Get the full lay of the land with Bitsight’s External Attack Surface Management (EASM) capabilities. See what you’re up against across the expanding attack surface. Prioritize what matters most. And mitigate where you’re most vulnerable.
Get the full lay of the land with Bitsight’s External Attack Surface Management (EASM) capabilities. See what you’re up against across the expanding attack surface. Prioritize what matters most. And mitigate where you’re most vulnerable.
See what an attacker sees.
See what an attacker sees.
Your attack surface may be quickly expanding, but that doesn’t mean your exposure has to. Security leaders harness the power of Bitsight’s EASM capabilities to keep track of countless digital assets - like operational technology (OT) and cloud infrastructure - at any given moment.
Know that your attack surface is covered.
Fix immediate exposure issues while keeping an eye on what’s new in your company. And get to the root cause of issues so you don’t see repeat problems. Now that’s long-term success.

With hundreds of thousands of assets on the internet and cloud instances being spun up every day, we needed visibility into where cybersecurity falls short—and Bitsight delivers that. You can't reduce the cyber risks faced by your organization if you don't know what you're up against—both internally and across your vendor portfolio.
Holistic external attack surface management—at scale.
Map your company
Map your company
Discover & classify your assets.
Take stock of your cyber assets and know how they impact you—with your organization mapped from day one. See your digital footprint from a 10,000-foot view, down to individual details of each asset.
- Continuously monitor assets to see what’s changing and where you might be exposed
- See your digital footprint based on the combination of automation and human annotation
- Built on Bitsight’s 9 patents of attributing infrastructure.
See your exposure
See your exposure
Analyze your exposure.
See your attack surface the way an attacker does—where you’re most exposed and vulnerable. Build your view based on exposure data from vulnerabilities, operational technology (OT), user behavior, compromised systems, public disclosures, and configurations across email, software, and the web.
- Gather insights on your entire infrastructure—with minimal work
- Drill-down into areas that matter most to you, like subsidiary, geography, or technology.
- See what’s lurking in shadow IT
Respond to vulnerabilities
Respond to vulnerabilities
Respond quickly to vulnerabilities.
There are thousands of known vulnerabilities in the world. Make sure you’re protected from them. Get a full view of your exposure across the extended enterprise when a new vulnerability pops up.
- Quickly understand your external exposure
- Prioritize vulnerabilities based on how severe they are
- Focus resources on what matters most
Remediate problems
Remediate problems
Get to the root cause.
Stop fixing the same findings over and over again. Continuously assess how effective your security controls are to get better at preventing cyber attacks and scaling efforts.
- Set processes that can scale with your team
- See how your controls are working so you don’t keep experiencing the same problems over again.
- Prioritize and communicate performance to stakeholders
See our certified EASM partners
Integrate with workflow tools to assign and track remediation across teams and report on insights.
Extend EASM capabilities to your third-party network.
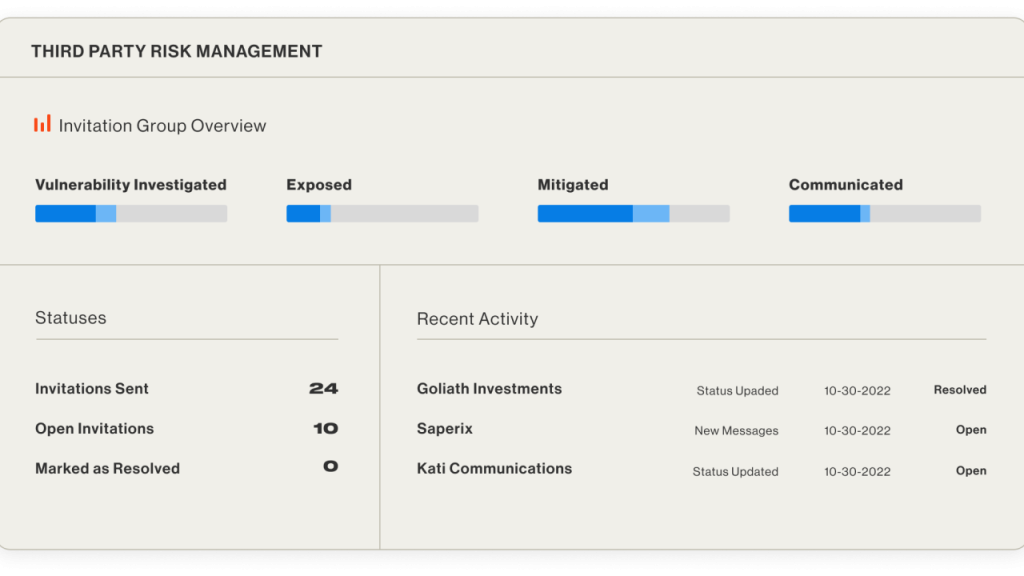
Extend EASM capabilities to your third-party network.
Work with vendors without working with their vulnerabilities. Use the same detailed attack surface data you have on your own ecosystem and share it with critical vendors to expedite remediation of their vulnerable areas.
External Attack Surface Management
Resources

Data Sheets
Bitsight External Attack Surface Management (Data Sheet)
Reports and Research




