New! The Security Ratings report is now the Executive Report. Request your report to see enhanced analysis such as your rating, likelihood of ransomware incidents, and likelihood of data breach incidents.

As the number and costs of cyber-attacks and data breaches continue to rise, more money is being thrown at the problem. IDC projects that by 2022, organizations will spend $133.8 billion to protect their IT infrastructures against cybersecurity threats.
With this much money being spent, organizations may want to target their efforts as efficiently as possible. Here are three critical areas that represent the most frequent and emerging causes of data breaches, with suggestions on steps you can take to prevent them--without breaking the bank.
1. Flawed cloud configurations
As more data is moved to the cloud, hardly a day goes by when a security incident involving misconfigured cloud storage configurations doesn’t make the headlines. Indeed, the cloud systems of Verizon, GoDaddy, the U.S. Department of Defense, and Capital One have all been compromised in recent years, leading to the breach of millions of customer records
But as we wrote previously, when discussing lessons learned from the Capital One data breach, such incidents are entirely preventable – if cloud users observe the cloud shared responsibility model. That model, stipulated in all cloud service agreements, makes it clear that cloud service providers (CSPs) are responsible for the security of their cloud infrastructure, while customers are responsible for security in the cloud – such as patches and updates, configuration and management tasks, and managing data.
Yet, only 10% of CISOs report that they fully understand the shared responsibility model, and 82% have experienced security incidents due to confusion over who has responsibility for what in the cloud. This can lead to misconfigurations or the mistaken belief that executives aren’t liable for losses as a result of a cloud breach.
Read more about how you can ensure your cloud data is protected, without overwhelming security teams with alerts and actions.
2. Vulnerable third parties
A study by Opus and Ponemon Institute found that third parties are one of the fastest growing risks to an organization’s sensitive data. Indeed, 59% of companies having experienced a third-party data breach.
Third-party risk management, however, can be extraordinarily challenging, since our vendor networks are growing at an exponential pace. Today, 60% of organizations work with more than 1,000 third parties. Unsurprisingly, only 16% say they take steps to effectively mitigate risk in their vendor ecosystems.
How secure is your organization?
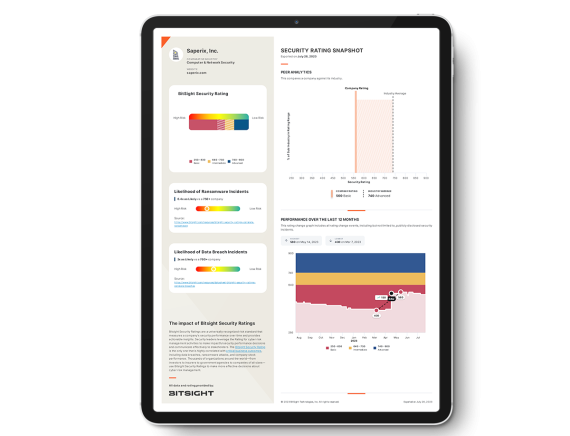
How secure is your organization?
The problem is that the tracking and management of vendor portfolios (including maintaining a record of the results of security audits and questionnaires) often falls to one person with a spreadsheet. If that person leaves, that spreadsheet essentially leaves with them. Without this single source of truth, organizations can quickly become vulnerable to potential security flaws in their vendor networks.
A better approach is to ditch this manual and siloed approach to third-party risk management and replace it with a robust program that incorporates processes, procedures, and technologies for assessing, monitoring, and mitigating vendor cyber risk. One that delivers a heightened level of visibility into the riskiest cyber issues impacting your vendors on a continuous basis and triggers automatic alerts when a vendor’s risk posture changes.
3. Unprotected code repositories
Code and asset repositories, such as GitHub, Docker Hub, and Bitbucket, represent another growing source for data breaches. These cloud-based repositories or file archives are used by application development teams to host source code for software, images, and web pages, and form an essential part of the open source software development process.
Unfortunately, these third-party sites can quickly become your weakest security links. As the recent breach of Docker Hub shows, when a repository is compromised, it’s not what is breached--it’s the scale of the breach.
When code repositories are hacked, thousands of logs, user tokens, and hashed passwords are up for grabs. With the vast amount of code stored in these repositories, hackers have plenty of places to insert malicious code. That code can then be downloaded by other users, infecting their networks and interconnected projects.
Remediation is often the only remedy. This involves combing through your code repositories and autobuilds, looking for suspicious activity in your accounts and projects, and then re-securing them--a time-consuming task that delays the application development pipeline, and has downstream effects on the business.
Much of the risk associated with unprotected code repositories can be mitigated in the first place by treating these code repositories as you would any vendor--by implementing a robust a third-party risk management program. This will enable you to understand the risk posed by these vendors so that you can put measures in place to mitigate the chances of a security incident. Read more about preventing data breaches associated with unprotected code repositories.
Make knowledge your first line of defense against data breaches
Much time and money is invested in technology tools that aid in the detection and protection against these top threats. These tools have their place. But understanding how, why, and where these threats have their genesis is also a vital first line of defense that can significantly improve the effectiveness of your investments without over-taxing security teams.