Request your free Security Rating Snapshot to find the gaps in your security program and how you compare to others in your industry.

When it comes to data breach prevention, there are plenty of guides for reducing risk in the long term. While it’s definitely valuable to be working on a data breach prevention strategy with 6-month, 1-year, or 5-year goals, not every cybersecurity initiative takes so much time.
In fact, there are steps that you can take right now to lower your organization’s risk of experiencing a data breach. Each of these steps takes less than 24 hours to complete, and each will have a positive impact on your overall cybersecurity posture.
Are you ready to reduce your risk of experiencing a data breach? Here’s what you need to do:
Close open ports.
According to research from Bitsight and Advisen, 60% of breached organizations have 10 or more ports susceptible to unauthorized use. We’ve also found that organizations with an F open port grade on our Security Ratings Platform are more than twice as likely to experience a breach than organizations with an A grade.
Closing open ports requires help from IT, but it isn’t that time-consuming. First, you have to compile a list of ports that should be open. These are determined by the systems and software on your network. Next, you need to use a tool to scan the entire network for open ports, and use administrative controls to close any ports that don’t need to be open. This article runs through the entire process in detail.
Run necessary updates.
We’re all guilty of ignoring the notifications on our workstations and mobile devices telling us it's time to update. However, when this becomes an organization-wide issue, it can lead to increased vulnerability for your systems and data.
Updates are important because hardware manufacturers and software developers will often roll out security patches alongside other performance and UX changes. These security patches might protect against new malware types or fix newly discovered vulnerabilities, helping to keep your systems safe. However, if the updates aren’t installed, your organization could fall victim to entirely preventable cyber attacks.
Every internet-connected device and software system on your network should be updated regularly. In the future, you can implement a regular patching cadence to ensure all devices and programs are up-to-date. For now, start with the devices and software that are most likely to be targeted in an attack. These include:
-
Router firmware
-
Web browsers
-
Operating systems
Implement multi-factor authentication.
Multi-factor authentication (also called two-factor authentication or 2FA) is perhaps the least-loved cybersecurity best practice. Yes, it’s a hassle to have to enter a code to log into systems and software platforms, however, it makes your accounts exponentially more secure.
The use of stolen credentials was the number one action variety in data breaches in 2017. Adding a second layer of security beyond username/password is a no-brainer for organizations with any amount of sensitive data. It makes it twice as hard to break in.
Best of all, it’s pretty much free. Most online platforms and cloud-based tools (Dropbox, Slack, Google, Microsoft, etc.) allow you to enable multi-factor authentication right from the settings. For proprietary systems, you have the option of either using SMS or app-based 2FA, or a physical authenticator keychain. The latter is more expensive and will take more time to implement, but adds an extra dose of security.
Check your security rating.
Cybersecurity performance audits are integral to the development of solid data breach prevention plans. However, audits take time, and depending on the resources you have available, might require you to hire a costly third party.
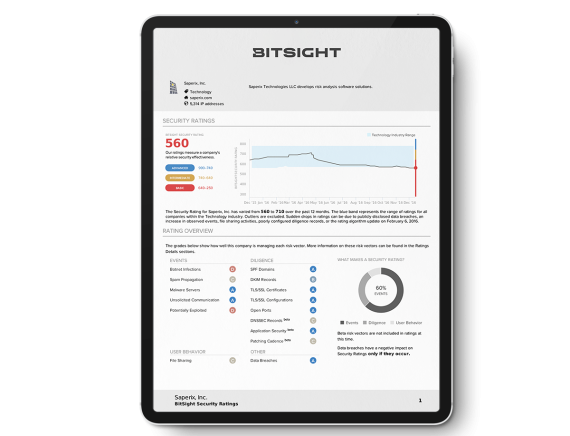
In the meantime, you can gain an up-to-date, objective perspective on your cybersecurity performance by requesting your Security Rating Snapshot report. Bitsight Security Ratings compile externally observable data from a range of trustworthy sources to show you how vulnerable your organization is. These ratings have been proven to correlate with risk of data breach. Read everything you need to know about security ratings here.
In addition to an overall rating, the Bitsight Security Ratings Platform will show you your performance in a number of specific risk areas, like malware servers, peer-to-peer file sharing activity, TLS/SSL configuration, etc. You can use your ratings in these areas to quickly identify the steps you should take next.
[Want to know what your security rating is? Request a Security Rating Snapshot report now.]
Request your Security Rating Snapshot report to find out how secure your organization really is
Request your Security Rating Snapshot report to find out how secure your organization really is
Address peer-to-peer file sharing.
One of the risk vectors revealed through the Bitsight Security Ratings Platform is peer-to-peer (P2P) file sharing activity. If you have a low grade in this area, that means people are using your network for P2P sharing, which can be very dangerous.
While P2P sharing isn’t illicit in itself, the files sent along P2P protocols often are. Our research found that 43% of applications and 39% of games shared via peer-to-peer protocols contained some form of malicious software. For this reason, a low P2P rating could indicate an increased risk of malware infection, and by extension, data breach.
What can you do today to prevent this activity? You can block certain well-known torrent trackers and other P2P-related sites on your network. While that won’t stop the most determined P2P users, it might act as a deterrent, and is generally a good idea.
What might be even more effective is issuing an alert to your employees that torrenting at work is against company policy and will result in serious consequences. After all, most people would rather keep their jobs than download some free software.
Backup your files.
This advice has been floating around since the dawn of digital storage, but in the age of cloud computing, many of us take backups for granted.
In many cyber attacks, files are completely destroyed or corrupted. Take the NotPetya “ransomware” attacks, which prompted users to pay a bitcoin ransom to decrypt sensitive data. Even those users who paid the price quickly found that their data was corrupted beyond recovery.
While many cloud services providers have state-of-the-art data breach prevention systems and backup across different locations, they are by no means impervious to cyber attacks. If you have sensitive data stored in the cloud, it’s wise to consider backing it up to physical drives, and vice versa.
Lock up your drives.
Speaking of physical drives, one of the most overlooked causes of data breach is physical theft. Stolen laptops, hard drives, USB drives, and other data-containing devices represent a cyber risk that you don’t need any cybersecurity expertise to mitigate.
Make sure any devices containing sensitive data are stored in locked safes or behind locked doors. Never store backups in the same locations as the originals. If employees are traveling with work devices, make sure they have software installed that enables them to remotely wipe drives in case of theft.
Secure your Wi-Fi.
Wi-Fi vulnerabilities can give cyber criminals incredible amounts of access to your sensitive files and systems. By exploiting certain vulnerabilities in Wi-Fi networks, hackers have been able to build backdoors into all devices connected to those networks, including computers and smartphones.
There are steps you can take right now to protect your Wi-Fi network from bad actors, including setting a strong password, installing encryption software, updating router firmware, and isolating guest networks from internal ones. Read more about securing Wi-Fi networks here.
Conclusion
You don’t have to wait to protect your organization from data breach. While it will take time, money, and energy to implement a truly robust data breach prevention strategy, there are steps you can take right now that will make your company more secure.