Escalating cyber threats are swirling around your organization’s digital footprint, looking for vulnerabilities. Recent incidents involving SolarWinds, Capital One, and Colonial Pipeline show the damage they can cause. And the financial, operational, reputational, and regulatory impacts of a cyberattack can be significant and lasting.
That doesn’t change one simple question: how do you get your arms around the challenge?
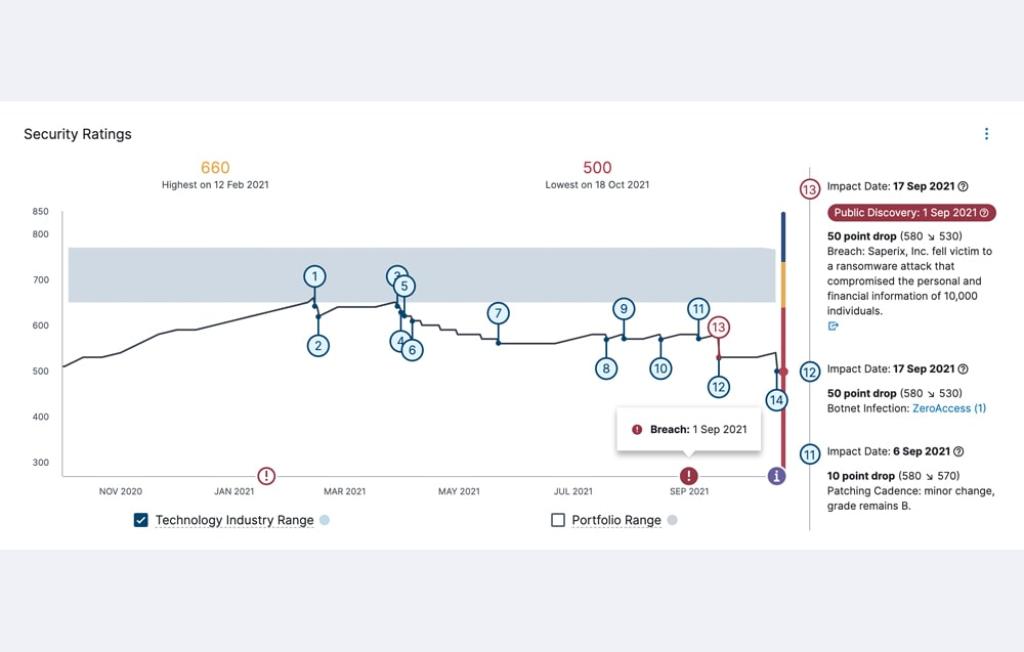
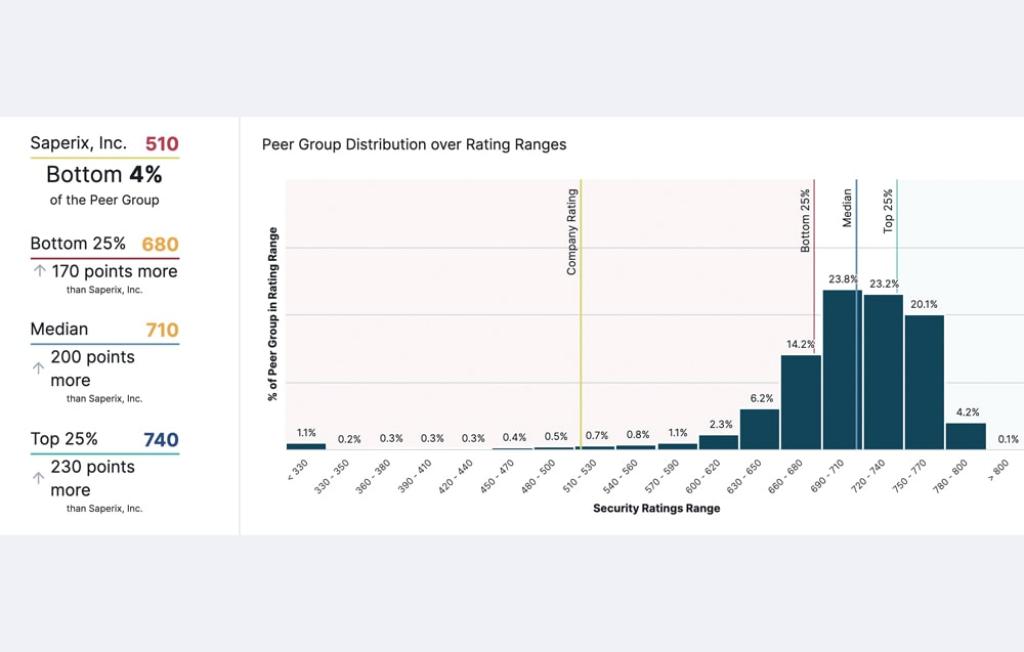
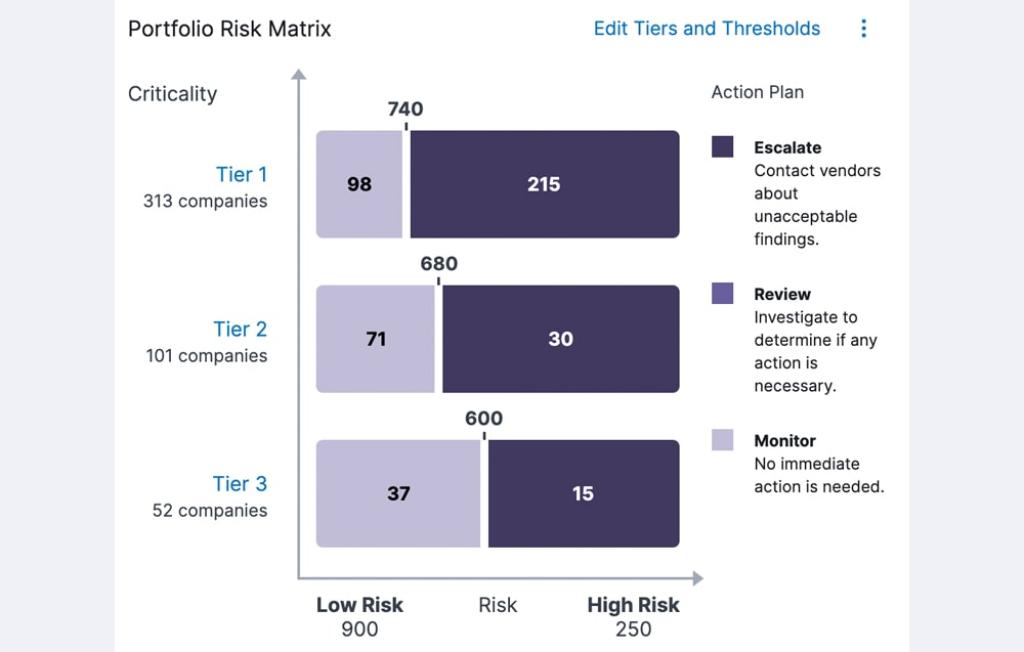
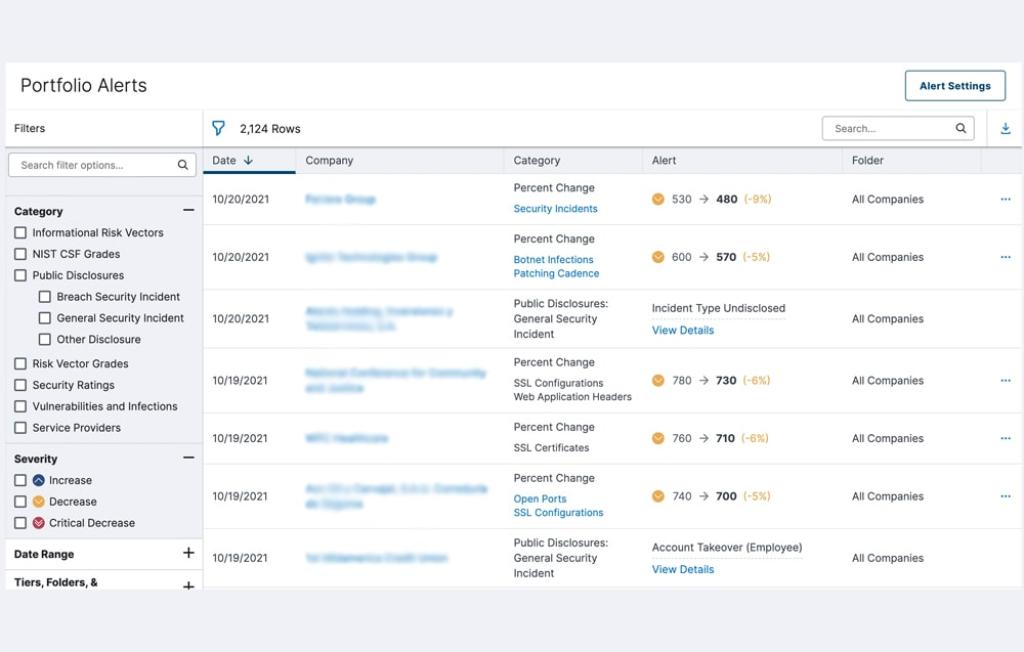
The answer: continuous monitoring with Bitsight. Continuously monitoring your cybersecurity posture lets you keep a constant check on your propensity for risk – in your own organization, and across your supply chain. With automated insights and near real-time alerts, you can bring your stress level down while boosting your security level up. Save time and target your remediation efforts where they’re needed most when you have the right tools.
Think of it as a heart rate monitor for cyber risk.