Access resources to learn about cyber risk management, security ratings and how to minimize cyber risk.
Resources.
Access resources to learn about cyber risk management, security ratings and how to minimize cyber risk.

Watch this webinar to learn how to gain visibility into what an attacker sees and take informed action to reduce exposure and empower growth and success.

Security Performance Management
The attack surface has expanded, and the number of vulnerabilities and risks has increased dramatically. Listen to the key issues and approaches to solve them.

Security Performance Management
Pedro Umbelino, Principal Security Researcher, discusses findings on BitSight-tracked organizations with internet-facing devices susceptible to compromise.
By improving their cybersecurity strategy and showcasing the effectiveness of their program, companies have a better chance to get the right cyber insurance coverage at an ideal premium.

Security Performance Management
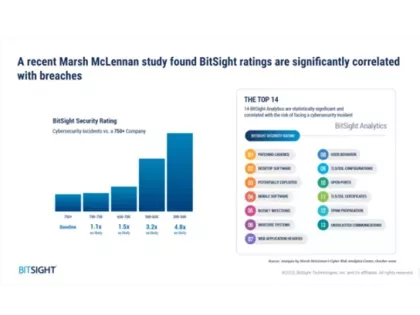
Download this webinar diving into a recent study highlighting the 14 Bitsight analytics that are significantly correlated with cybersecurity incidents.
Join Anders Norremo, VP of Product Management at Bitsight, and Ben Moreland, Managing Security Consultant at Guidepoint, to hear more about leveraging automation to manage hundreds of vendors as effectively as you manage ten.

Download now to listen to this insightful discussion on cybersecurity trends and CISO priorities.

How Rush University uses Bitsight VRM to leverage cybersecurity data to further address vendor risk across their organization. Learn more.

Security Performance Management
Watch this webinar to see how Bitsight Peer Analytics gives you the answers you need by easily comparing yourself against a meaningful group of peers.

As companies look to gain or expand their cyber coverage and negotiate premiums, they need to effectively demonstrate their risk profile to insurers.

What are the major cybersecurity trends for 2023? Download this webinar to hear insights from Moody’s analysts and Bitsight’s cyber risk experts as they discuss their latest research and look ahead to 2023.

Gain strategies to identify and overcome vendor exposure—and examples of how we’re helping customers address concentrated risk.

Security Performance Management
A study by the Marsh McLennan Cyber Risk Analytics Center found that poor performance in many Bitsight analytics is statistically significant and correlated with the likelihood of experiencing a cybersecurity incident.

Struggling to defend your organization against cyber attacks? Wondering how to prioritize limited resources?

Join Bitsight and ProcessUnity, on a journey that highlights TPRM trends, and challenges and introduces a data-driven approach through ProcessUnity that is fast, frictionless, and provides actionable integration to help modern organizations make smarter cyber decisions.