Access resources to learn about cyber risk management, security ratings and how to minimize cyber risk.
Resources.
Access resources to learn about cyber risk management, security ratings and how to minimize cyber risk.

What are the major cybersecurity trends for 2023? Download this webinar to hear insights from Moody’s analysts and Bitsight’s cyber risk experts as they discuss their latest research and look ahead to 2023.

With Bitsight VRM, you can proactively manage increasing risks by automating vendor risk management throughout the entire lifecycle; from due diligence and vendor onboarding, to reassessment and ongoing monitoring.

Security Performance Management
Get this ebook to learn how each of our seven advanced analytics enable you to achieve your goals in cyber risk governance, management, and assurance.

Gain strategies to identify and overcome vendor exposure—and examples of how we’re helping customers address concentrated risk.

Bitsight's CEO Steve Harvey, Moody's Corporation's President and CEO Rob Fauber talk about how the two companies are working together to transform how the global marketplace measures and manages cyber risk.

Security Performance Management
A study by the Marsh McLennan Cyber Risk Analytics Center found that poor performance in many Bitsight analytics is statistically significant and correlated with the likelihood of experiencing a cybersecurity incident.

Download our datasheet to learn how Bitsight Third-Party Vulnerability Detection can elevate your vendor risk remediation strategy and highlight major security vulnerabilities quicker than ever before.
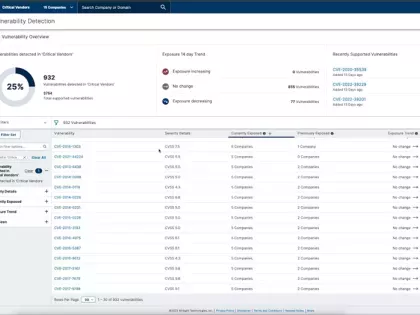
Learn about our latest functionality that helps organizations detect, manage and remediate zero day events at scale.
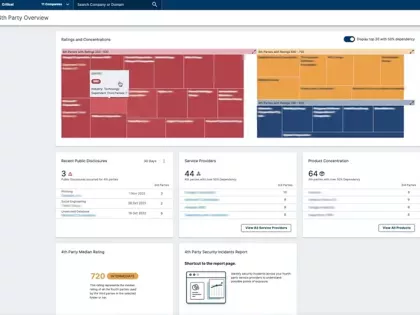
Learn about the latest enhancements we’ve made to our Fourth-Party Risk Management solution to help organizations gain better visibility into the concentrated risk within their extended vendor ecosystem.

Struggling to defend your organization against cyber attacks? Wondering how to prioritize limited resources?

Join Bitsight and ProcessUnity, on a journey that highlights TPRM trends, and challenges and introduces a data-driven approach through ProcessUnity that is fast, frictionless, and provides actionable integration to help modern organizations make smarter cyber decisions.

Brand new research from Marsh McLennan using Bitsight data shows that many Bitsight analytics are clearly correlated with cybersecurity incidents, including the Bitsight Security Rating and 14 risk vectors.

Download our datasheet to learn more about our CRQ Enablement Services to help you calibrate cyber insurance, prioritize investment, and report to the board.

Join Bitsight’s ransomware experts and third-party risk management professionals as they discuss third-party risk management and the threat of ransomware.

The corporate attack surface is rapidly expanding: how can security professionals get ahead of the curve and create resilient organizations?