten there first. We found that 2.4% of those vulnerable IPs had the WARPWIRE webshell running, and most (84%) of those had evidence of weblog exfiltration that was described by Mandiant. While this isn’t a lot, note we are only checking for one particular webshell, and often attackers will “close the door behind them” and patch up a system they compromised to keep other, competing attackers out.
So what’s this mean for you Jane Q Security Professional? Well, if you run any of the Ivanti products, get that stuff updated (especially before you connect it back to the Internet), and maybe look around to see if anyone unauthorized has been mucking about in your network. But who am I kidding? If you are smart enough to be reading this, you’ve already done that. It’s also worthwhile to check if anyone you rely upon uses that software (fourth party risk is so in right now), and if they are, maybe take the necessary precautions to make sure attackers can’t move from that infrastructure to yours.
I am sure this month we’ll have a nice Valentine’s gift in the form of someone using the Internet for evil, and we look forward to chatting about it here.
For Bitsight Customers
Bitsight customers can identify exposure in their first- and -third-party digital ecosystems in either the Continuous Monitoring or Security Performance Management (SPM) pages of the Bitsight product.
CISA has issued a directive for federal agencies to disconnect all instances of Ivanti Connect Secure and Policy Secure by February 2nd and perform additional analysis and remediation on affected systems. Due to ongoing issues, including delayed patch availability, evidence of active exploitation, reports of failed fixes, and the discovery of additional vulnerabilities, our cybersecurity experts strongly advise taking CISA recommended actions. Please refer to Bitsight’s Knowledge Base (KB) article for updates.
If you believe you may have an issue, please contact Bitsight so we can help.
1Read “thought leaders”
2Why only 17 of the 56 published? Bitsight takes care to scan for vulnerabilities that we can be very confident in detecting and those that, when detected, won’t break anything on the devices we are scanning.
3 We’re doing a bit of filtering here and only reporting countries for which we can be confident of the prevalence values and have a high ratio.